Weekly web attack trends
Weekly web attack trends allow you to see when web attacks are most prevalent. This can help you plan ahead to prevent and respond to web attacks during peak periods.
The graph below shows the web attacks detected by AIWAF as of September 2024.
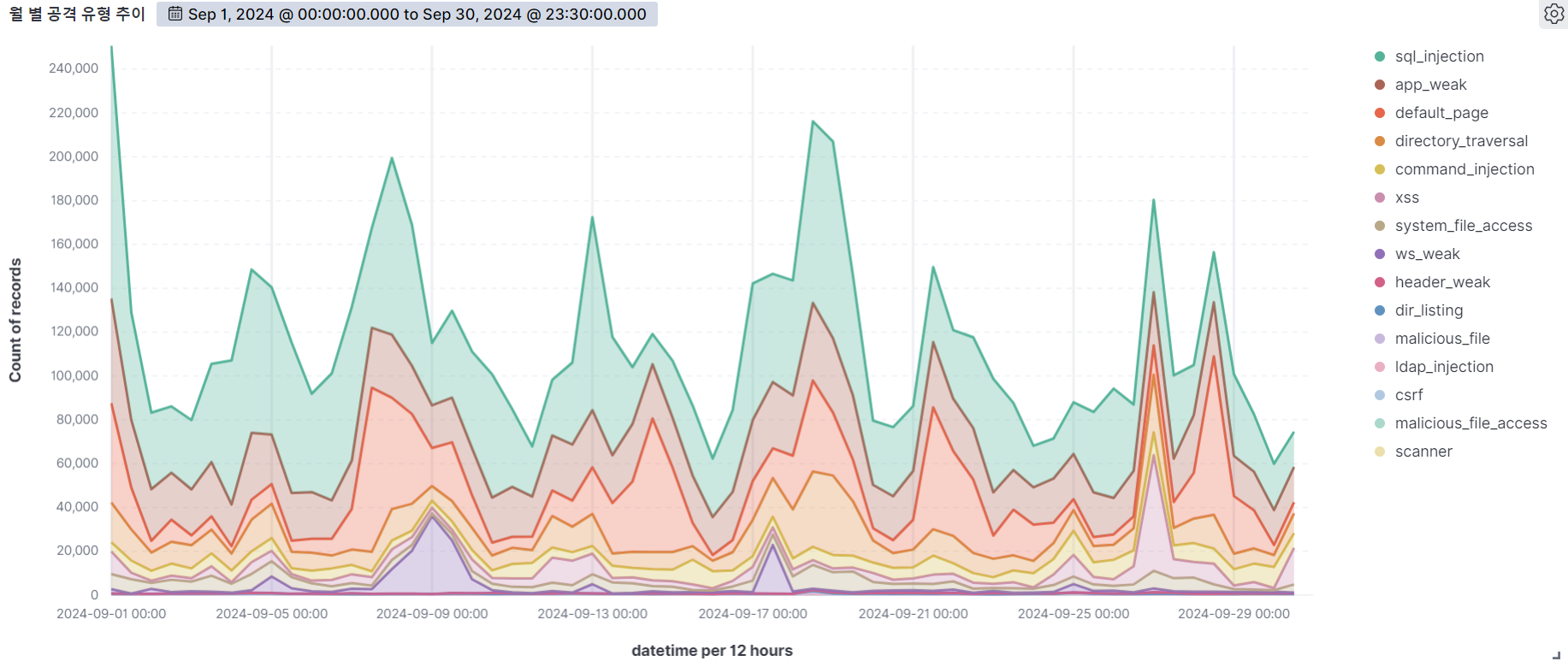
In September 2024, we detected over 230,000 attacks per day on average, with the highest number of attacks occurring on a single day.
SQL Injection, the vulnerability with the most attempted attacks in 24 days, has the most detection conditions in our AIWAF. However, SQL Injection attacks are always being monitored because there are many new attack types and evasion methods.
Web attack trends by attack type
Web attack trends by attack type, based on detection logs, allow you to see which attacks were most prevalent during the month. Based on this, you can establish basic web attack response guidelines to prevent and respond to these types of attacks.
The graph below shows the web attacks detected by AIWAF as of September 2024.
