Weekly web attack trends
Weekly web attack trends allow you to see when web attacks are most prevalent. This can help you plan ahead to prevent and respond to web attacks during peak periods.
The graph below shows the web attacks detected by AIWAF as of June 2024.
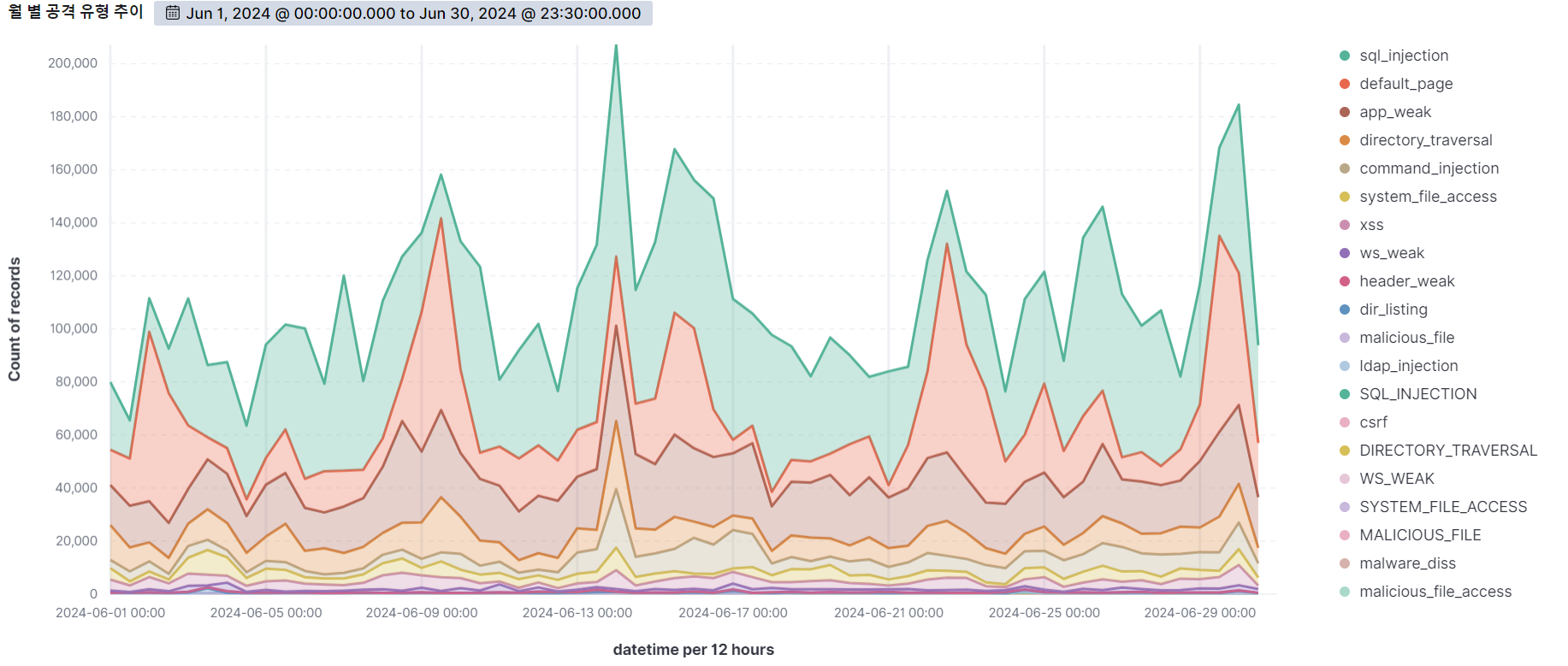
In June 2024, we detected over 200,000 attacks per day on average, with the highest number of attacks occurring on the 14th.
SQL Injection, the vulnerability with the most attempted attacks on the 14th, has the most detection conditions in our AIWAF. However, SQL Injection attacks are always being monitored because there are many new attack types and evasion methods.
Web attack trends by attack type
Web attack trends by attack type, based on detection logs, allow you to see which attacks were most prevalent during the month. Based on this, you can establish basic web attack response guidelines to prevent and respond to those types of attacks.
The graph below shows the web attacks detected by AIWAF as of June 2024.
