
Zero Trust Network Access (ZTNA) is often said to be an alternative to VPNs.
Then let's take a look at how ZTNA differs from traditional VPNs.

Authentication procedures
The first is the difference in the authentication process.
Zero Trust has strengthened its certification very much.
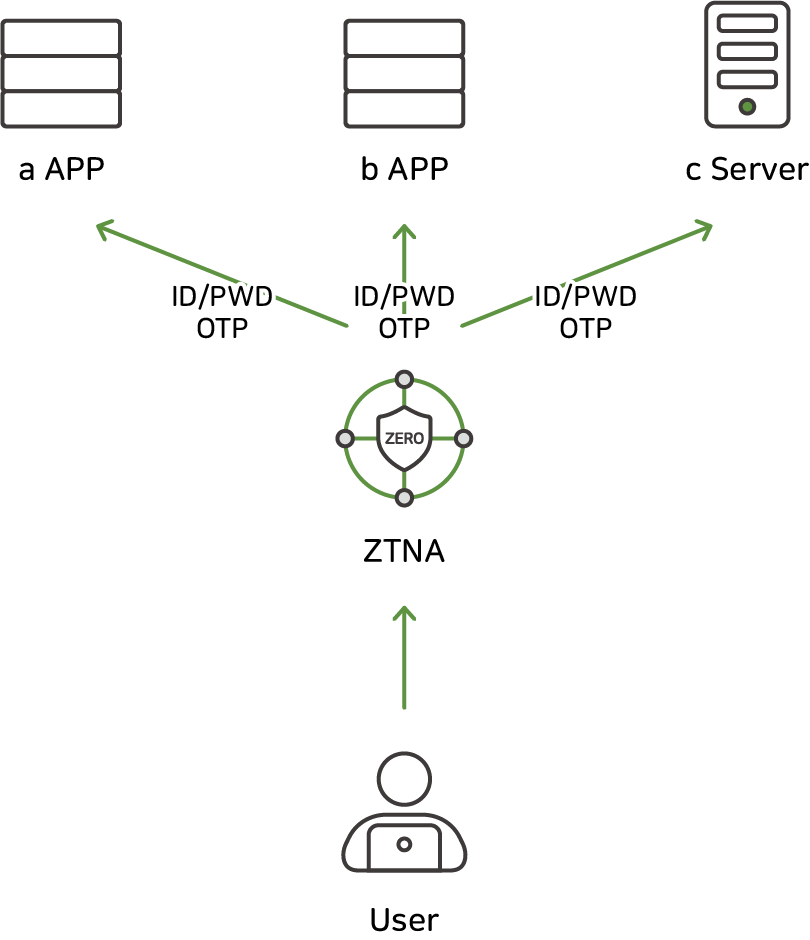
Unlike VPNs that complete authentication with simple ID/PW and OTP, various authentication mechanisms have been added to ZTNA.

For example, there is an authentication function for the physical device itself that attempts to authenticate
If the device is not authorized by the organization in advance, you will not be able to connect even if you enter the ID/PW correctly.
The second one is through a function called "Device Posture."
Authentication is allowed only if it meets the conditions specified by the administrator in advance.
The conditions at this time can be selected, such as Windows 10, whether the appropriate OS authorization,
whether the latest patch above a certain level is applied, or whether the anti-virus program is working.