Web Attack Trends by Rule
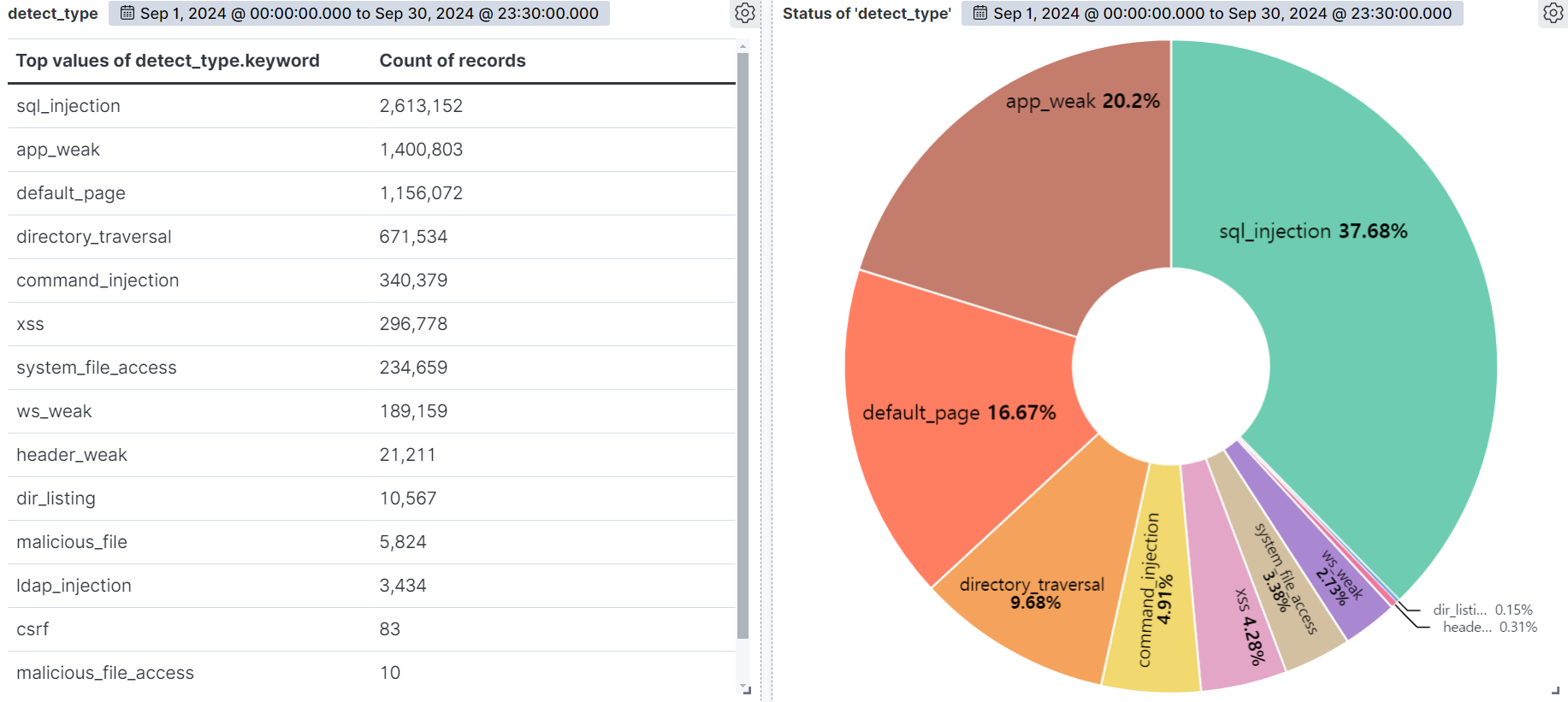
SQL Injection (37.68%) was the most common attack type, followed by App weak (20.2%), Default page (16.67%), and Directory Traversal (9.68%).
SQL Injection is the most diverse and dangerous attack, as it is ranked #1 by OWASP. It is an attack that forces malicious SQL statements into SQL statements that dynamically generate data based on user requests, which can cause vulnerable applications to authenticate or return abnormal SQL results. If you encounter the following syntax in your query values, you should suspect an attack.
APP WEAK indicates a vulnerability within an app that an attacker can exploit to gain unauthorized access or perform malicious actions. These vulnerabilities can be the result of poor coding practices, misconfiguration, or insufficient security measures. As a general rule of thumb, be suspicious of unauthorized files in addition to authorized files when using app programs.