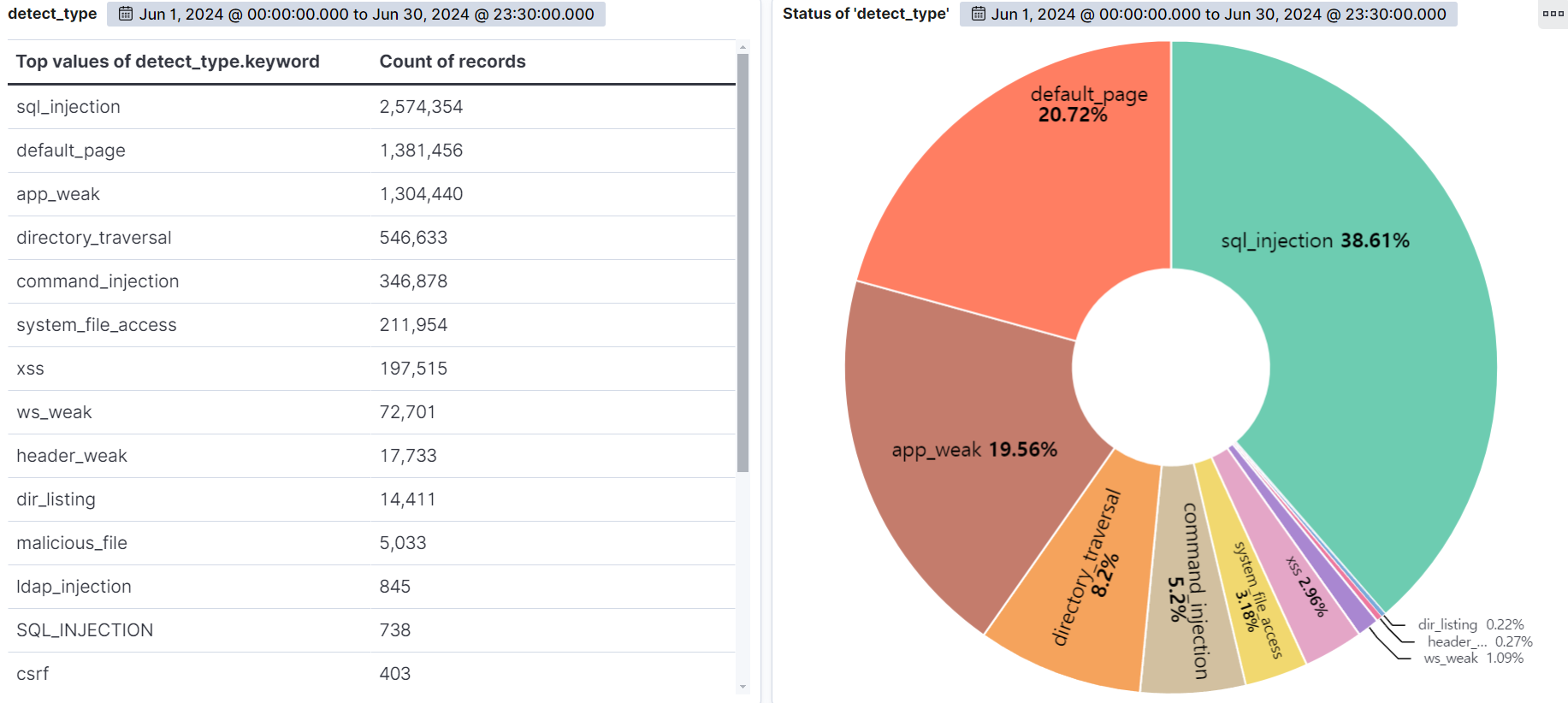
SQL Injection (38.61%) was the most common attack type, followed by Default page (20.72%), app weak (19.56%), and Directory Traversal (8.2%).
SQL Injection is the most diverse and dangerous attack, as it is ranked #1 by OWASP. It is an attack that forces malicious SQL statements into SQL statements that dynamically generate data based on user requests, which can cause vulnerable applications to authenticate or return abnormal SQL results. If you encounter the following syntax in your query values, you should suspect an attack.
Default page attempts to access a file from an unusual path or bypasses authorization to access the file directly. These are not files typically used in web services, so be suspicious of malicious intent.