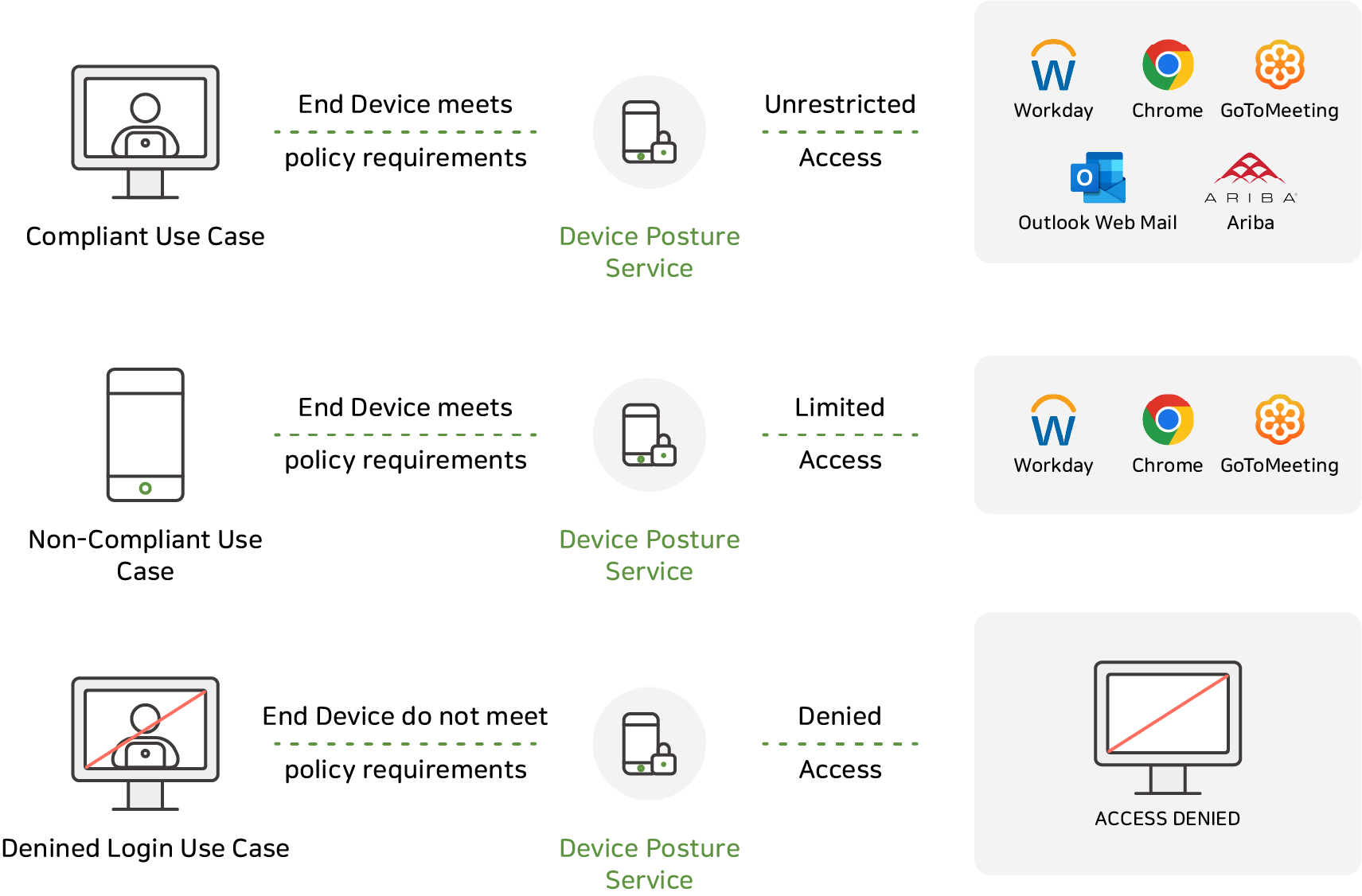
Additionally, you can also include logic to check multiple conditions, such as whether the location you are attempting to authenticate is in-house or not in a specific country.
Access range
The following are the differences in resources that can be accessed after authentication.
If you look at the picture below, you can clearly understand the difference between the two.
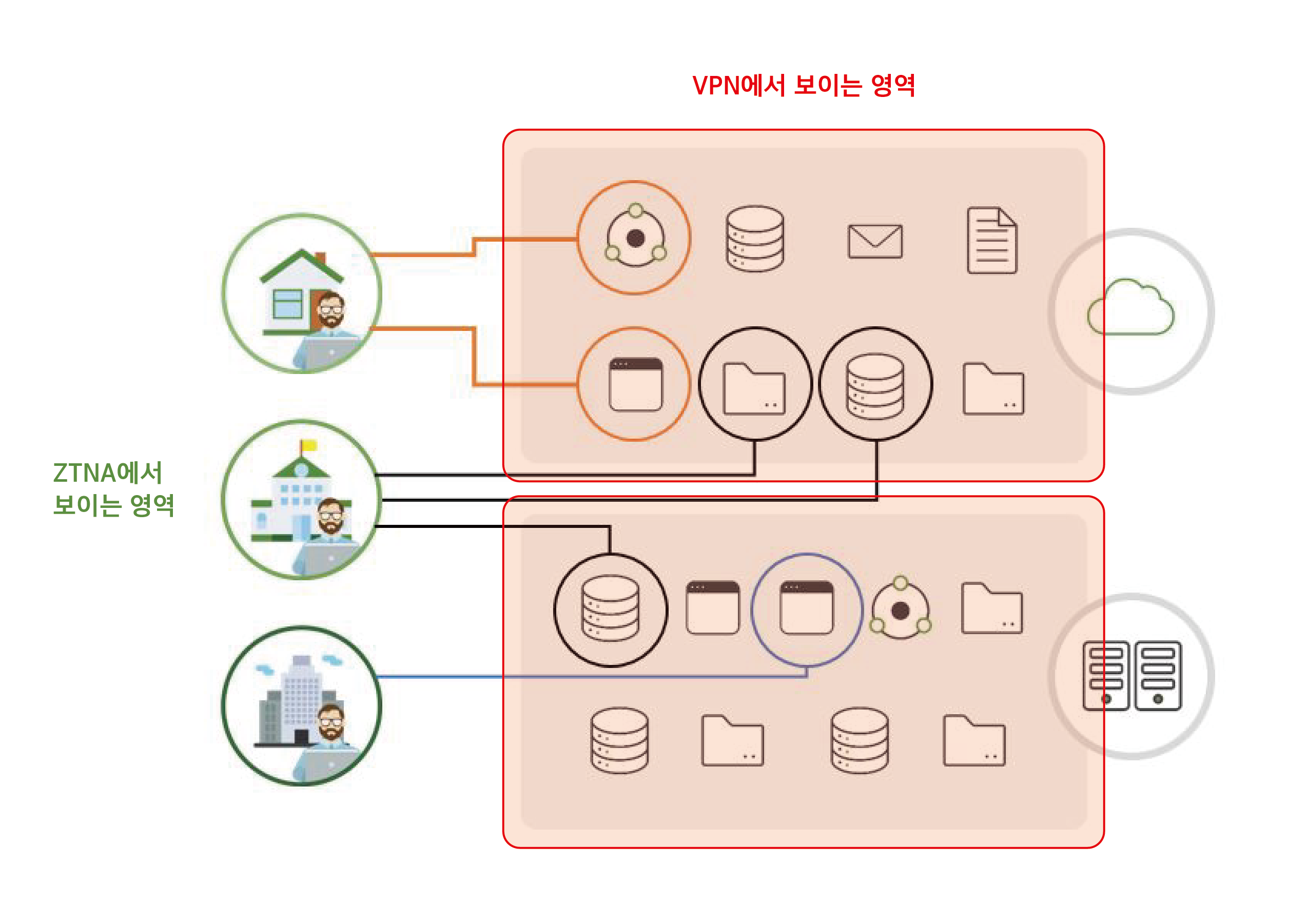
This means that VPN is just like the name "Virtual Private Network" means
It's a so-called network-based solution.
Therefore, once you connect to a VPN, you will have access to all the network resources inside that you are connected to.
ZTNA, on the other hand, is called "Network Access" itself, but "Zero Trust," which is not trusted by anyone, so it is often referred to as application-level access control.
