Weekly web attack trends
Weekly web attack trends allow you to see when web attacks are most prevalent. This can help you plan ahead to prevent and respond to web attacks during peak periods.
The graph below shows the web attacks detected by AIWAF as of February 2025.
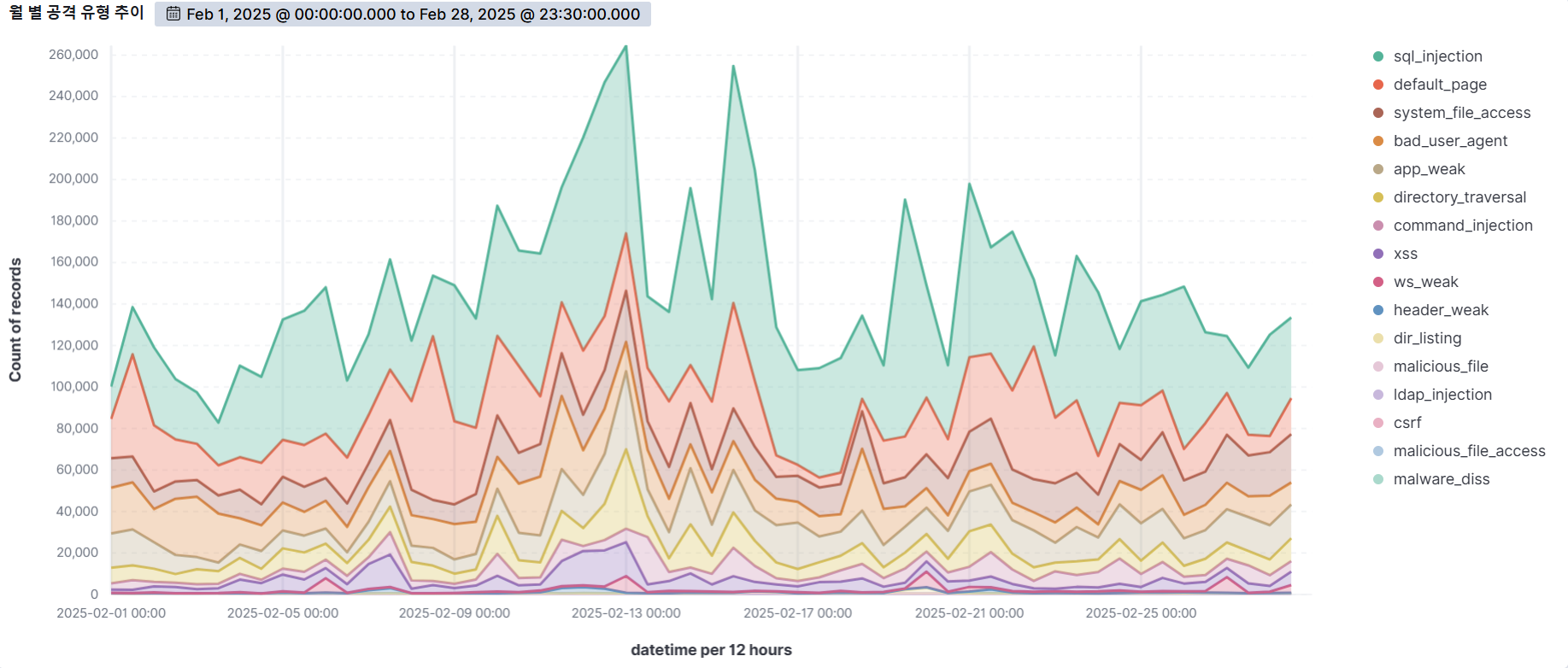
In February 2025, we detected an average of about 270,000+ attacks per day, with the highest number of attacks occurring on the 28th and 30th.
SQL Injection, the vulnerability with the most attempted attacks on the 13th, has the most detection conditions in our AIWAF. However, SQL Injection attacks are always being monitored because there are many new attack types and circumvention methods.