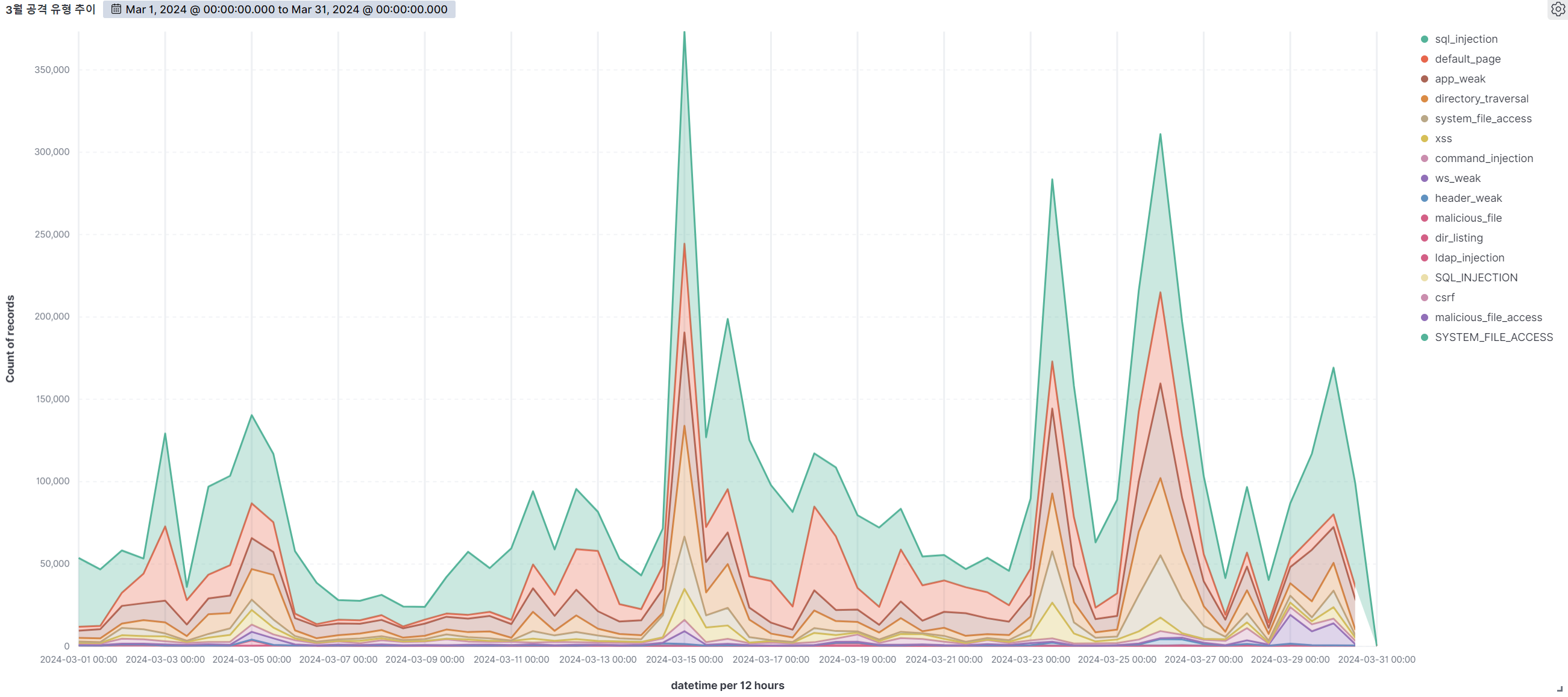
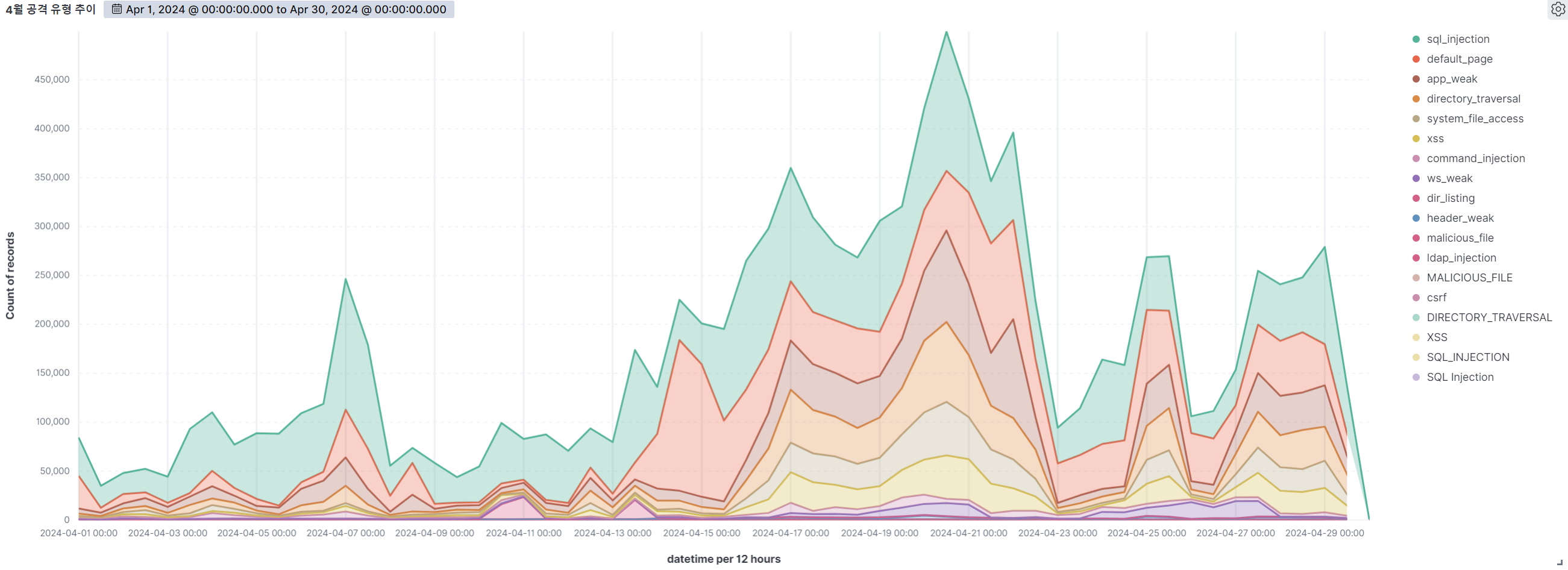
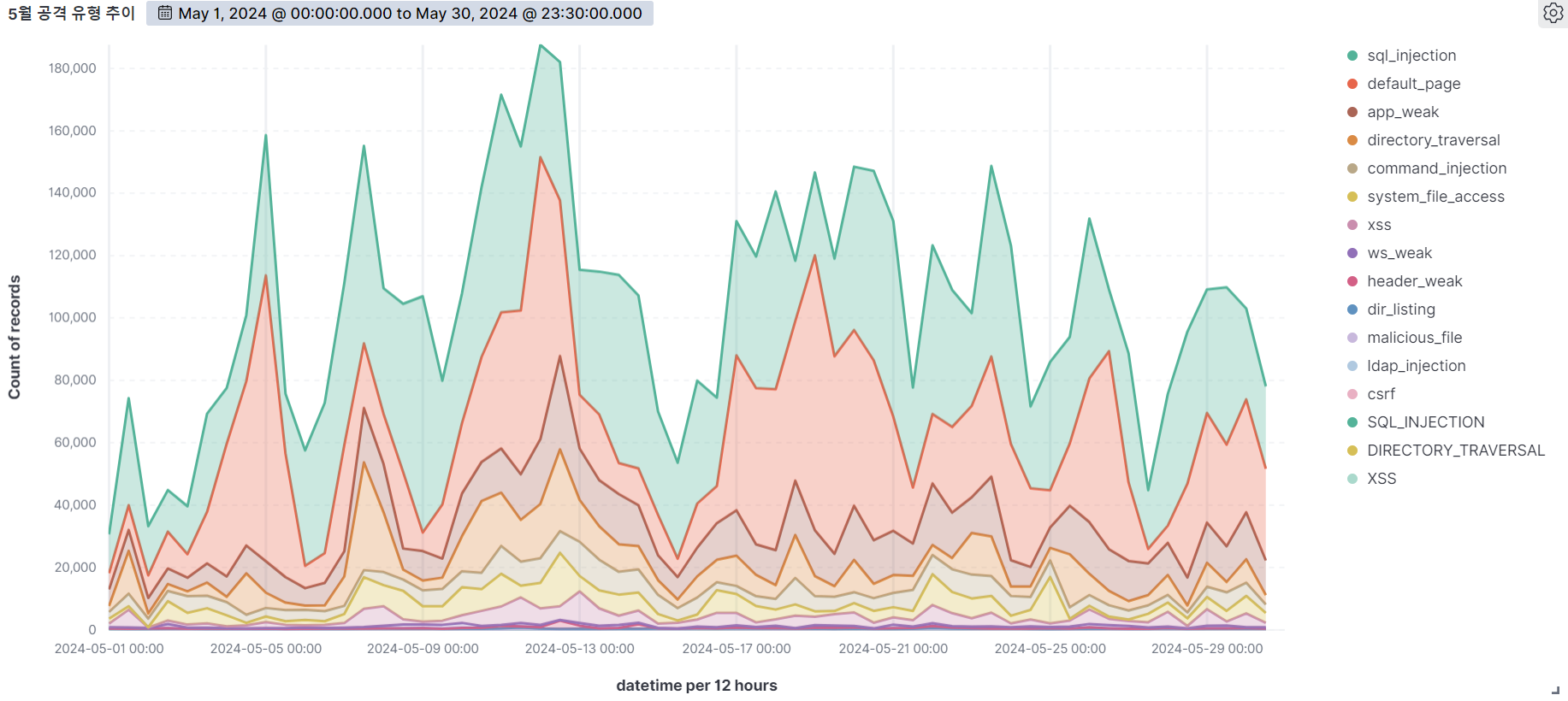
Summary of web attack trend graphs for the last 3 months
March
April
May
Top 30 Attacker IPs

Vulnerability analysis reports
[PHP-CGI Argument Injection]
1. Overview
We analyzed the recent Argument Injection and Remote Code Execution vulnerabilities in Apache and PHP-CGI running on Windows.

