Weekly web attack trends
Weekly web attack trends allow you to see when web attacks are most prevalent. This can help you plan ahead to prevent and respond to web attacks during peak periods.
The graph below shows the web attacks detected by AIWAF as of October 2024.
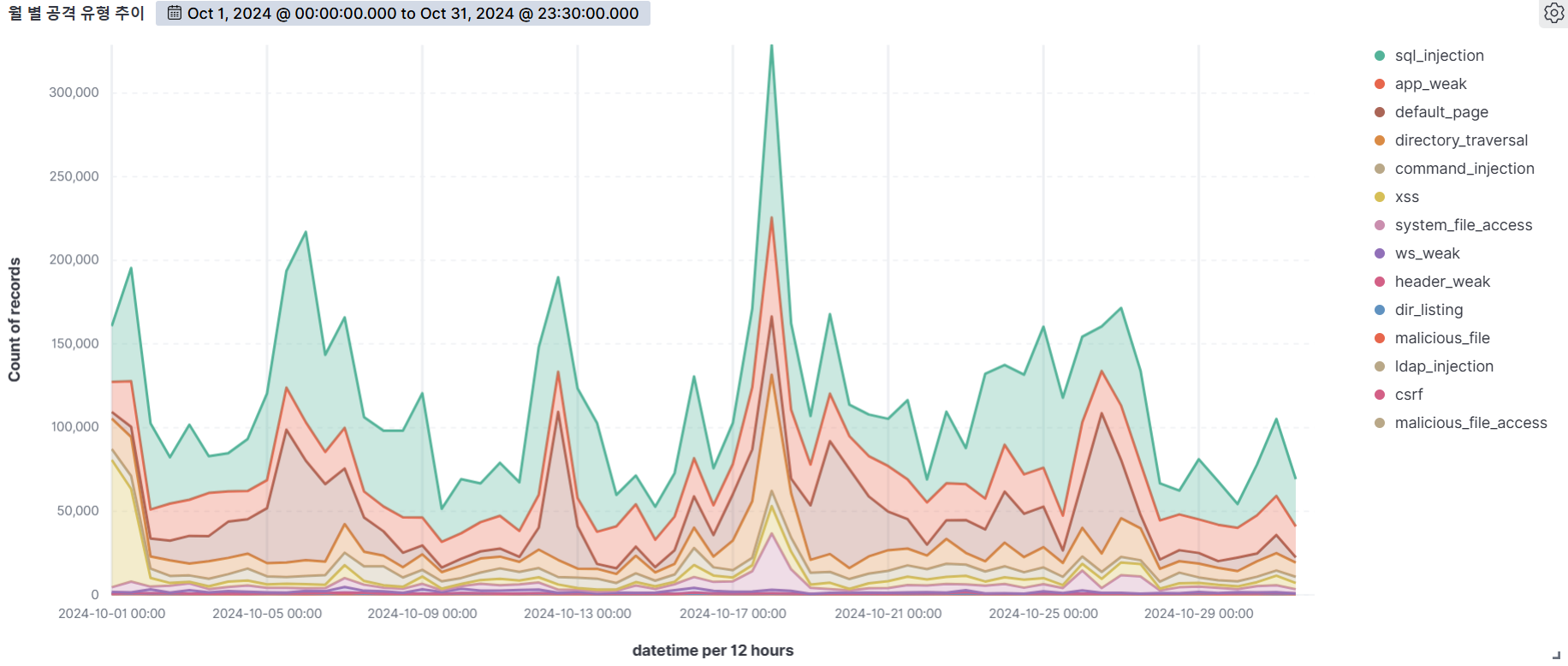
In October 2024, we detected over 230,000 attacks per day on average, with the highest number of attacks occurring on a single day.
SQL Injection, the vulnerability with the most attacks attempted on 18 days, has the most detection conditions in our AIWAF. However, SQL Injection attacks are always being monitored because there are many new attack types and evasion methods.
Web attack trends by attack type
Web attack trends by attack type, based on detection logs, allow you to see which attacks were most prevalent during the month. Based on this, you can establish basic web attack response guidelines to prevent and respond to these types of attacks.
The graph below shows the web attacks detected by AIWAF as of October 2024.