Web attack trends by attack type
Web attack trends by attack type, based on detection logs, allow you to see which attacks were most prevalent during the month. Based on this, you can establish basic web attack response guidelines to prevent and respond to these types of attacks.
The graph below shows the web attacks detected by AIWAF as of February 2025.
Web Attack Trends by Rule
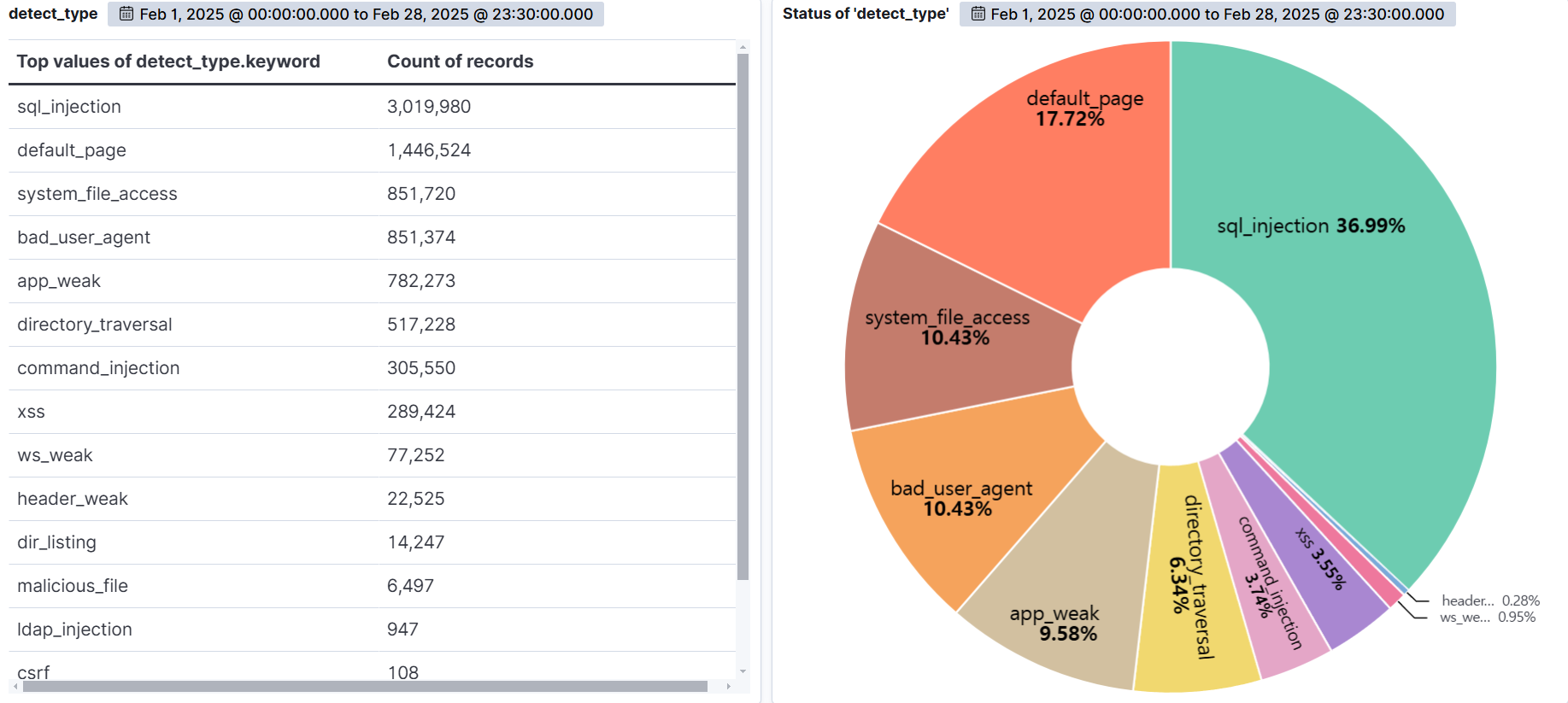
SQL Injection (36.99%) was the most common attack type, followed by App weak (17.72%), Default page (10.43%), and bad user agent (10.43%).