Summary of web attack trend graphs for the last 3 months
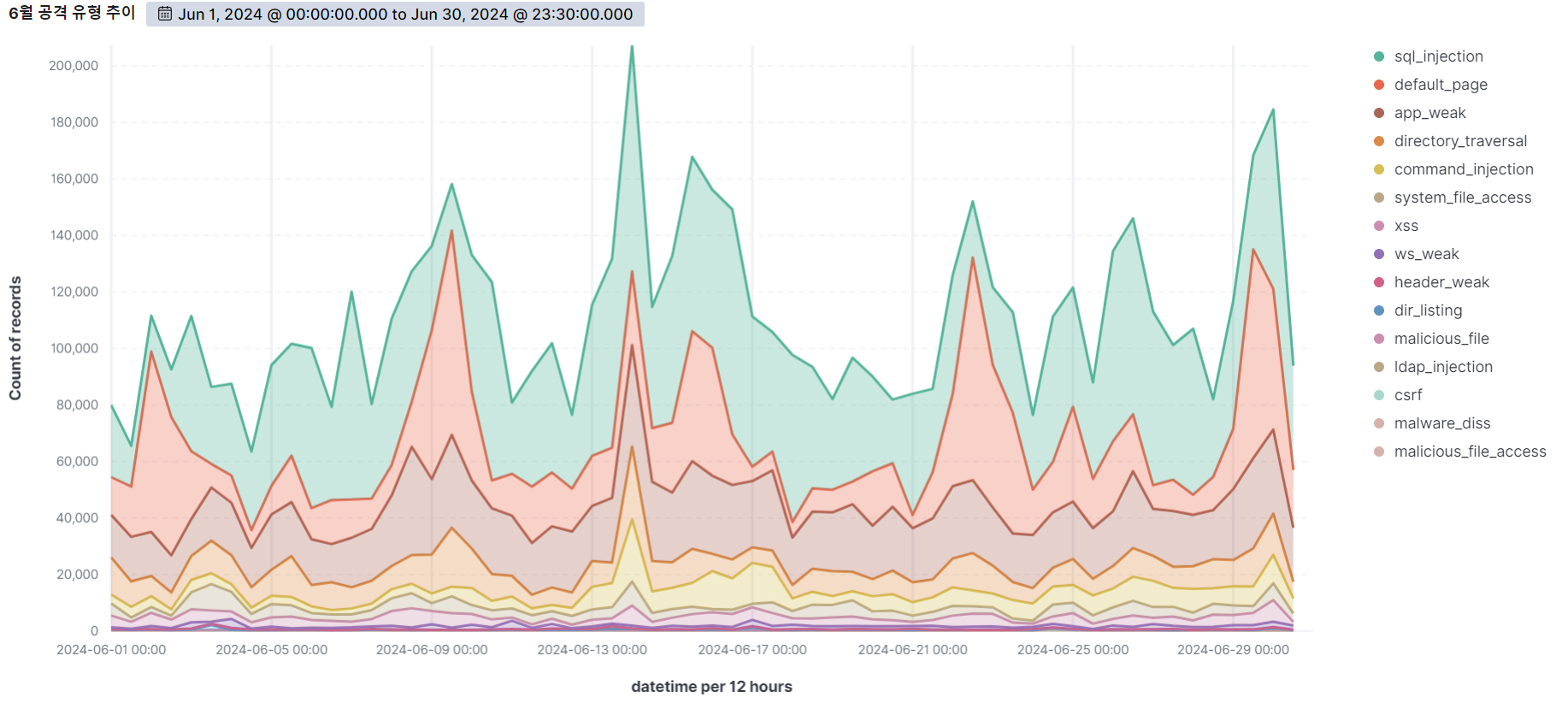
June
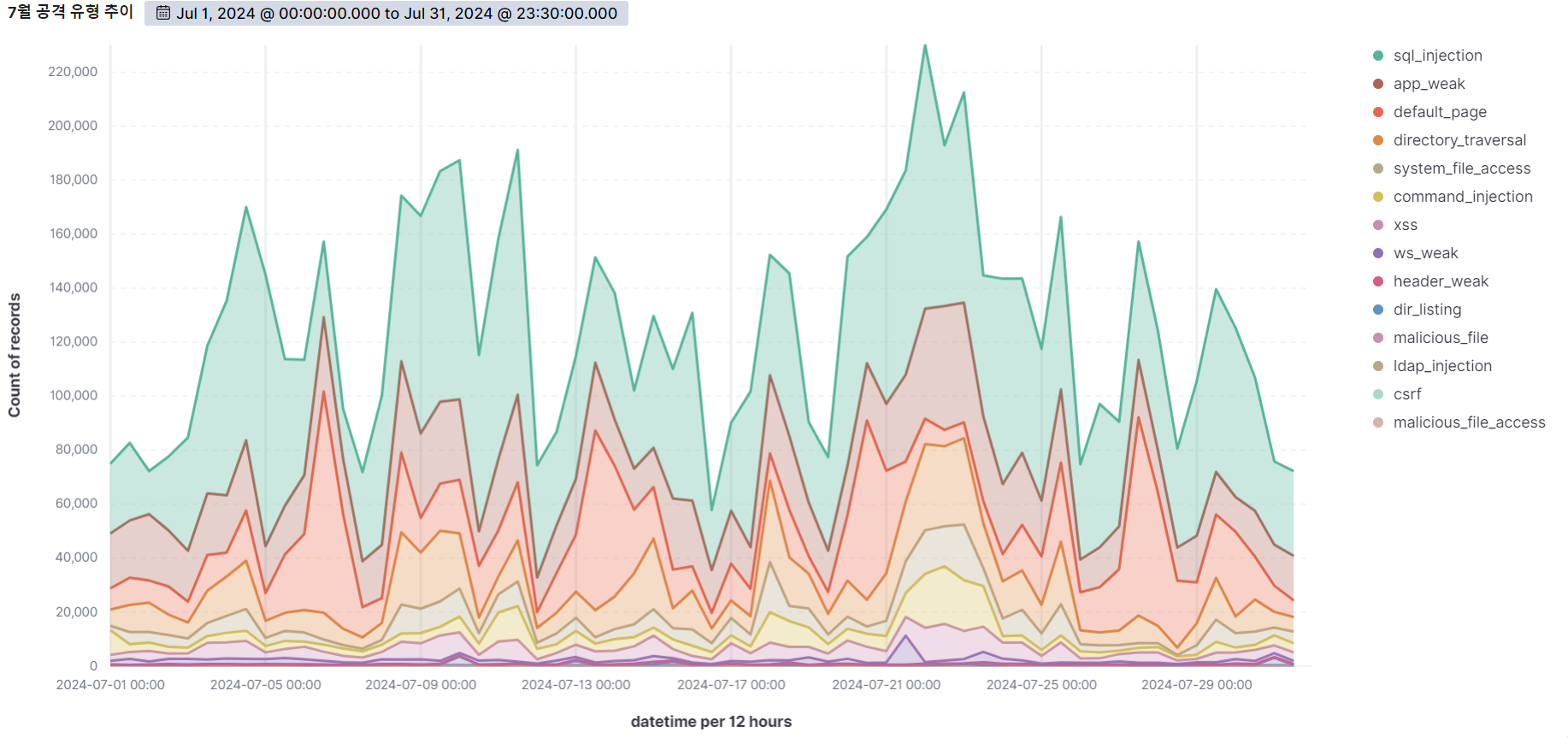
July
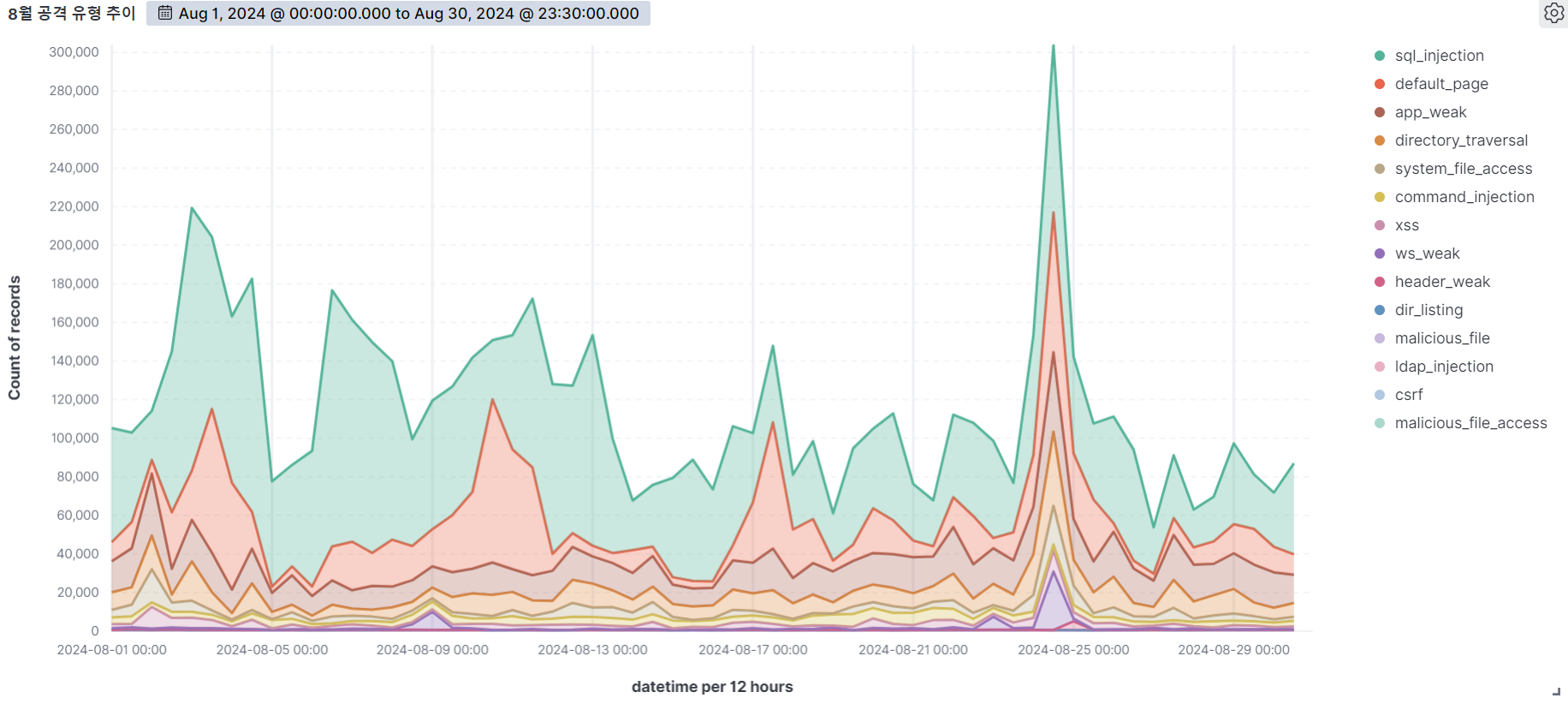
August
Top 30 Attacker IPs

Vulnerability analysis reports
[Jenkins Arbitrary File Read]
1. Overview
Jenkins, a tool used to automate tasks such as building, testing, and deploying software, was analyzed for CVE-2024-43044, a file read vulnerability in the tool.

