
Today, digital transformation and the proliferation of cloud technologies are rapidly transforming the enterprise network landscape,
and with the rise of remote work and cloud-based applications, traditional network security models are no longer sufficient.

Traditional security models rely primarily on physical perimeters to create a clear distinction between inside and outside,
but cloud environments and the proliferation of remote work have blurred these boundaries, making network resources more vulnerable to cyber threats.
Traditional network security primarily utilizes VPNs, IDS/IPS, and more to protect the perimeter of the network.
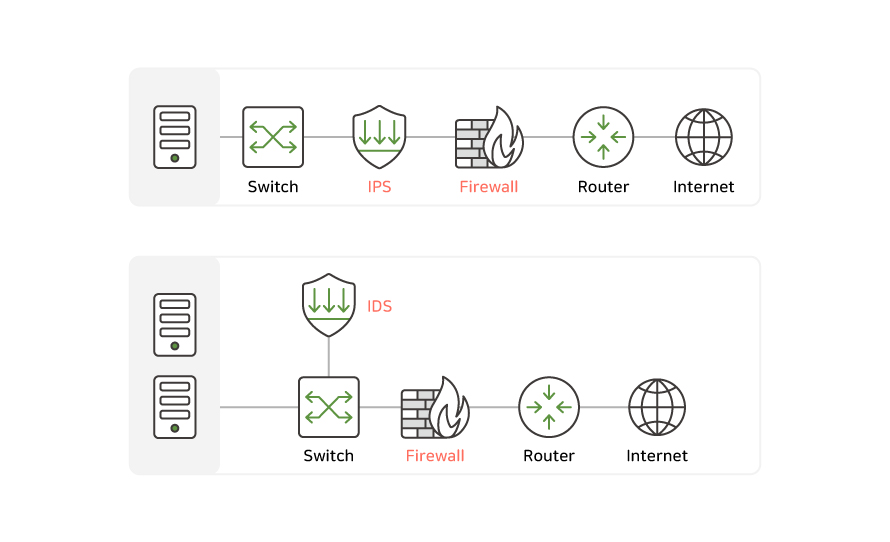
This approach relied on trusting the internal network and controlling only external transfers.
However, it is vulnerable to insider threats such as collusion or privilege escalation by internal users, and is particularly difficult to defend against lateral movement.
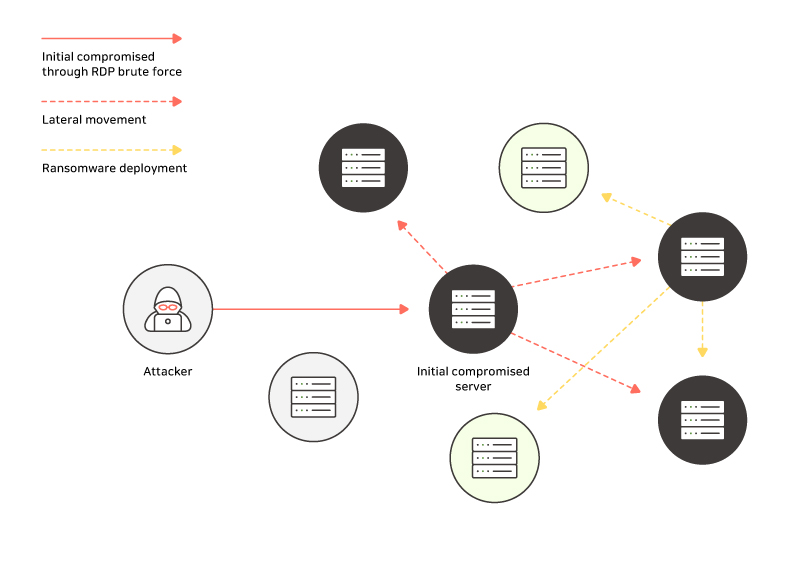
Lateral movement means that once an attacker is inside your network, they gradually gain access to more and more resources as they move from less privileged to more privileged systems.
In other words, if even one of the perimeters protecting your internal network from outside attackers is breached, the overall effect can be devastating.
Zero Trust Architecture (ZTA), which is based on the idea of “not trusting”, has emerged to address the holes in security caused by these changing times.
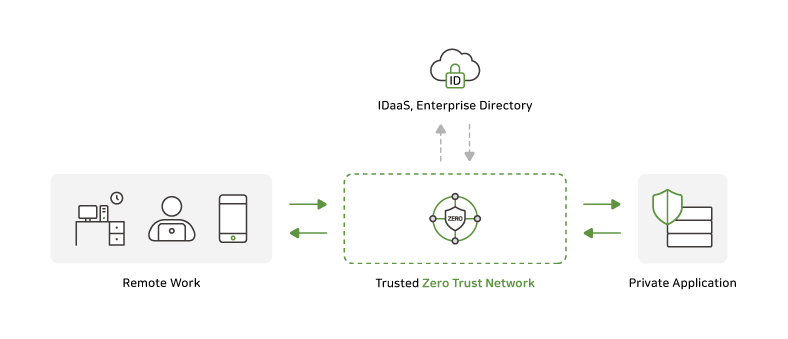
ZTA always verifies the identity of the user and adopts a security strategy centered on individual resources and data, rather than network perimeters.