Web Attack Trends by Rule
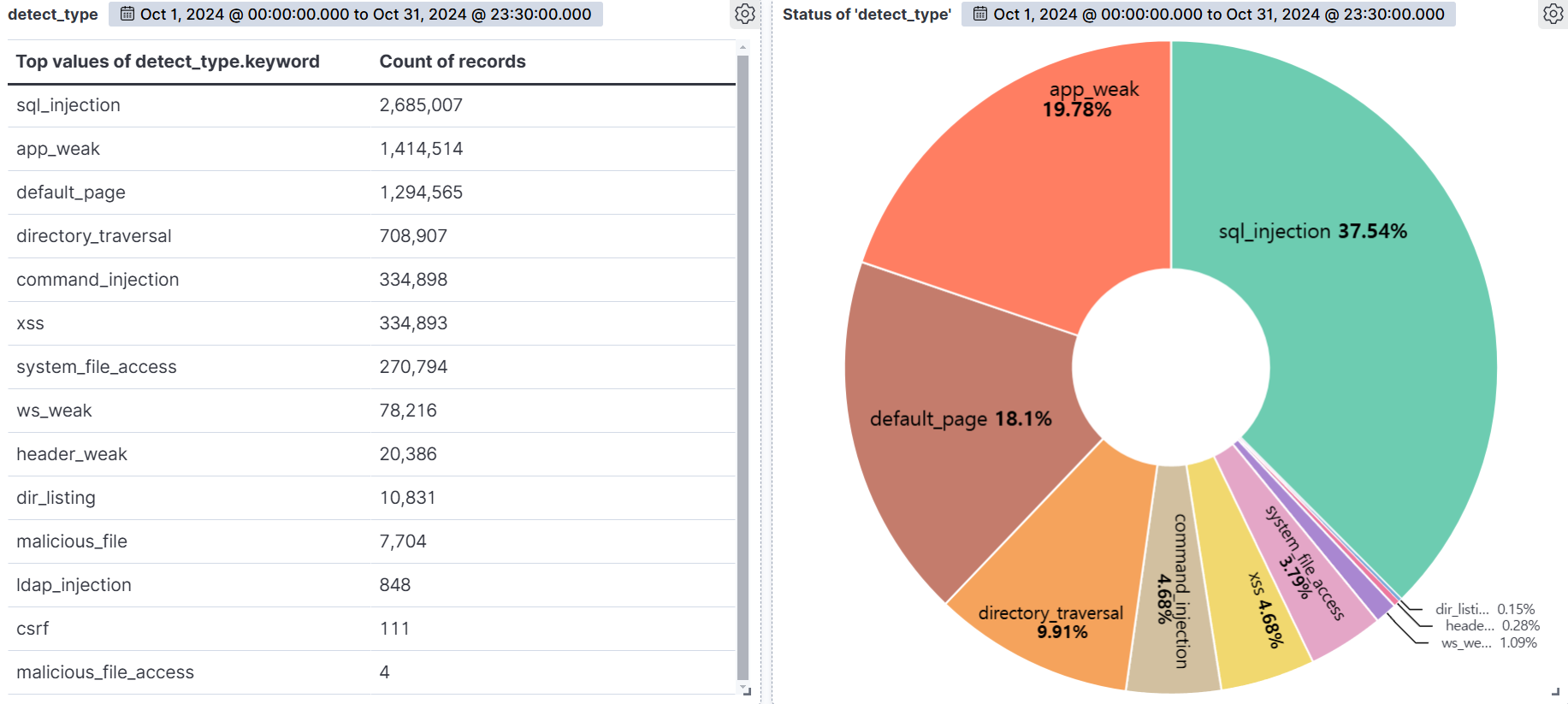
SQL Injection (37.54%) was the most common attack type detected, followed by App Weak (19.78%), Default Page (18.1%), and Directory Traversal (9.91%).
SQL Injection is the most diverse and dangerous attack, as it is ranked #1 by OWASP. It is an attack that forces malicious SQL statements into SQL statements that dynamically generate data based on user requests, which can cause vulnerable applications to authenticate or return abnormal SQL results. If you see the following syntax in your query values, you should suspect an attack.
App Weak refers to vulnerabilities within an app that can be exploited by an attacker to gain unauthorized access or perform malicious actions. These vulnerabilities can be the result of poor coding practices, misconfiguration, or insufficient security measures. As a general rule of thumb, be suspicious of unauthorized files in addition to authorized files when using app programs.