2. Attack types
The architecture of Jenkins consists of Jenkins Agents and a Controller that coordinates the management, job scheduling, and monitoring of those Agents. The communication between Jenkins Agent and Controller uses the Remoting library, which communicates via its own protocol or SSH.
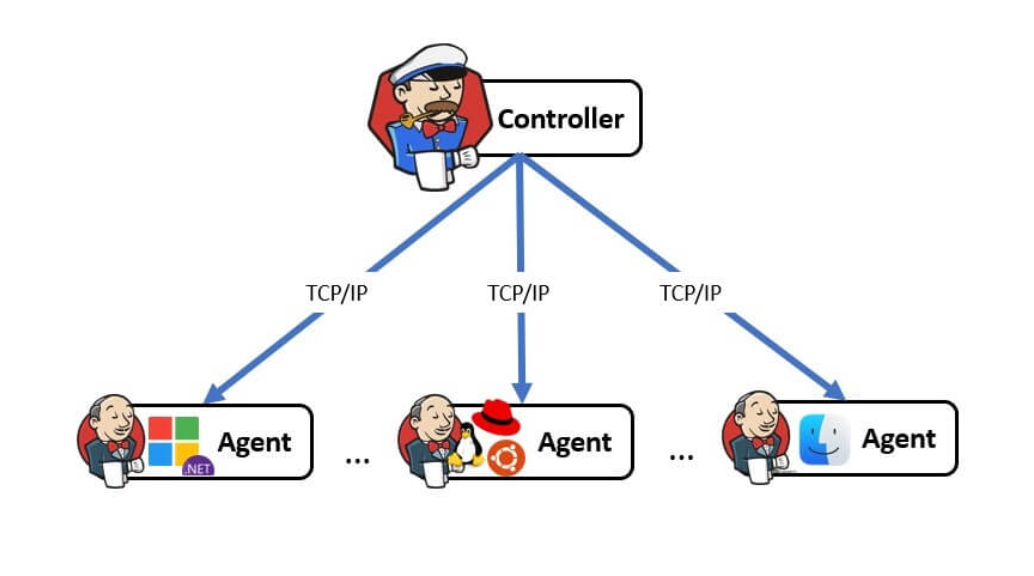
Source : https://blog.convisoappsec.com/en/analysis-of-cve-2024-43044/
This vulnerability allows the Agent to access and read arbitrary files within the Controller, because some code in functions within the Controller does not restrict the path of the request when the Agent requests files it needs from the Controller file system.
Therefore, an attacker can gain access to the Agent by obtaining the agent.jar file or leaking credentials via the remoting.jar file to obtain the agent name and secret information, connect to the Controller using the Remoting library, a communication library, and call the vulnerable instance, hudson.remoting.RemoteClassLoader, to access arbitrary files.
The vulnerability can be leveraged to steal information about a specific user, create a Remomber-Me cookie based on that information, and gain access to the Jenkins Scripting Engine to execute malicious commands.
3. What to do
The vulnerability has been patched in Jenkins 2.471, LTS 2.452.4, and 2.462.1, and Jenkins has also provided corrected agent files for Jenkins Controllers that were unfortunately unable to apply the fix.
The vulnerability is in the SSH communication environment, which is a proprietary protocol, and does not appear to be a patternable area for AIWAF.
Source: https://github.com/jenkinsci/remoting/blob/master/docs/protocols.md
4. Conclusion
The file reading vulnerability in Jenkins is easily exploitable by anyone who can access the Agent in any way, and with over 516,000 Jenkins servers exposed as of September 24, 2024, the impact of this vulnerability is high, so you should always keep Jenkins patched to the latest version.