To enable this “ZTA,” a key technology has emerged: software-defined perimeter (SDP).
What is a Software Define Perimeter (SDP)?
SDP is one of the key technologies in the Zero Trust security model for securing network resources and ensuring that only authorized users can access them.
By default, SDPs keep all network resources private and only allow access to them when a user or device has trusted credentials.
By ensuring that network resources are not unnecessarily exposed, SDP is an excellent way to protect them from malicious access, both from external attackers and from within.
The core principle of SDP is to make network resources “invisible”.
This means that resources on your network appear to be nonexistent to unauthenticated users.
This prevents unnecessary access attempts or attack attempts.
SDP also dynamically grants or restricts access based on a comprehensive analysis of the user's identity, location, device state, and more.
This provides strong security not only in traditional network environments, but also in situations where network boundaries have become blurred, such as in modern cloud environments.
AIONCLOUD Secure Remote Access (SRA) is a ZTNA service that utilizes SDP to continuously validate users or devices and only allow access after verifying that they are trusted.
Built on top of ZTA, AIONCLOUD SRA strictly controls all access between users and resources, protecting your organization's assets from all threats, both internal and external.
AIONCLOUD SRA enhances your organization's security in the following ways
Network invisibility
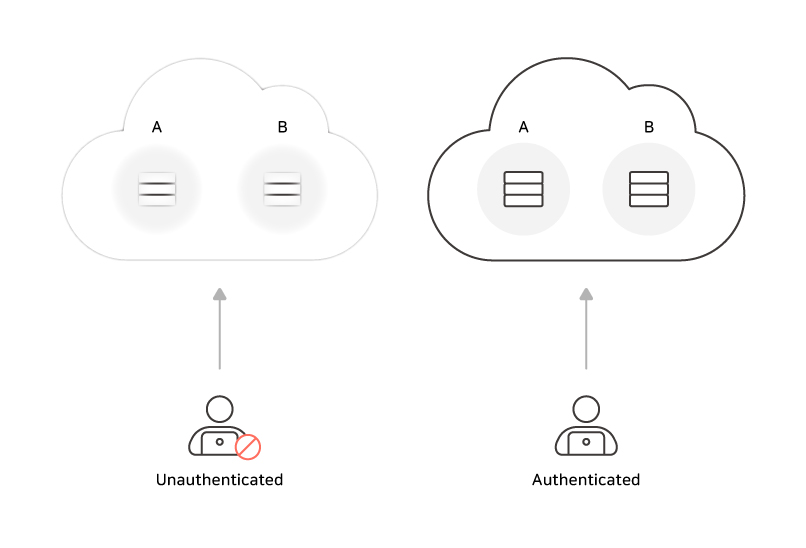
Until a user is granted access, resources within the network are invisible to anyone.
Therefore, unauthorized users cannot even recognize the existence of network resources.
AIONCLOUD SRA is effective in preventing cyberattackers from targeting network resources, thus eliminating potential threats at the source.
Flexible access control