SQL Injection is the most diverse and dangerous attack, as it is ranked #1 by OWASP. It is an attack that forces malicious SQL statements into SQL statements that dynamically generate data based on user requests, which can cause vulnerable applications to authenticate or return abnormal SQL results. If you encounter the following syntax in your query values, you should suspect an attack.
APP WEAK indicates a vulnerability within an app that an attacker can exploit to gain unauthorized access or perform malicious actions. These vulnerabilities can be the result of poor coding practices, misconfiguration, or insufficient security measures. As a general rule of thumb, be suspicious of unauthorized files in addition to authorized files when using app programs.
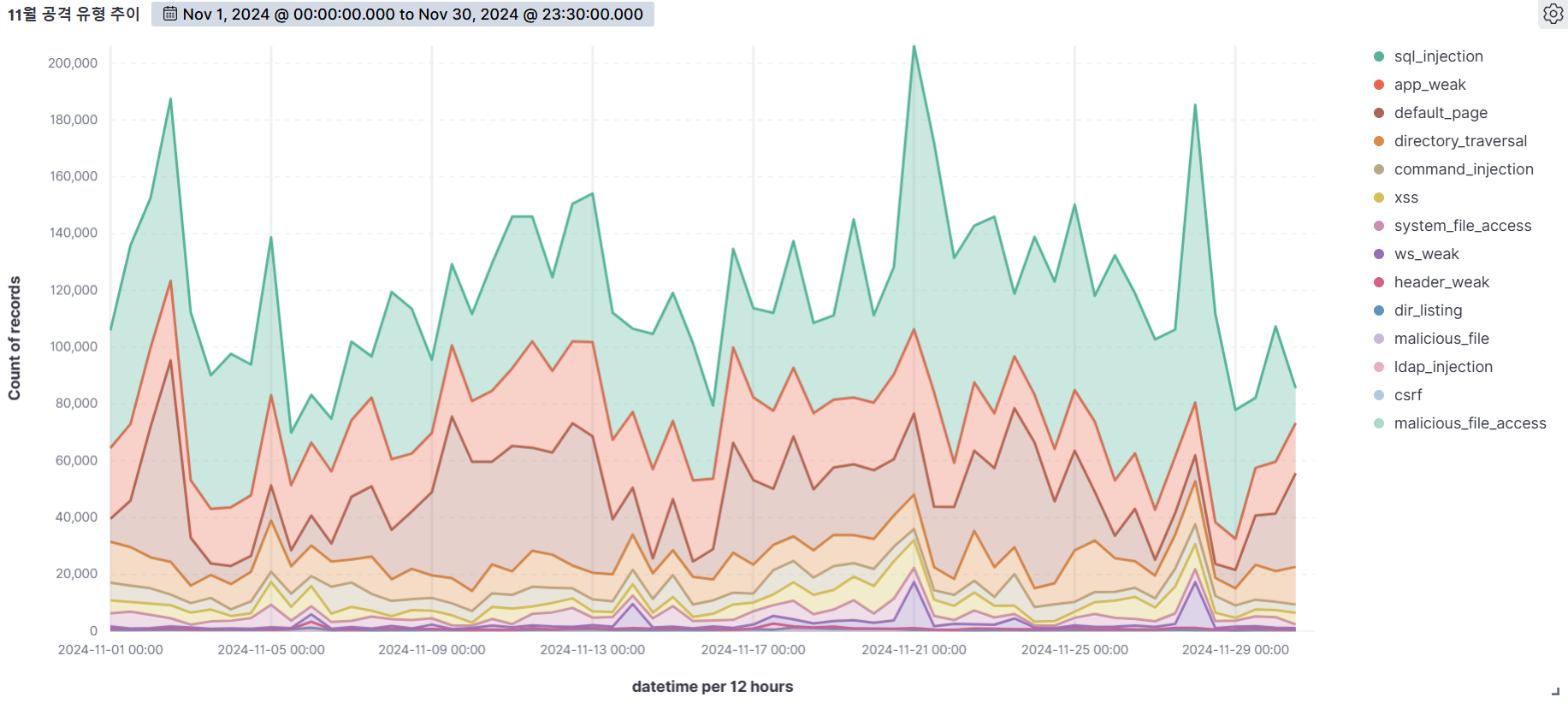