Summary of web attack trend graphs for the last 3 months
July
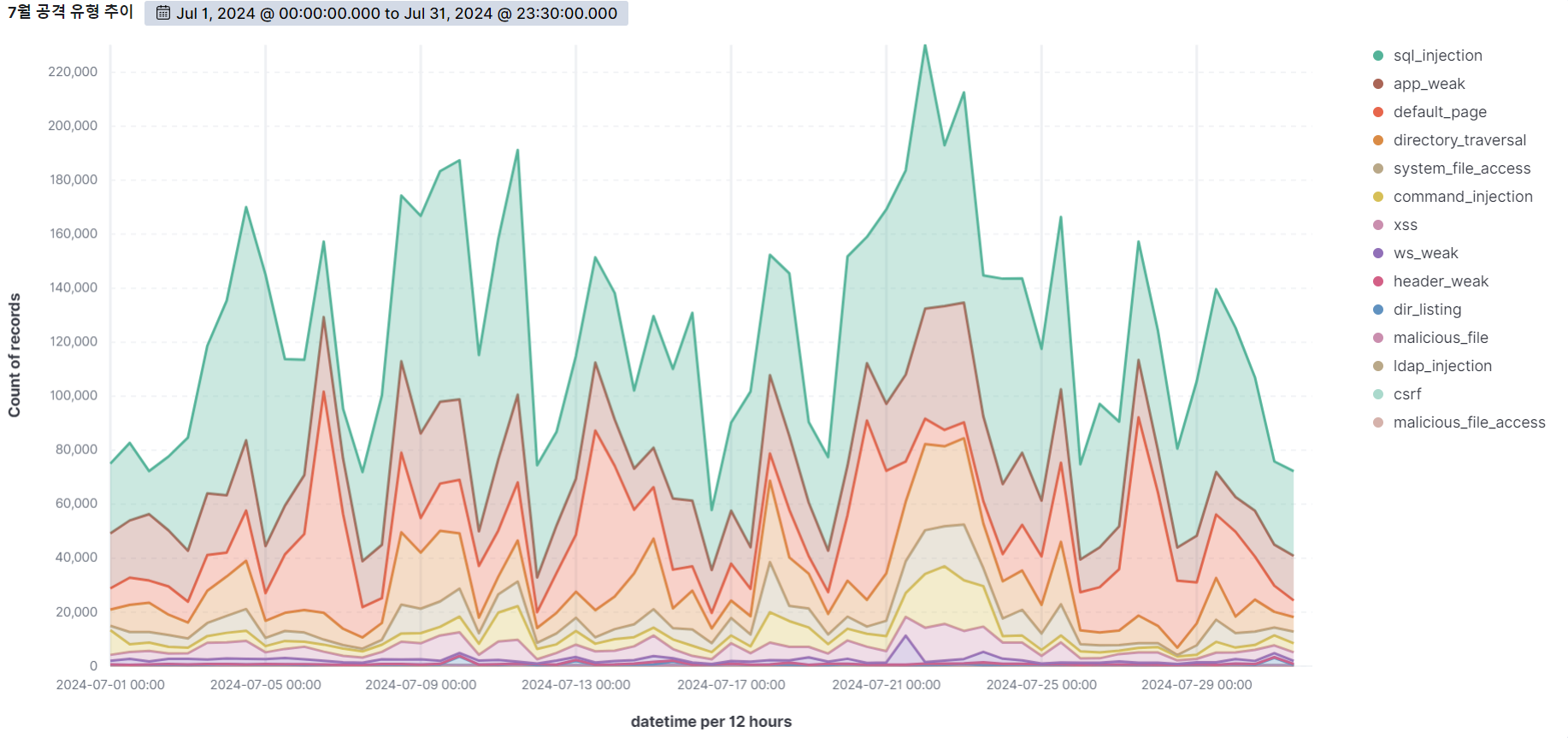
August
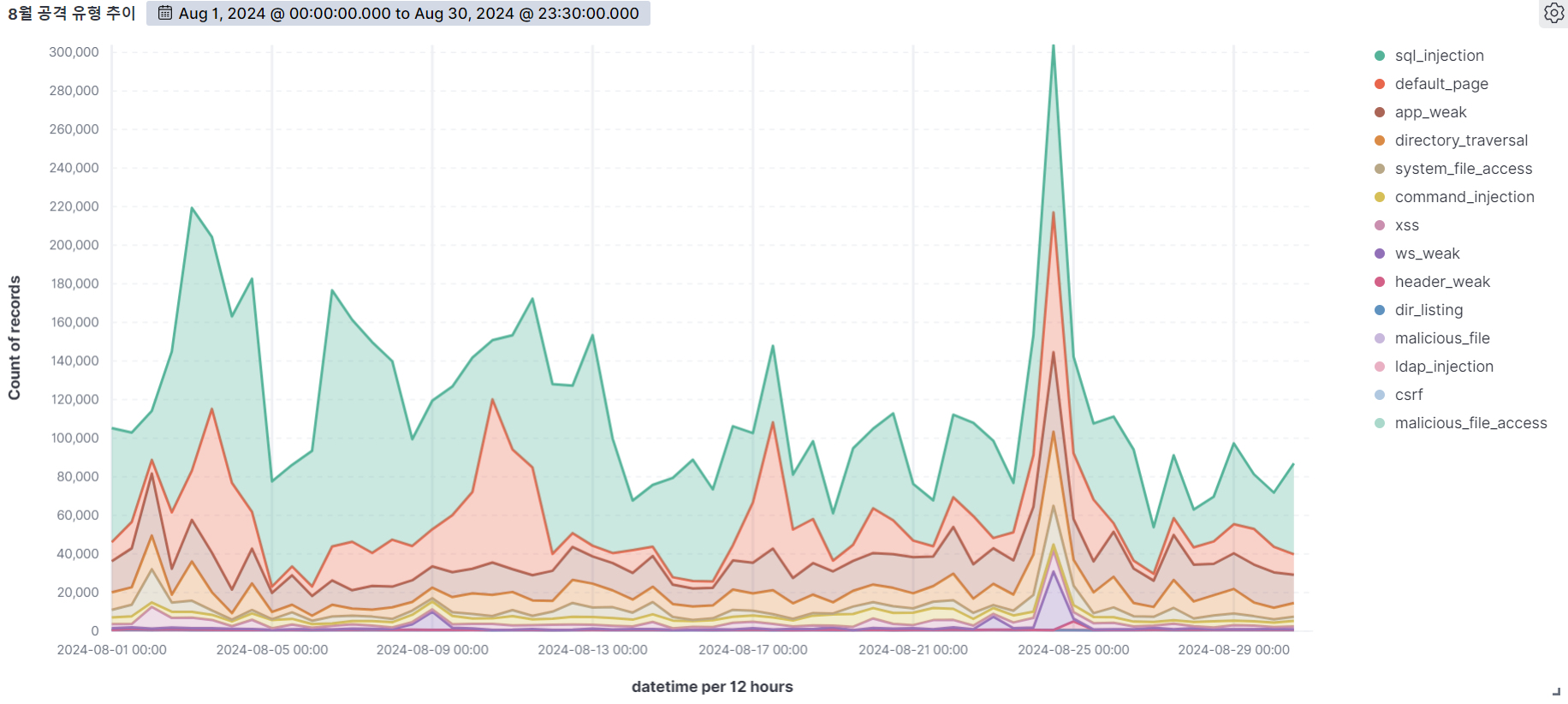
September
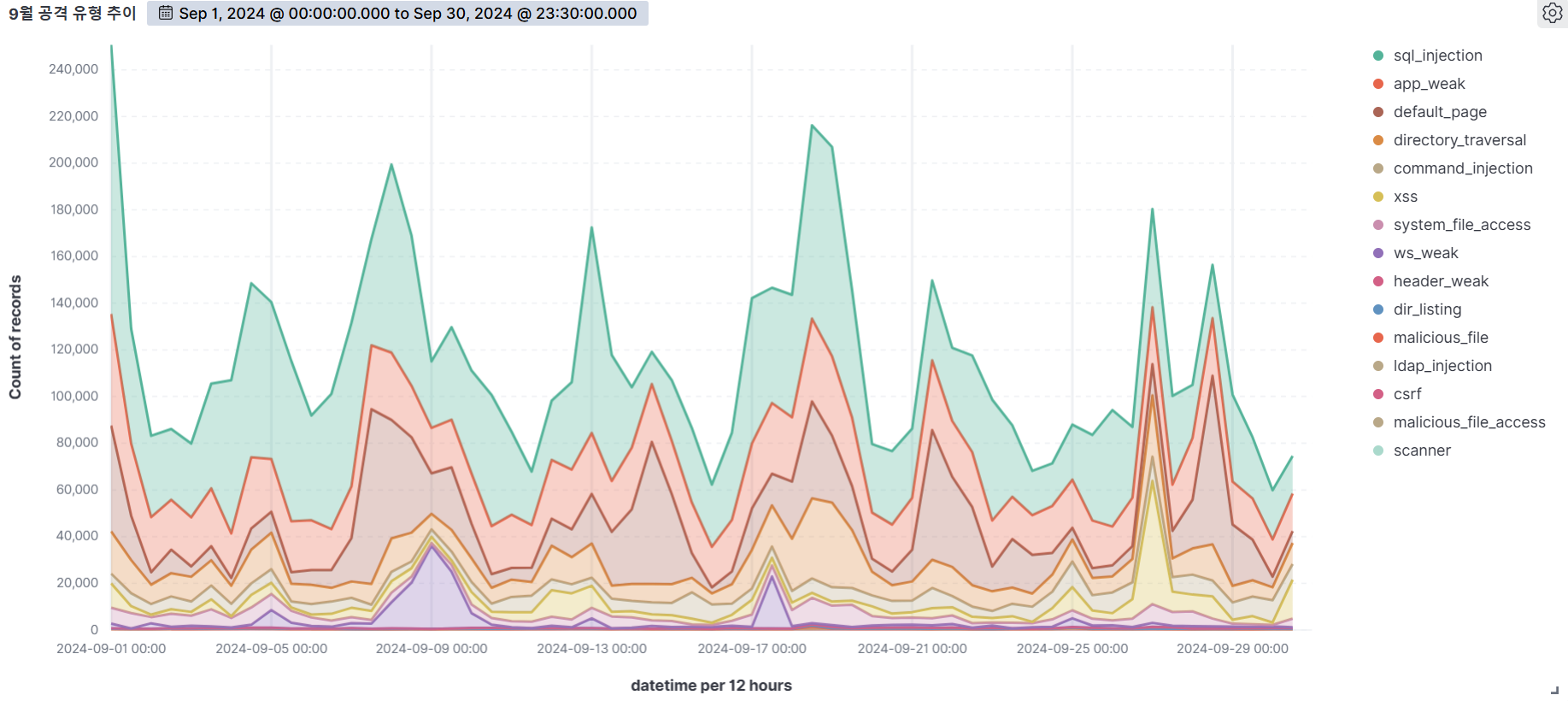
Top 30 Attacker IPs

Vulnerability analysis reports
[Github Enterprise Server Authentication Bypass]
1. Overview
Github, a service that provides hosting capabilities for Git, a distributed version control tool, has published an analysis of CVE-2024-4985 and CVE-2024-9487, authentication bypass vulnerabilities in Github Enterprise Server (GHES), the service's paid plan.

Source : https://projectdiscovery.io/blog/github-enterprise-saml-authentication-bypass
2. Attack types
Github Enterprise Server (GHES) uses SAML SSO authentication and the cryptographic assertion feature for the authentication process. The cryptographic assertion feature is disabled by default, but GHES with it enabled is affected by this vulnerability.
In GHES with the encrypted assertion feature enabled, the authentication process checks whether there is a signature outside the assertion block, and whether the identity of the entire signature and parent assertion in the block match to prevent an attacker from manipulating the signature to insert a malicious assertion.
However, the verification process does not verify the assertion signature itself, which could allow an attacker to bypass the verification process by obtaining a valid SAMLResponse from the IDP and appending a fake assertion node to that SAML to fake the presence of an encrypted assertion signature, thus gaining access to a GHES arbitrary account.