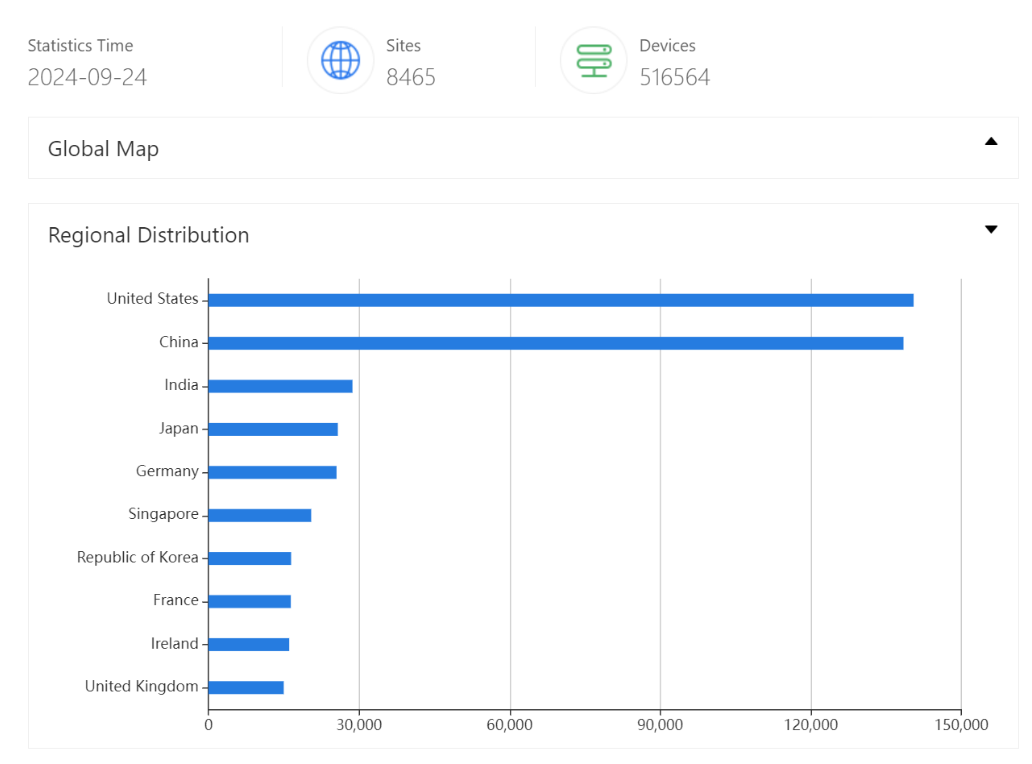
A search for “Jenkins” in ZoomEye resulted in the following
Our AIWAF product continues to monitor for vulnerabilities in Jenkins, and we will continue to respond quickly to relevant vulnerabilities as they are discovered.
5. References