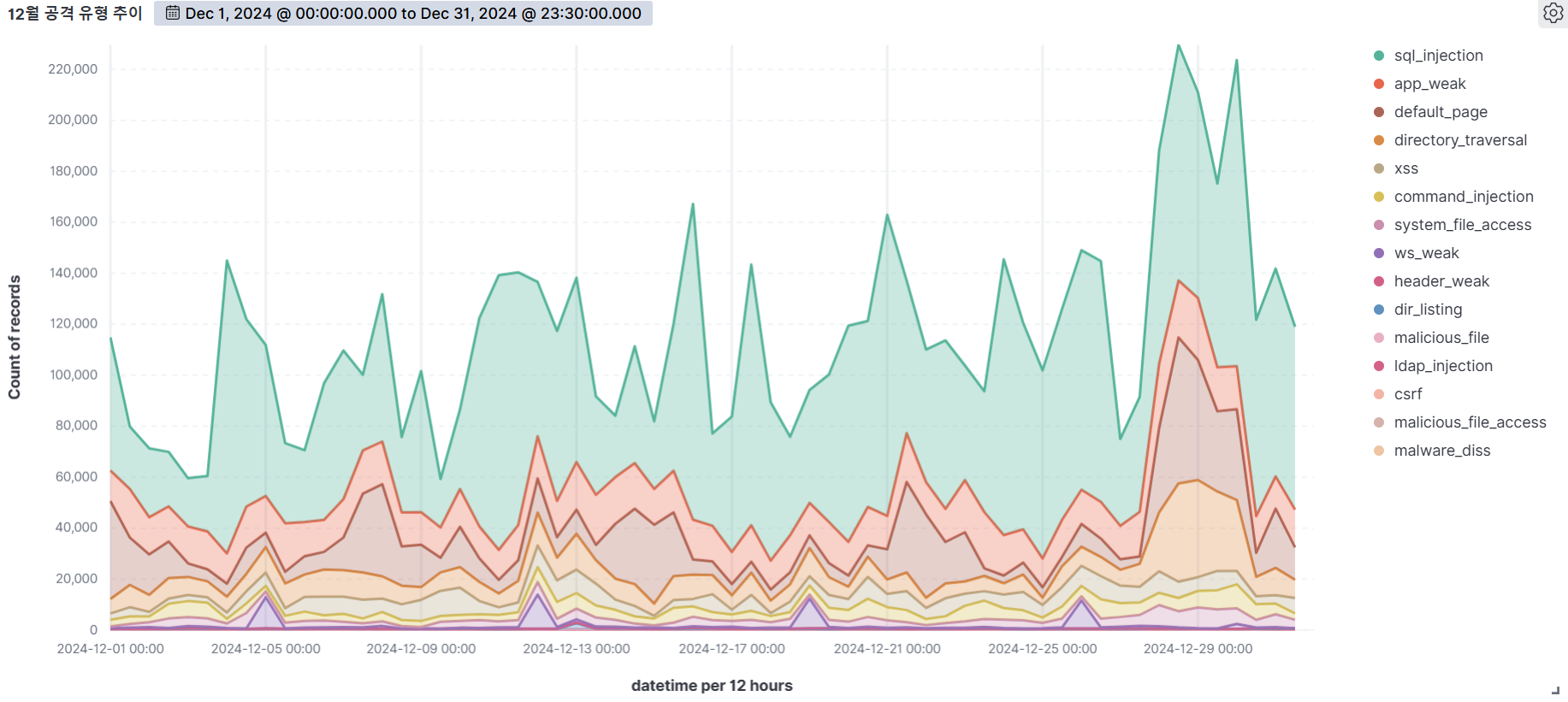
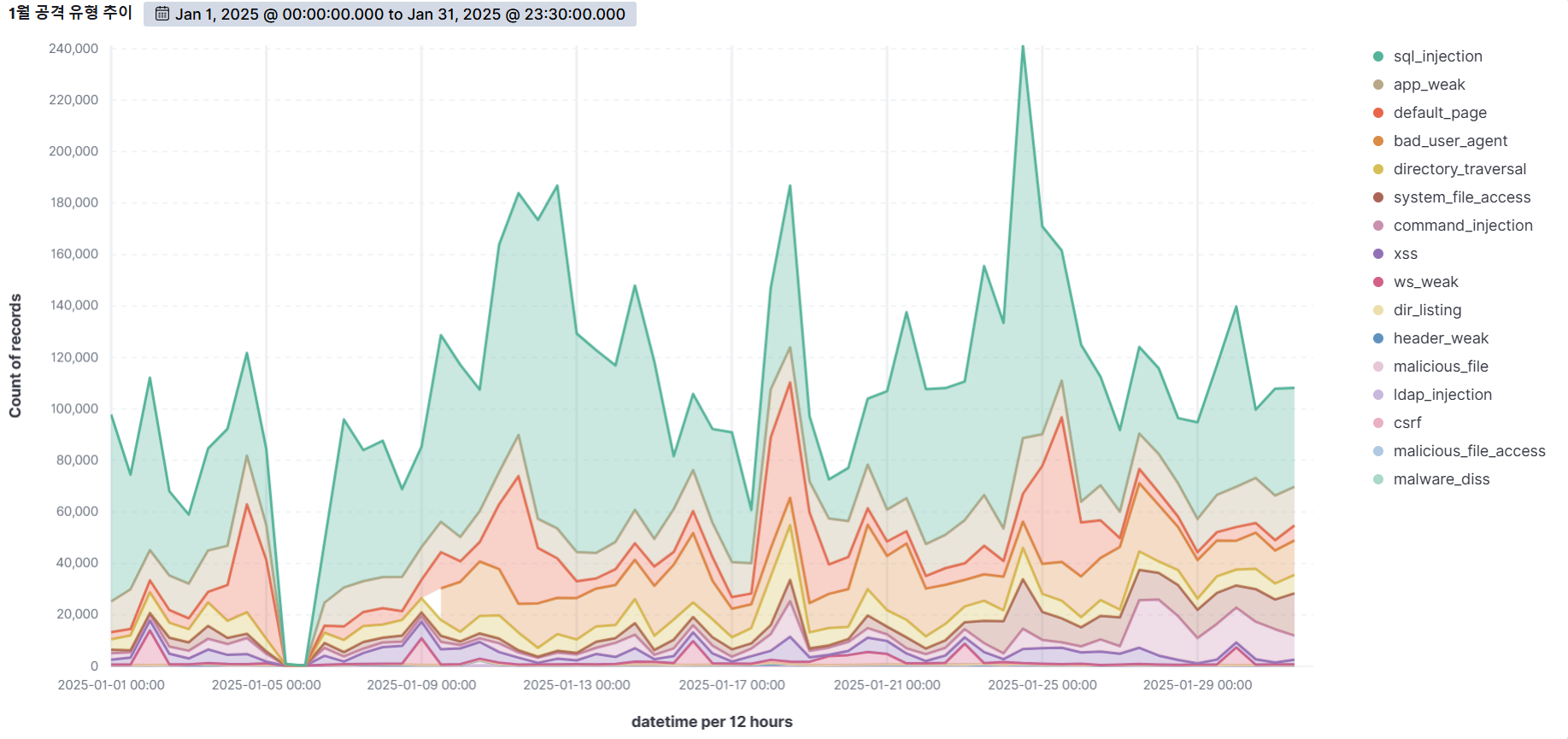
Summary of web attack trend graphs for the last 3 months
November
December
January
Top 30 Attacker IPs

Vulnerability analysis reports
Apache OFbiz Pre-Auth Remote Code Execution
1. Overview
Apache OFBiz is a free and open source ERP, and we recently analyzed CVE-2024-38856, a pre-authentication RCE vulnerability discovered in the platform.