This means that when you access ZTNA, you can only access certain resources in your network as shown in the figure above.
You cannot even ping other neighboring resources in your network even if you know the IP of the other neighboring resources in the network
because the Zero Trust Principle is "deny all" by default and only allows resources to be accessed through 1:1 tunneling.
It would be easy to understand if you think of a card key that is not accessible except on the floor where your room is to stay at the hotel.
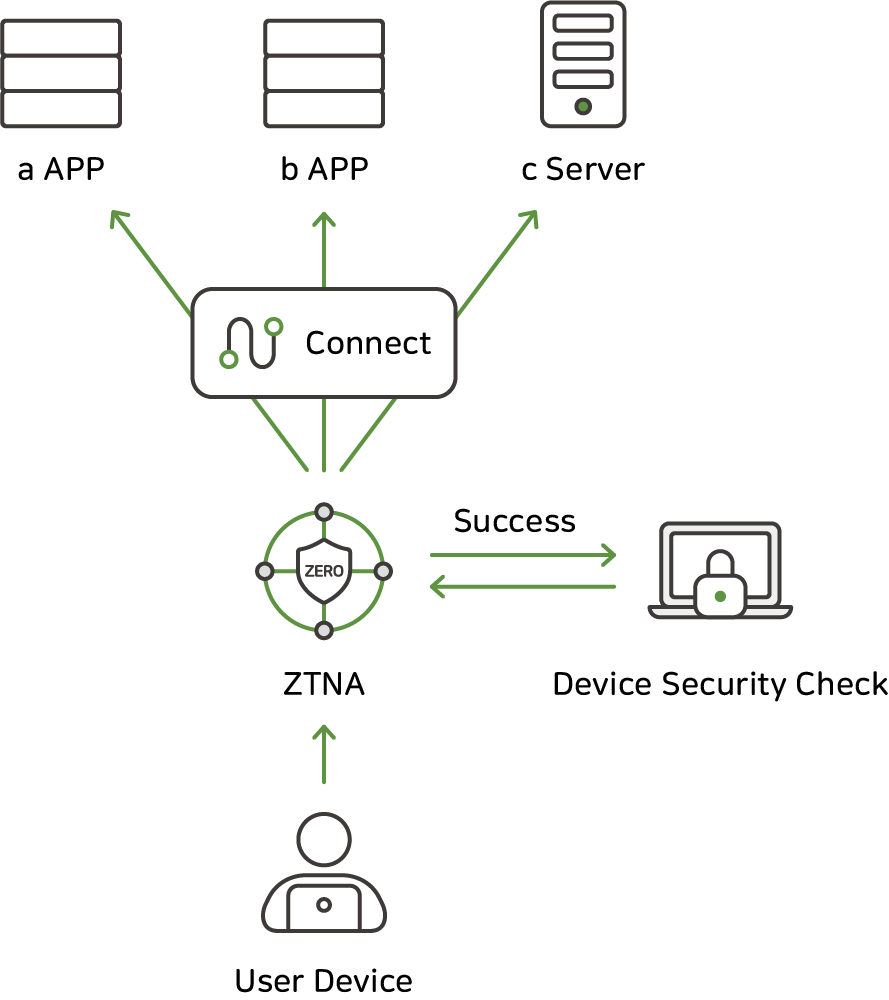
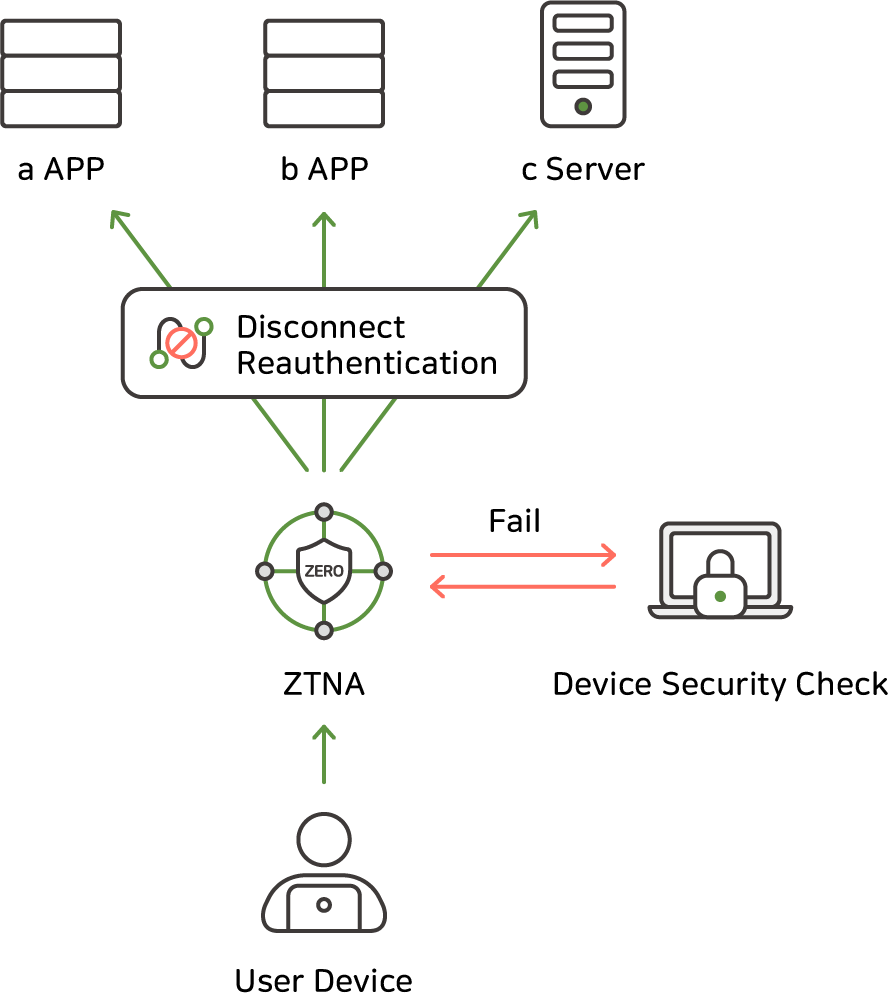
Continuous Authentication
The "persistent authentication" that ZTNA refers to may be misunderstood as annoying users by repeatedly entering ID/PW and OTP each time they access additional resources,
but it has a different meaning.
In other words, even if ZTNA satisfies all conditions at the time of initial authentication and succeeded in authentication,
it will be able to continuously check the security status of the device, which is an authentication condition,
and if the condition changes, even if it is already successful, it will be able to terminate the session or request re-authentication.
For example, if you pass the authentication by satisfying the condition in the environment where the anti-virus program is running at the time of initial authentication,
but if you forcefully terminate or delete the program afterwards, you can detect it and block the current session and force it to re-authenticate.
So far, we've looked at the differences between conventional VPNs and ZTNAs.
I hope this opportunity will give us an opportunity to understand why ZTNA is more secure than VPN and says it is an alternative solution.