Image source : https://portswigger.net/daily-swig/php-package-manager-component-packagist-vulnerable-to-compromise
2. Attack types
The vulnerability occurs when using certain versions of PHP-based services running on Windows, and it became a big deal when watchTowr published analysis and exploit information for the vulnerability.
The PHP-CGI service parses HTTP requests and passes them to a php script, which basically looks like this: php.exe cgi.php test=test for a query string like https://test.com/test=test.
To prevent attacks that exploit this fact to inject arbitrary commands, PHP-CGI performs escaping on the characters used in the attack, but attackers have found that they can bypass the header escape operation by using the “Best-Fit Mapping” feature of the Win32 API function, which converts certain characters to arbitrary characters when PHP-CGI is running on Windows.
The strings below are call strings consisting of a real hyphen (-) character and a soft hyphen (0xAD) character, which at first glance appear to be indistinguishable, but checking the data in hexadecimal form via HxD reveals that they are different.

A legitimate call utilizing a real hyphen (-) character in php.exe and a malicious call utilizing a soft hyphen (0xAD) character.
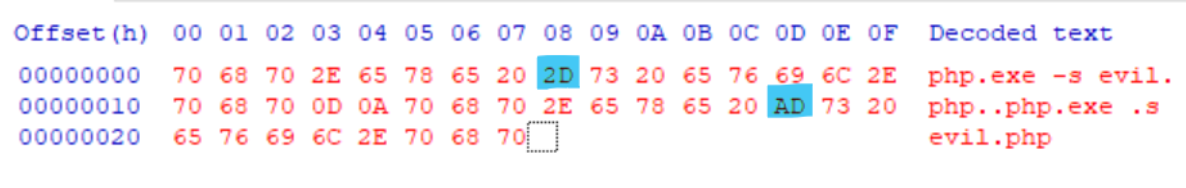
Compare calls verified by Hxd.
The soft hyphen character is not escaped by CGI handlers because it is not a real hyphen character, but because of the “Best-Fit Mapping” feature discussed earlier, it can be interpreted as a real hyphen character in PHP, allowing arbitrary command arguments to be injected.
This injects an argument designed to perform an RCE attack, leading to the execution of malicious PHP code.
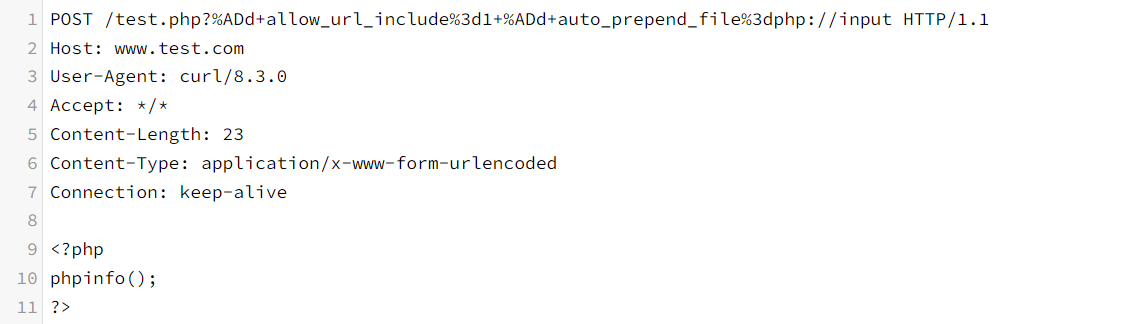
3. What to do
Fortunately, PHP has been quick to release patches for this vulnerability, so PHP versions 8.1.29, 8.2.20, and 8.3.8 should be covered when you update to version 8.3.8.
Our AIWAF product natively detects requests containing malicious PHP code in the 825: Webshell pattern, so this attack is also being detected, but we believe that additional patterns for the soft-hyphenated attack syntax are needed and are in the process of further analysis and pattern development.
4. Conclusion
The Argument Injection attack in PHP-CGI running on Windows is a simple and easy to exploit vulnerability, and since many organizations still use PHP-based services such as Apache, the impact is high and it is important to update to the latest version as soon as possible.
Our AIWAF product has developed patterns to respond to vulnerabilities in PHP-CGI, and we will continue to respond quickly to related vulnerabilities as they are discovered.