Source : https://www.helpnetsecurity.com/2024/08/05/cve-2024-38856/
2. Attack types
CVE-2024-38856 is a pre-authentication RCE vulnerability in Apache OFBiz that allows requests to be processed without authentication due to an incorrect authentication process when processing requests for certain URLs.
There was previously a vulnerability, CVE-2024-36104, that utilized this process and was patched, but according to Sonicwall, the response was to add a check for Path Traversal without essentially fixing the feature, so it was possible to bypass that patch by sending a URL without the Path Traversal syntax.
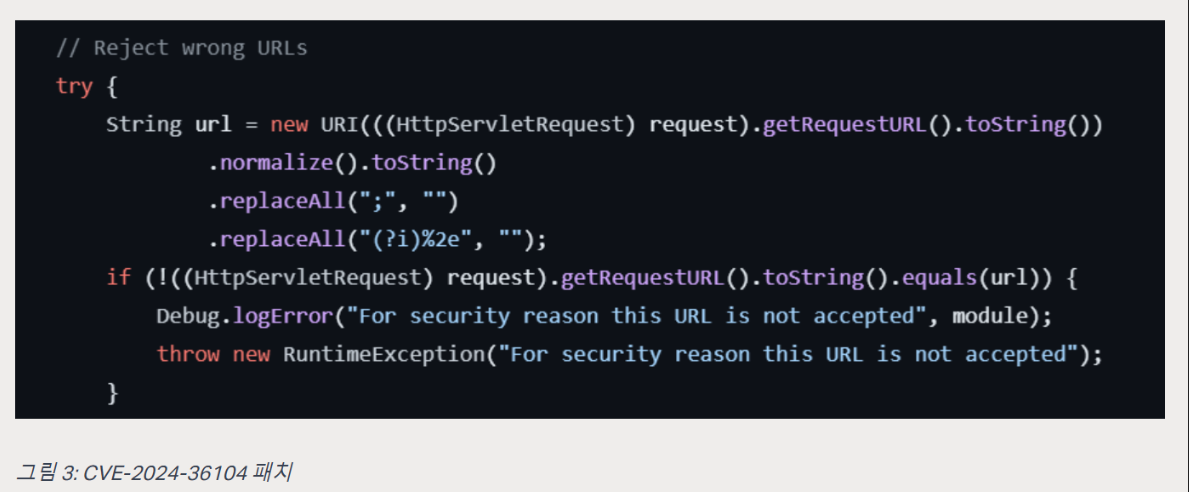
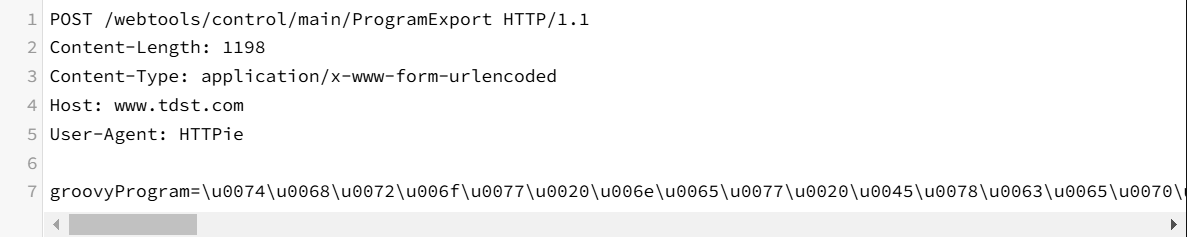
The attacker leverages the ProgramExport feature that renders page views to send a malicious payload in a groovyProgram parameter to a specific URL.