SAML data written to an arbitrary GHES URL (https://your-ghes-instance.com) :
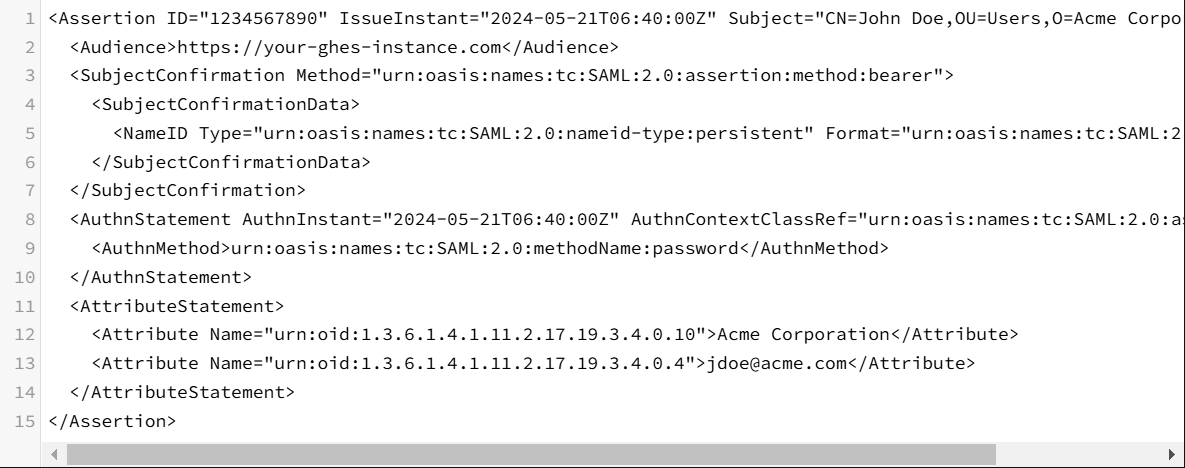
Nuclei Template-Based Attacks Request :
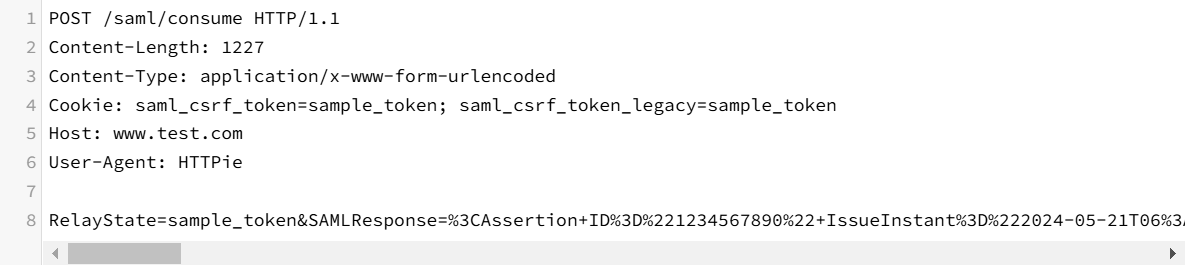
3. What to do
The vulnerability was fixed in GHES versions 3.9.15, 3.10.12, 3.11.10, and 3.12.4 with CVE-2024-4985 upon initial disclosure, but was found to be incompletely addressed in a fix patch and was fixed again in GHES versions 3.11.16, 3.12.10, 3.13.5, and 3.14.2 with CVE-2024-9487.
The vulnerability bypasses the validation step by injecting a crafted, fake assertion node, and is not considered a patternable area as AIWAF is likely to detect legitimate requests when responding with patterns.