5. References
https://nvd.nist.gov/vuln/detail/CVE-2024-4577
https://labs.watchtowr.com/no-way-php-strikes-again-cve-2024-4577/
https://github.com/watchtowrlabs/CVE-2024-4577
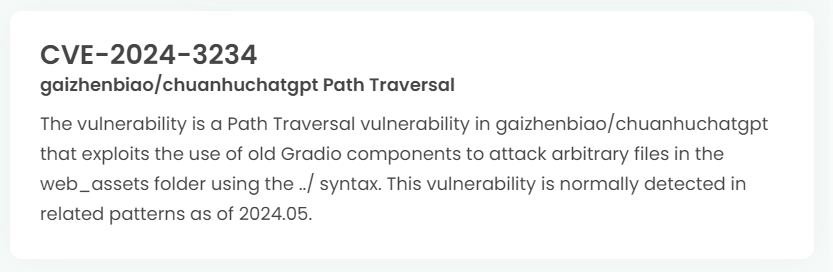
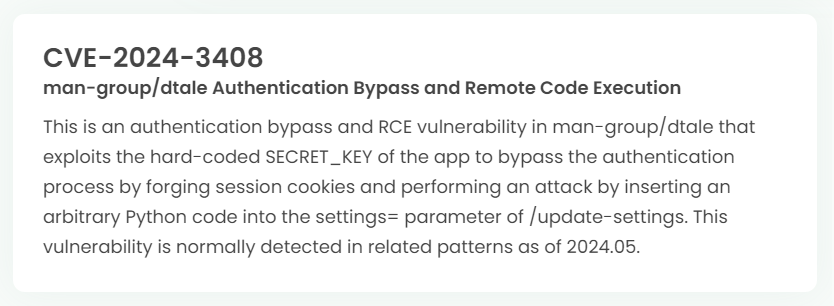
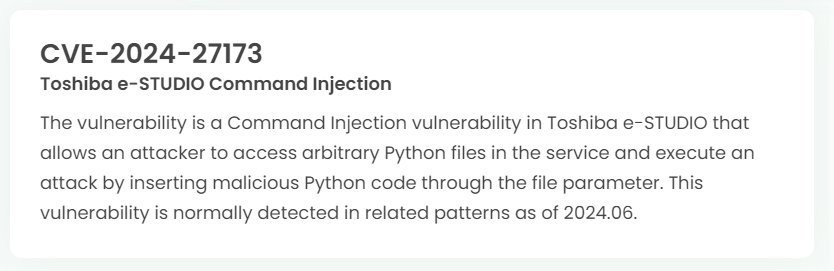
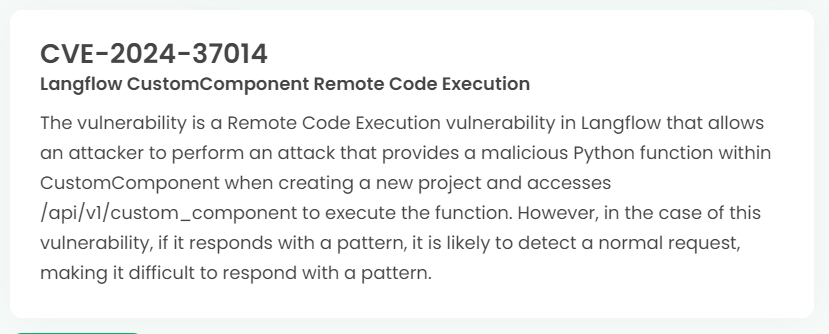
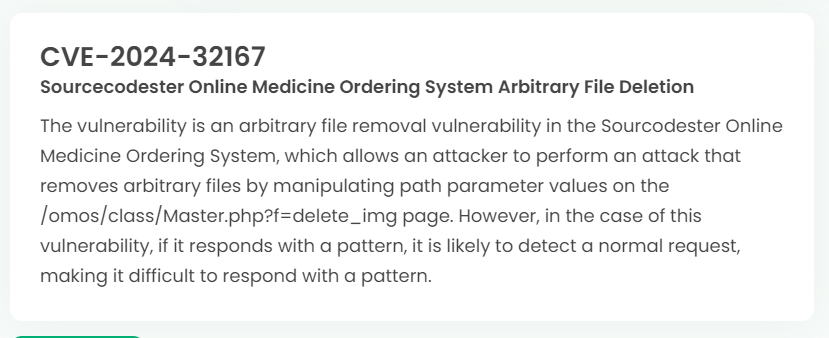
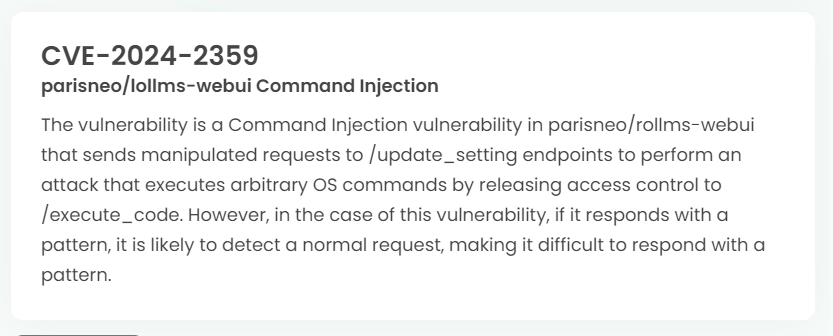