The following URLs are utilized in the attack
- /webtools/control/forgotPassword/ProgramExport
- /webtools/control/main/ProgramExport
- /webtools/control/showDateTime/ProgramExport
- /webtools/control/view/ProgramExport
- /webtools/control/TestService/ProgramExport
RCE Attack Request :
3. What to do
Apache OFBiz has released a patch for CVE-2024-38856, and users of that product should patch to version 18.12.15 or later to respond. In our AIWAF product, the vulnerability is addressed via pattern 2228: Apache OFBiz Remote Code Execution, which was added in the January 2025 pattern update.
4. Conclusion
Apache OFBiz is a powerful open source ERP that is used in many organizations due to its open source nature, and this vulnerability has been identified as a highly impactful and dangerous vulnerability that has been added to the CISA category, with a CVSS score of 9.8, and should be patched to the latest version as soon as possible.
Our AIWAF product has developed a pattern of response to vulnerabilities in Apache OFBiz, and we will continue to respond quickly to related vulnerabilities as they are discovered.
5. References
https://nvd.nist.gov/vuln/detail/cve-2024-38856
Latest vulnerability CVE status
1. High-risk vulnerability status (2025.01~02)
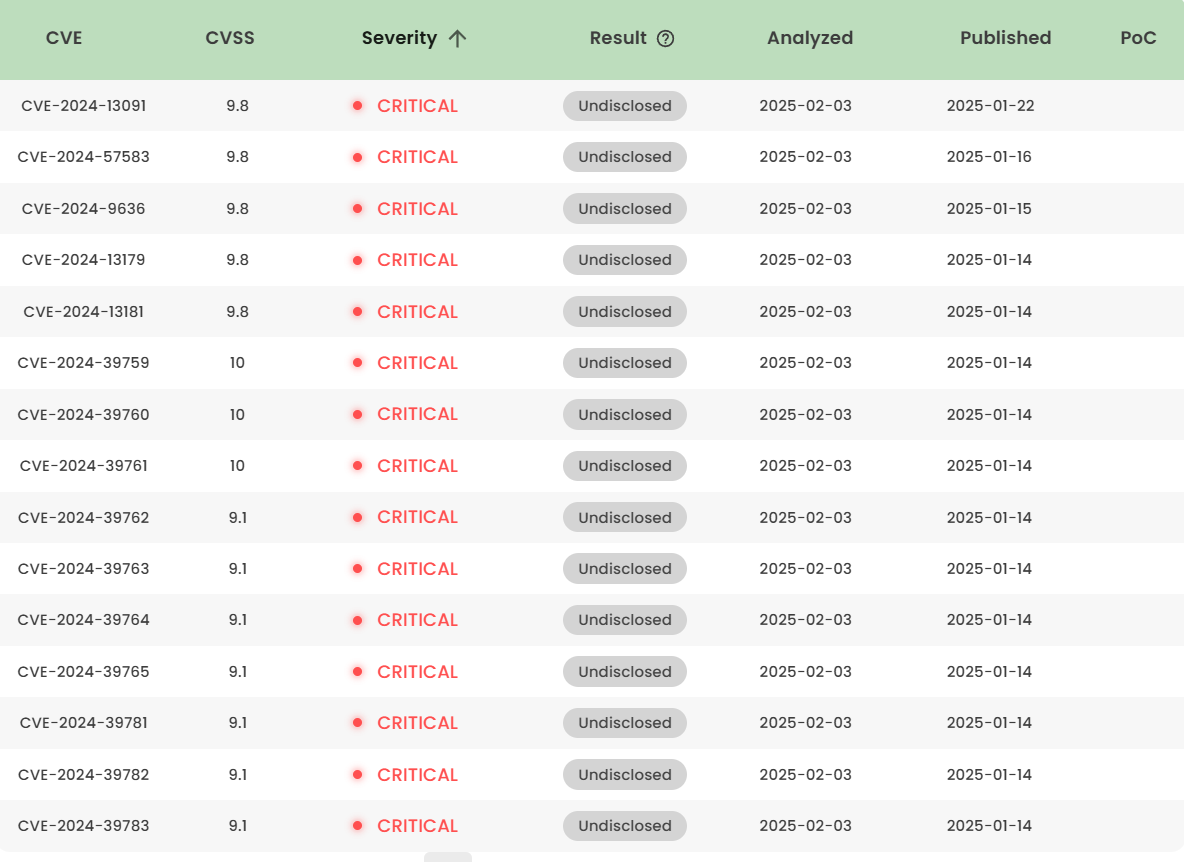
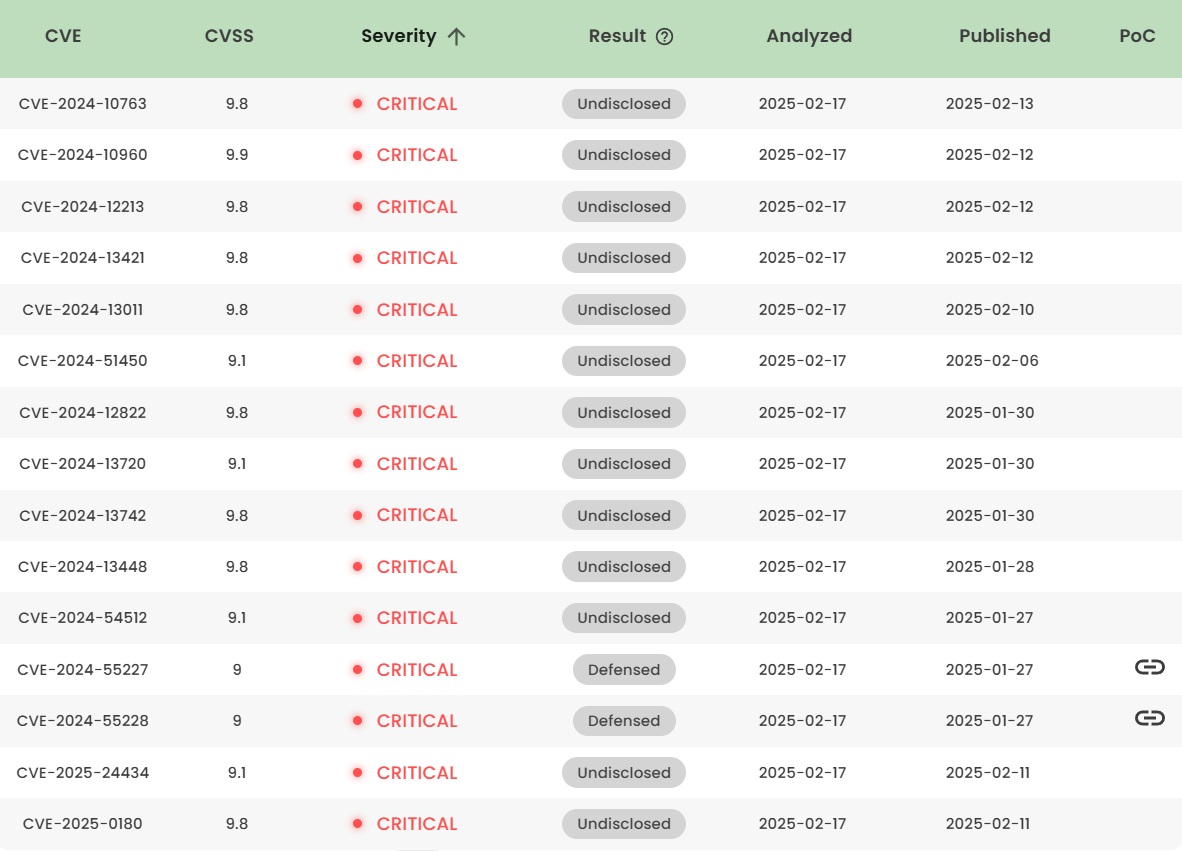
2. High-risk vulnerability descriptions