- https://blog.convisoappsec.com/en/analysis-of-cve-2024-43044/
- https://blog.criminalip.io/ko/2024/08/22/cve-2024-43044/
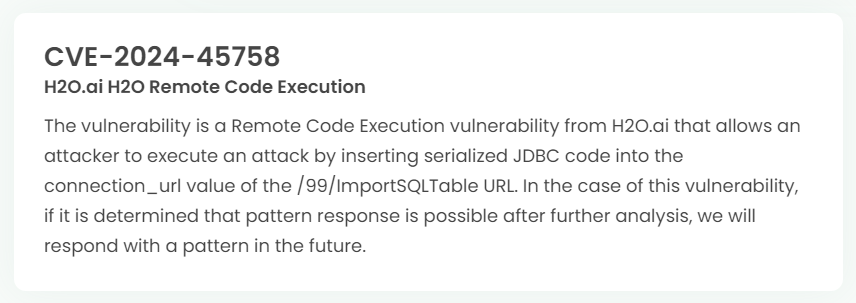
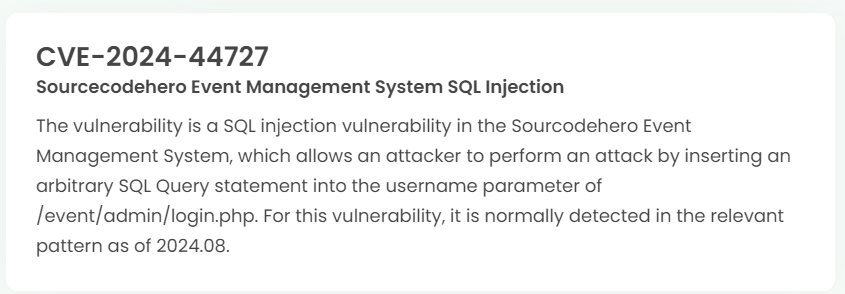
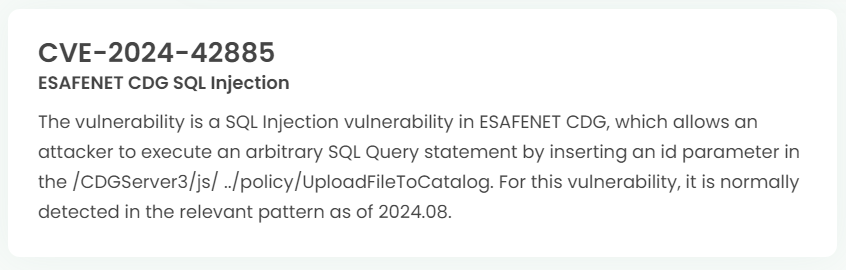
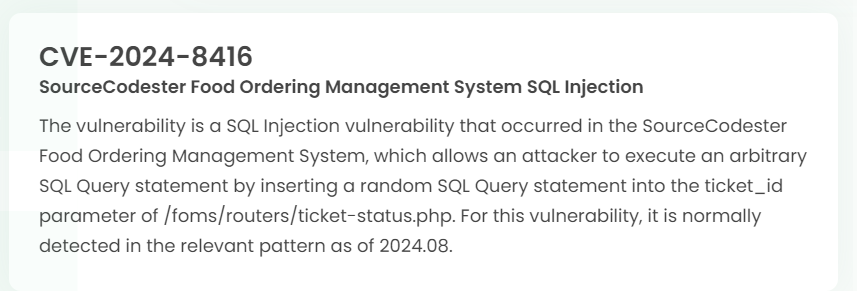
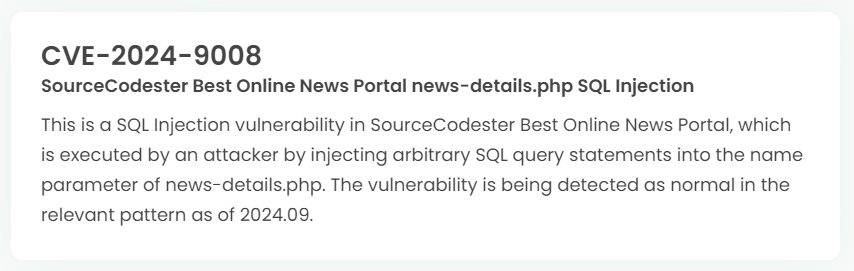