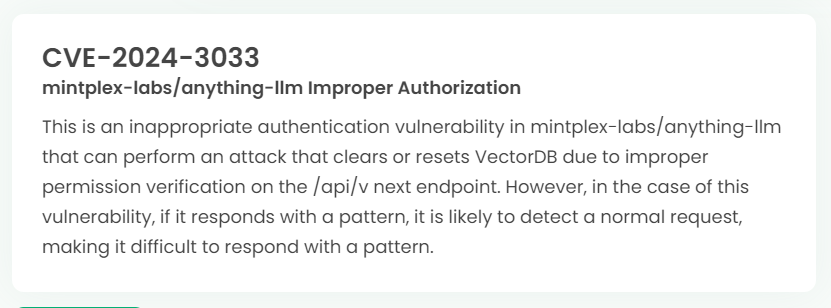
Latest vulnerability CVE status
1. High-risk vulnerability status (2024.06)
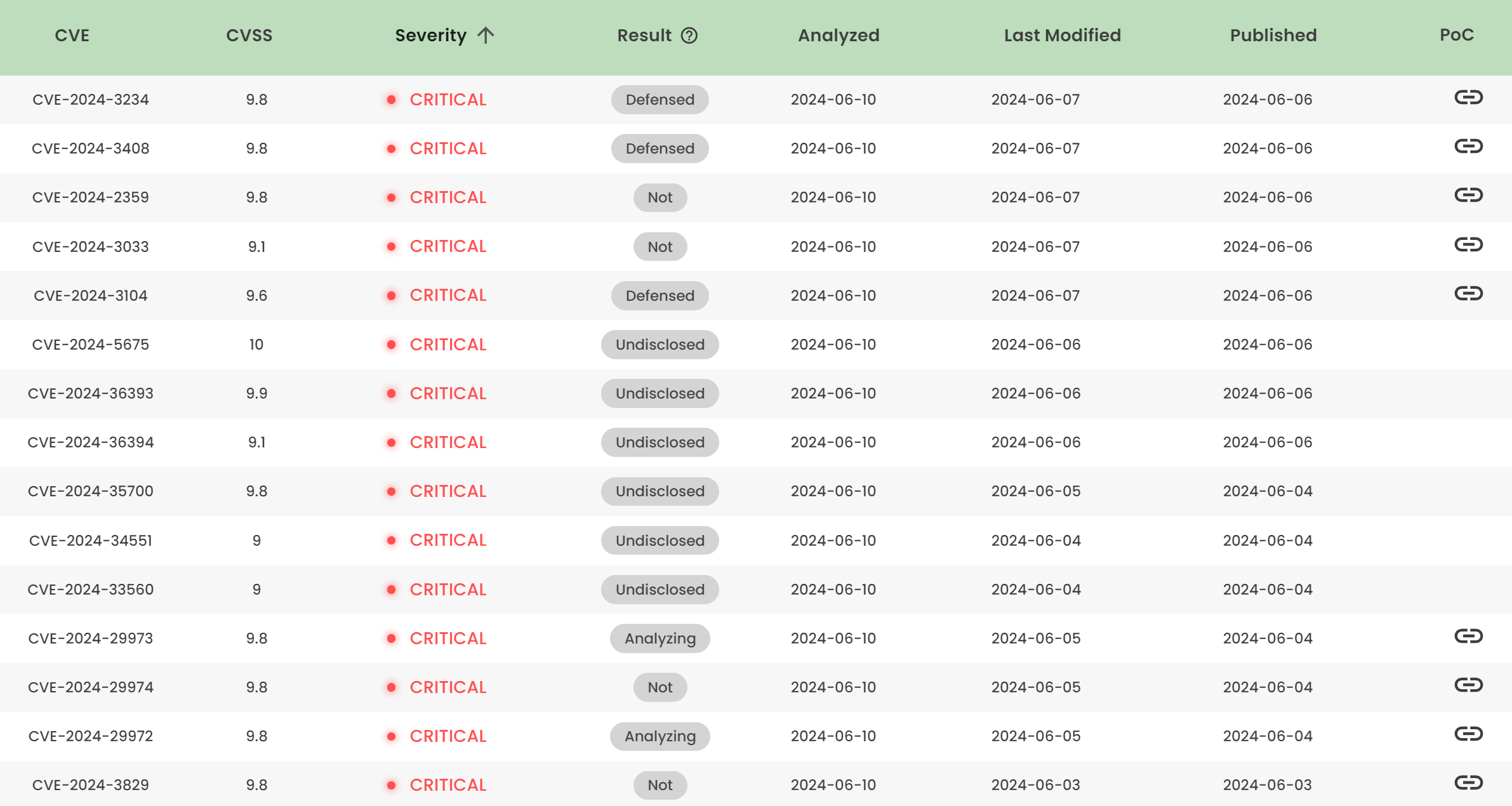
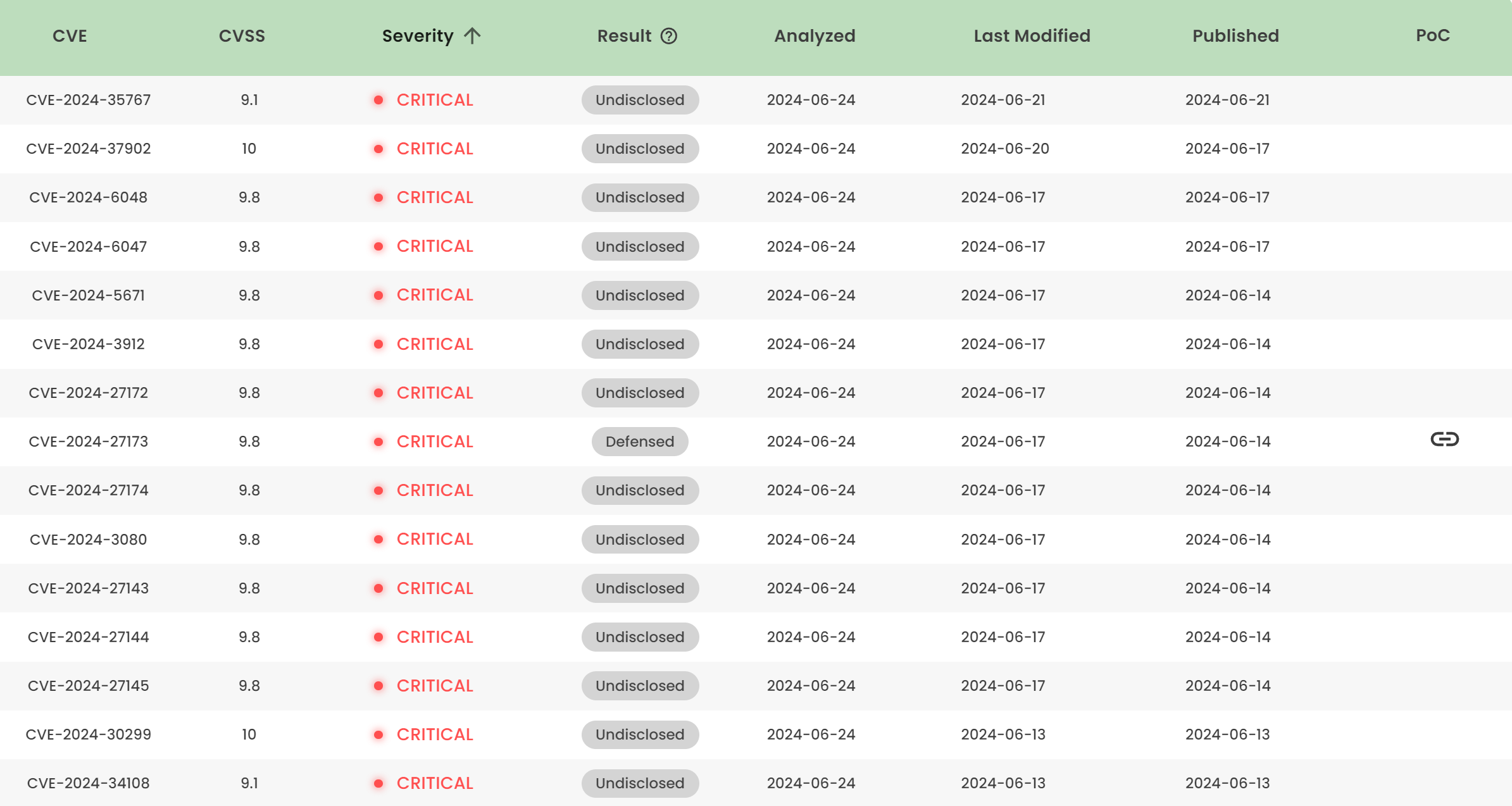
2. High-risk vulnerability descriptions