4. Conclusion
Github Enterprise Server is a hosted service on the Github platform and is used by many customers and organizations, so an authentication bypass vulnerability in this service is a high impact and high impact vulnerability, and organizations and customers using Github Enterprise Server should ensure that they are always patched to the latest version.
Our AIWAF products continue to monitor Github and Github Enterprise Server for vulnerabilities, and we will continue to respond to relevant vulnerabilities as they are discovered.
5. References
https://projectdiscovery.io/blog/github-enterprise-saml-authentication-bypass
https://github.com/absholi7ly/Bypass-authentication-GitHub-Enterprise-Server
https://hawk-eye.io/2024/10/cve-2024-9487-critical-vulnerability-affecting-github-enterprise-server/
Latest vulnerability CVE status
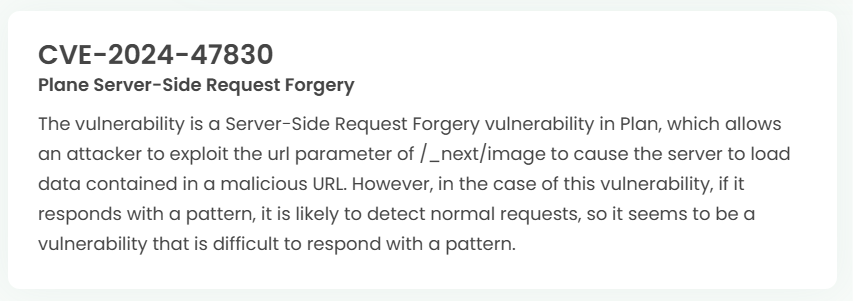
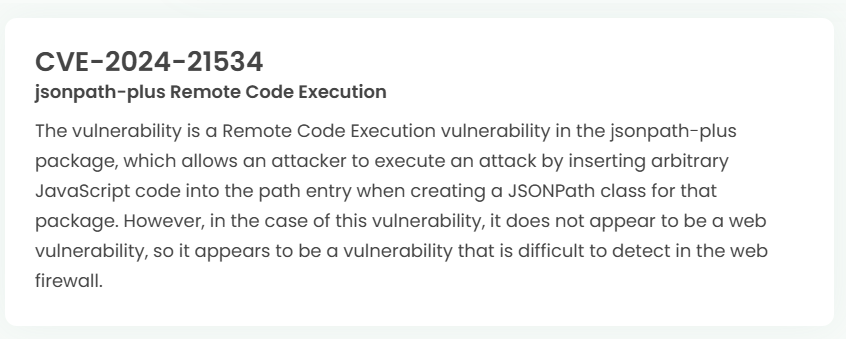
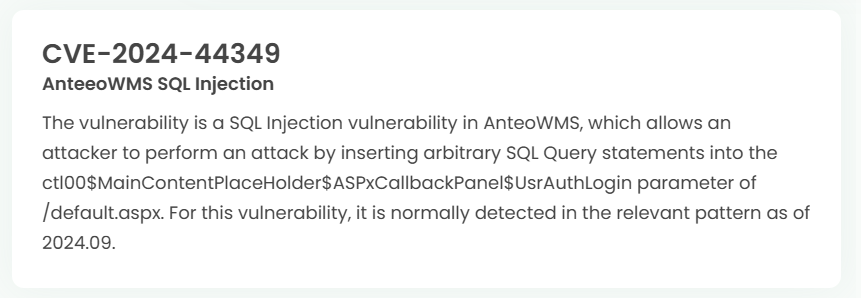
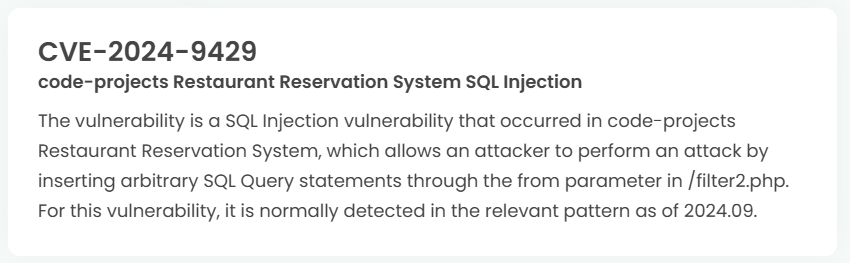
1. High-risk vulnerability status (2024.10)
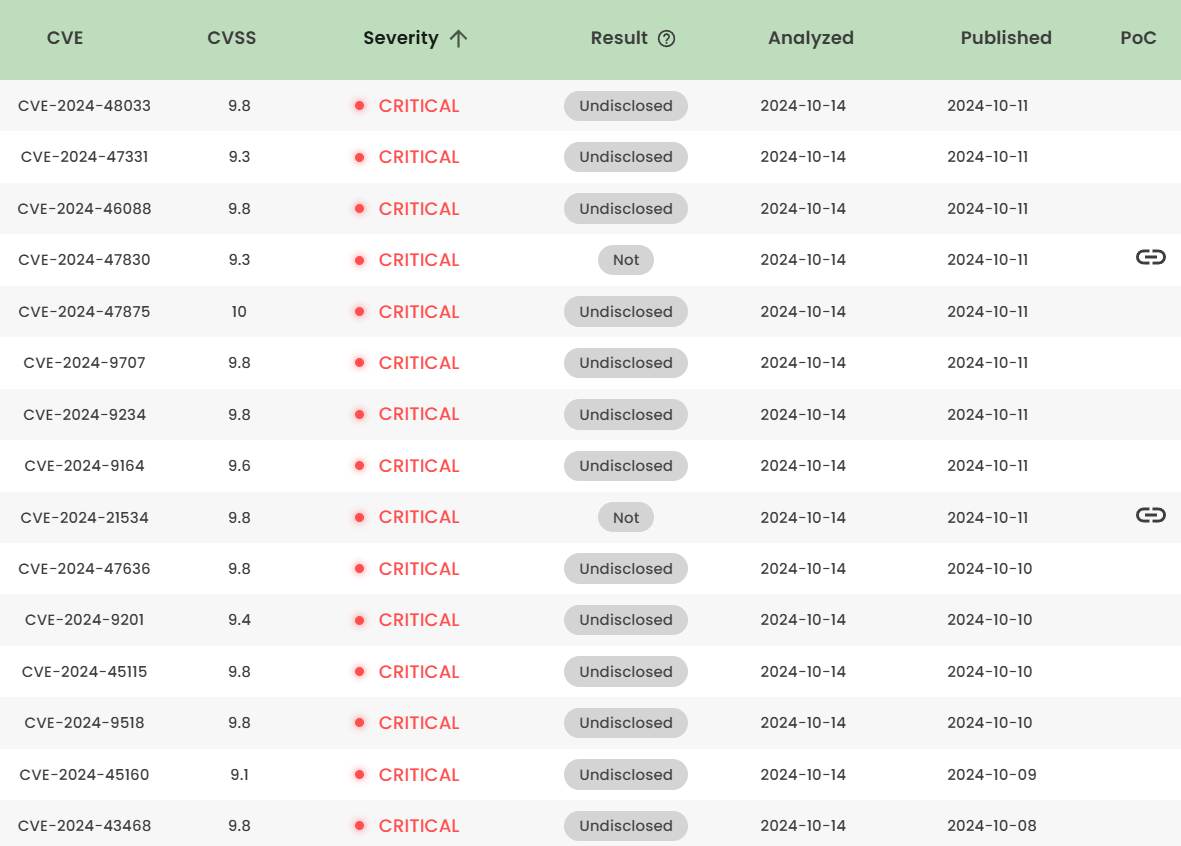
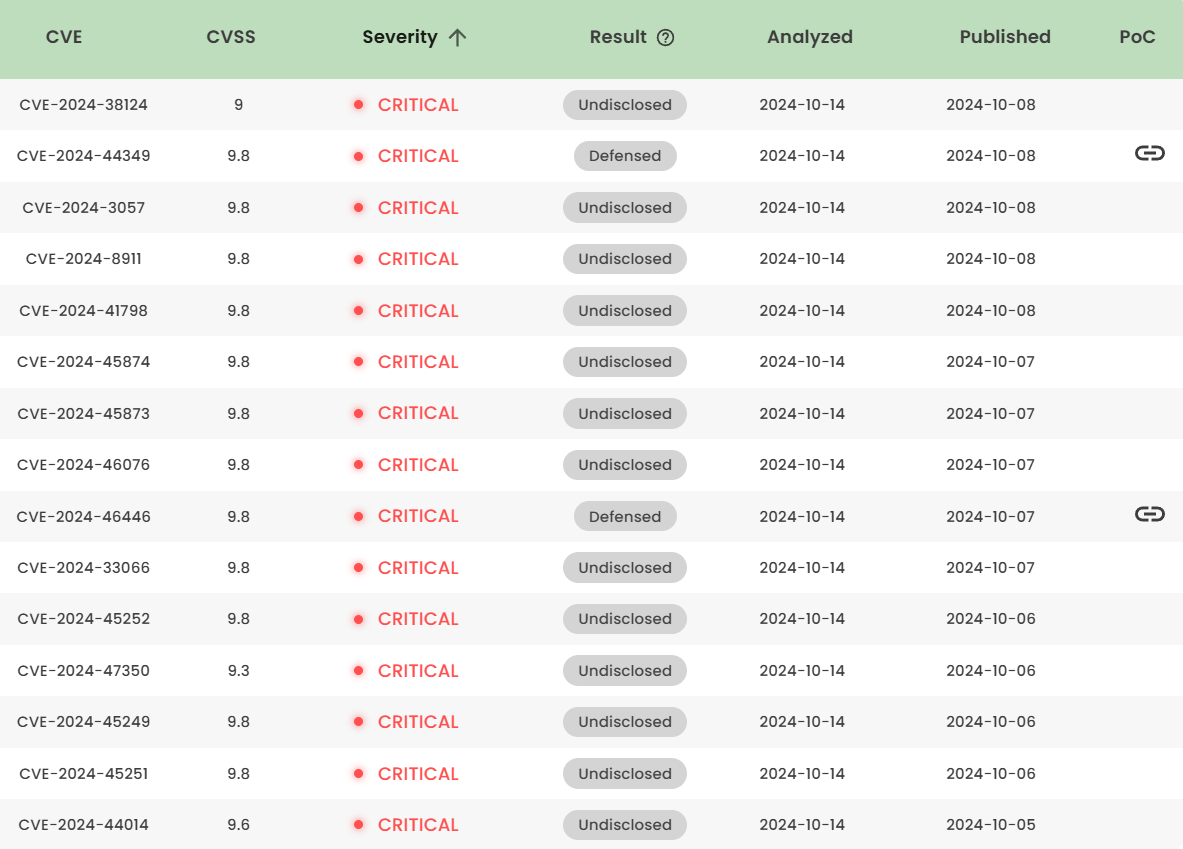
2. High-risk vulnerability descriptions