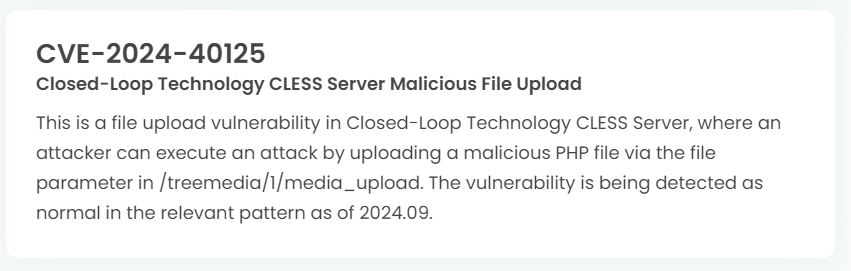
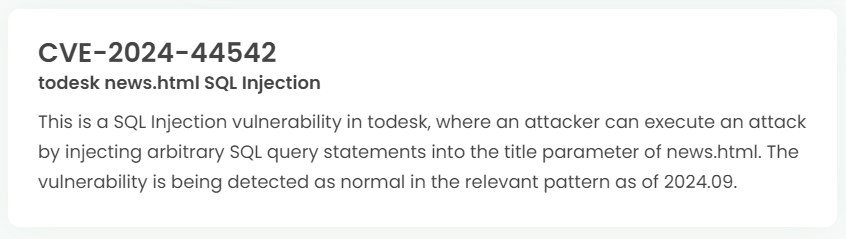
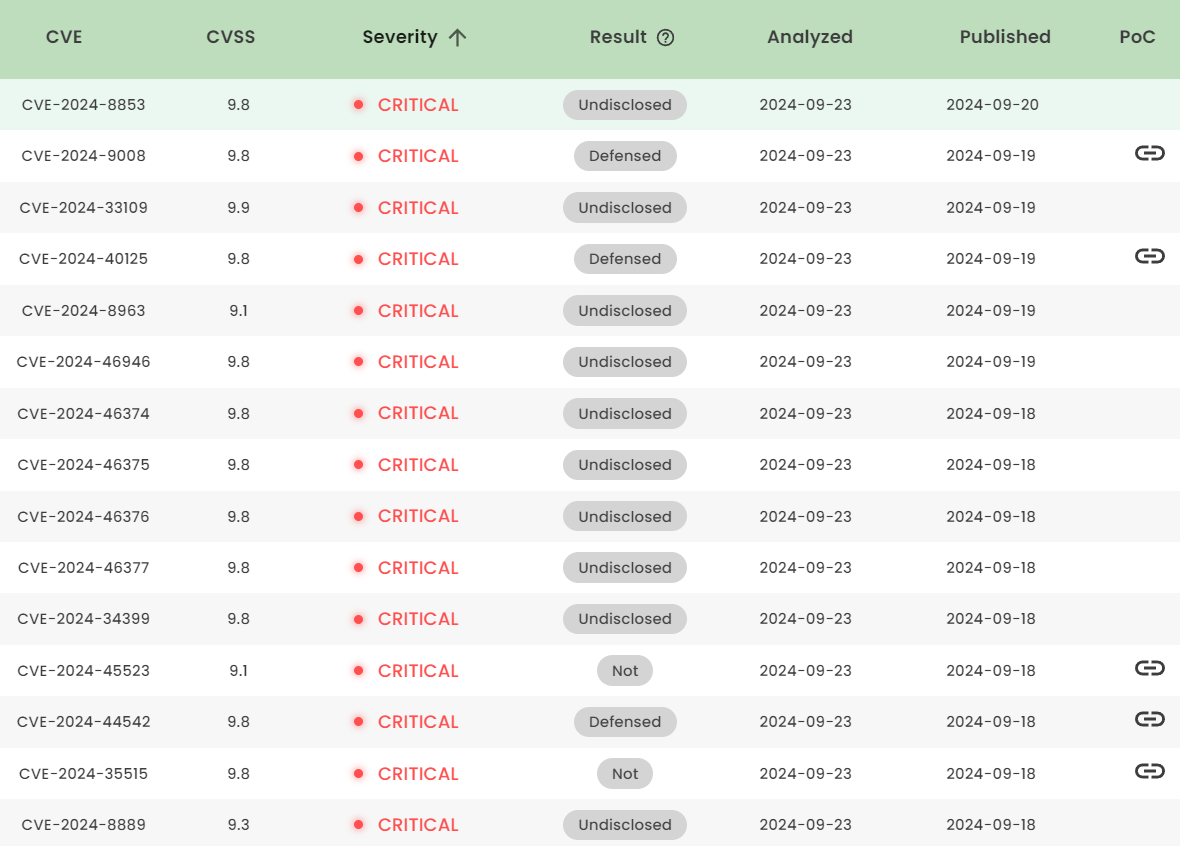
Latest vulnerability CVE status
1. High-risk vulnerability status (2024.09)
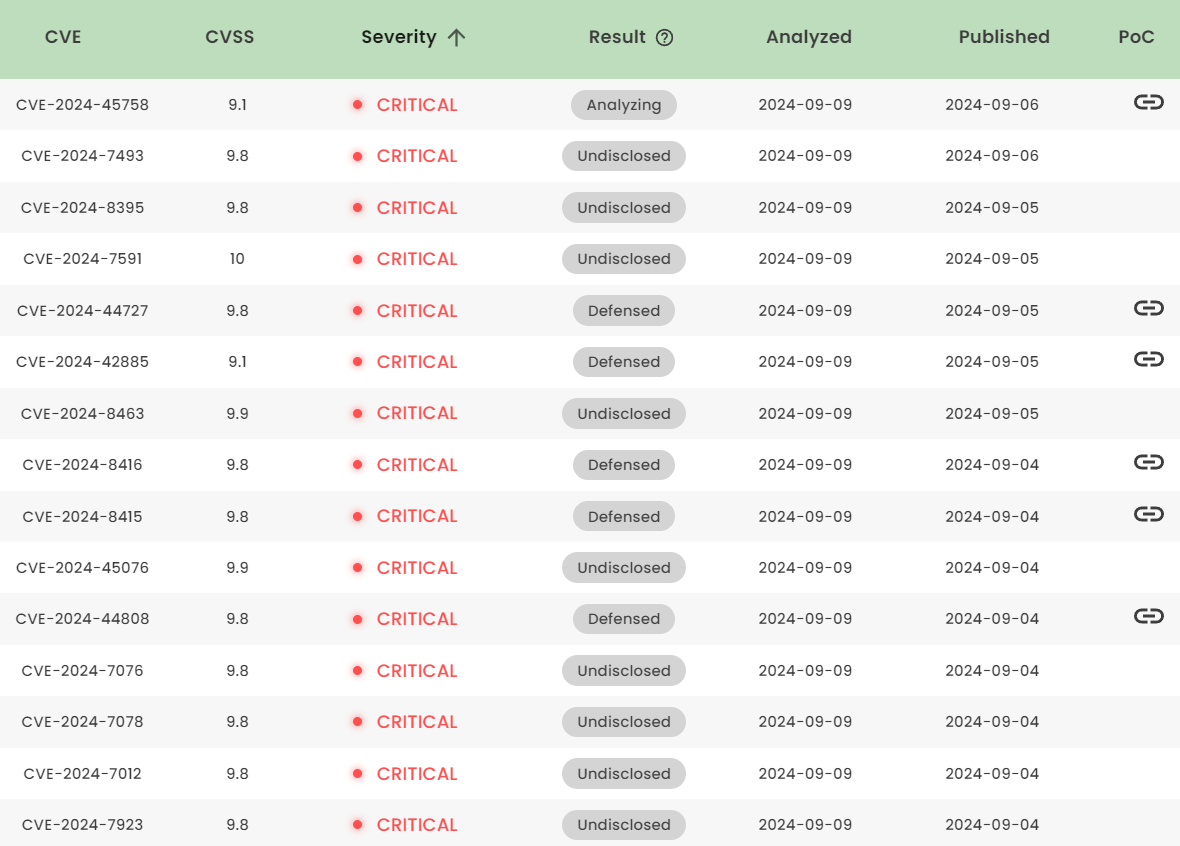
2. High-risk vulnerability descriptions