AIONCLOUD SRA analyzes user identity and device status in real time, regardless of the physical network configuration, enabling fluid adjustment of access rights.
This has the advantage of allowing you to quickly modify security policies based on network conditions.
For example, whereas previously network segments had to be physically separated, AIONCLOUD SRA allows you to logically separate user groups and resources.
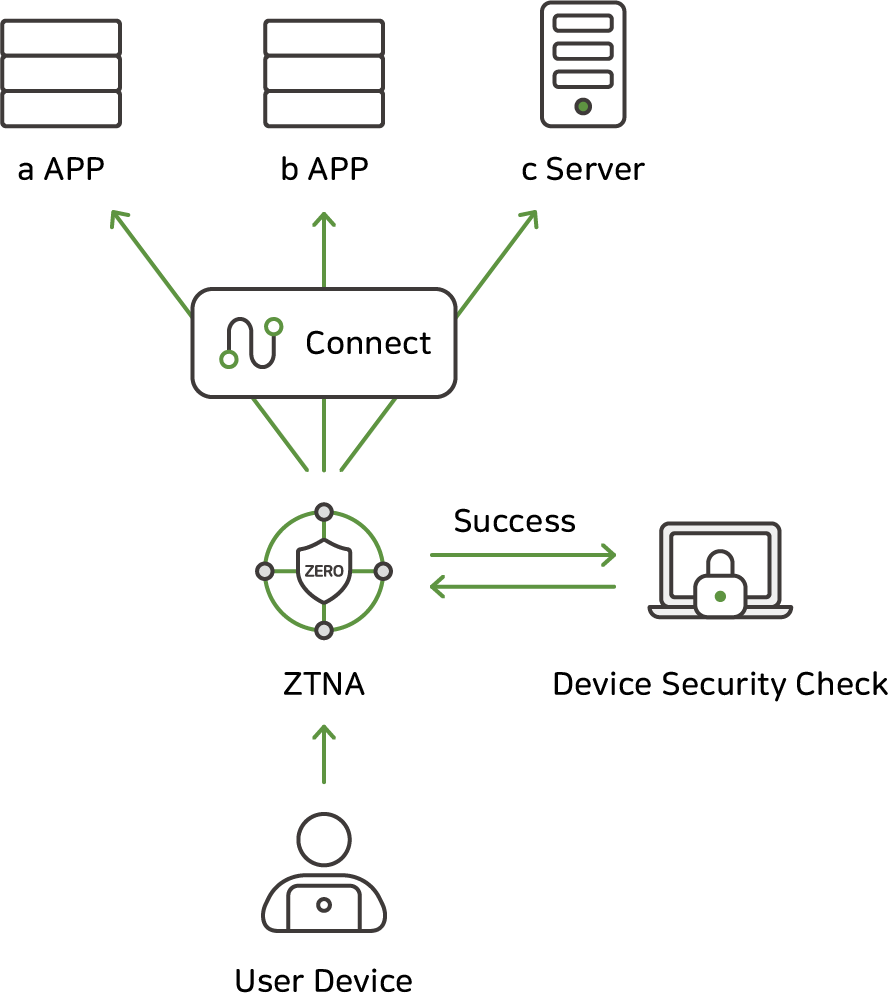
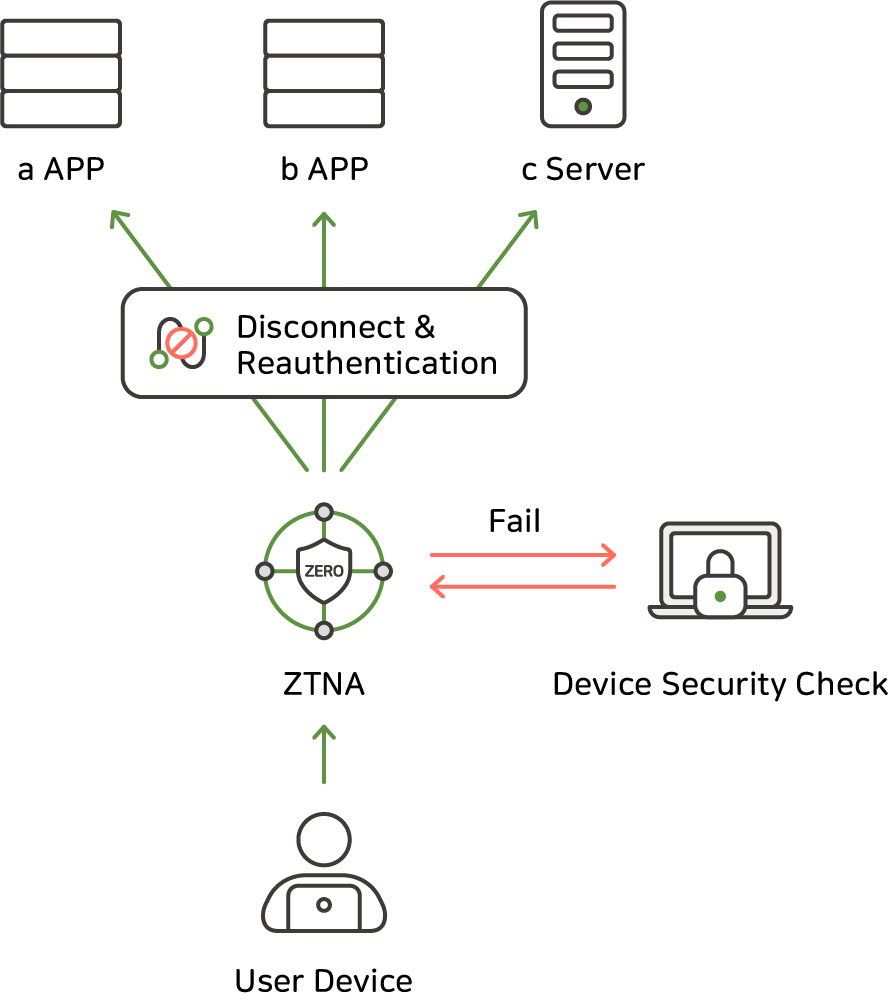
Enhance security
AIONCLOUD SRA requires strict authentication for every access, providing an effective defense against both external attacks and insider threats.
For example, users must go through an authentication process every time they access a cloud application, ensuring that only trusted users can access the network.
Flexible scalability
AIONCLOUD SRA can be applied in a variety of environments, including cloud environments, hybrid clouds, and remote work, in addition to on-premises environments.
Especially when organizations introduce new cloud services or remote work solutions, AIONCLOUD SRA enables them to extend their existing security policies without the need for additional physical security devices.
As digital transformation accelerates and network boundaries become increasingly blurred, organizations need new security strategies.
AIONCLOUD SRA leverages SDP to secure network resources and ensure that only authorized users can access them.
This enables organizations to effectively respond to evolving cyber threats.
SDP is not just another security technology; it is becoming an essential component of a future security strategy.
Now is the time for organizations to adopt AIONCLOUD SRA to keep pace with the changing security landscape.
Protect your organization's valuable assets with AIONCLOUD SRA as the security landscape evolves.
If you are interested in learning more about AIONCLOUD SRA, please visit the URLs below.


