Hello, this is MONITORAPP.
The traditional network security model centers on perimeter security with firewalls, basically trusting internal users and blocking access from the outside.
However, with the proliferation of cloud services, the rise of telecommuting, and the Bring Your Own Device (BYOD) trend, the lines between internal and external have blurred, and there is a widespread realization that untrusted users can emerge even from within.
This has led to the rise of the “Zero Trust” model, where all access is always verified, not trusted.
The main elements of the Zero Trust model are 'Micro Segmentation', 'Software Defined Perimeter (SDP)', 'Enhanced authentication', and 'Device Posture'.
Following on from each of these key elements, today we'll discuss Device posture.
What is Device Posture?
Device Posture is the concept of assessing the security posture and configuration settings of devices that are attempting to access your network.
It's a way to ensure that a device's health is trustworthy before allowing it to access your network or applications.
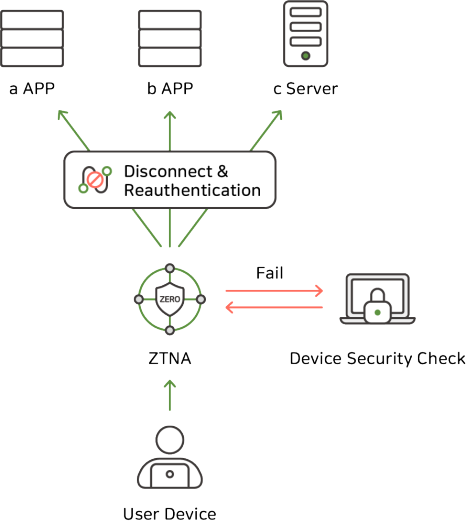
Device Posure is a key component of ZTNA because it goes beyond simple user authentication to evaluate the health of the device being accessed, in line with the Zero Trust model's “don't trust, verify all access” principle.
Device posture enables ZTNA to continuously assess the health of a device to perform thorough validation of all access attempts, creating a tighter defense.
Key features of Device Posture
Check the operating system status

You can check a device's OS version and patches to make sure it's up to date and that updates have been applied.
Based on this, you can set policies to ensure that only users with certain versions and certain OSes can access your network or applications.
Check your antivirus status

By verifying that an antivirus product is installed and running, you can set policies to ensure that only devices that meet your organization's requirements can access your network or applications.
Verify Process

You can see if a specific process (application) is running on a device to assess whether the device is managed by your organization's Mobile Device Management (MDM) or EnterpriseMobility Management (EMM) system.
You can also determine if an unauthorized application is installed or if malicious software is running.
Verify the certificate

By ensuring that devices have specific certificates installed, you can set policies to ensure that only devices that meet your organization's requirements can access your network or applications.
Determine if a firewall is enabled

By ensuring that the firewall is enabled on the device, you can set policies to ensure that only devices that meet your organization's criteria can access your network or applications.
Benefits of Device Posture
Enhanced security
Even for authorized users, insecure devices can pose risks like data leaks and malware infections.
Therefore, it's essential to assess the security posture of your devices to protect your network from potential risks.
Flexible access control
By granting differentiated access to specific users or groups based on device state, you can provide flexibility while enhancing security.
Always-on security
In an environment where the perimeter of the network has disappeared and users and devices are accessible from anywhere, checking device health in real time can minimize security threats.
In this way, Device Posture strengthens security, enables flexible access control, and helps maintain a continuous state of security in today's complex, distributed IT environments.
AIONCLOUD SRA provides the flexibility to set various policies to meet the security needs of the enterprise through the Device Posture feature.
This provides a complete ZTNA service that is optimized for the security needs of the enterprise.
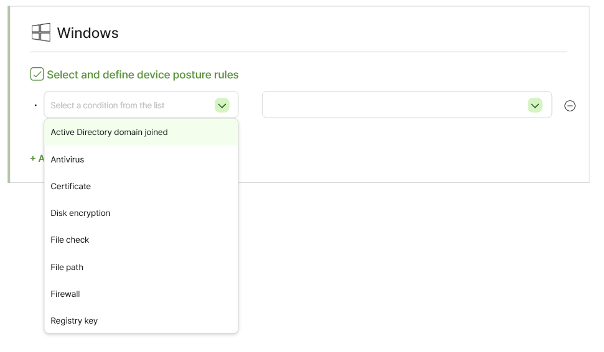
AIONCLOUD SRA includes the main features of Device Posture described above, as well as additional features such as 'Check the existence of specific files', 'Active Directory Domain Joined', which checks whether the device is registered in 'Active Directory' and does not allow unregistered devices to access the network or applications, and 'Serial Number', which checks the device's 'Serial Number' and blocks access to devices that are not registered in advance.
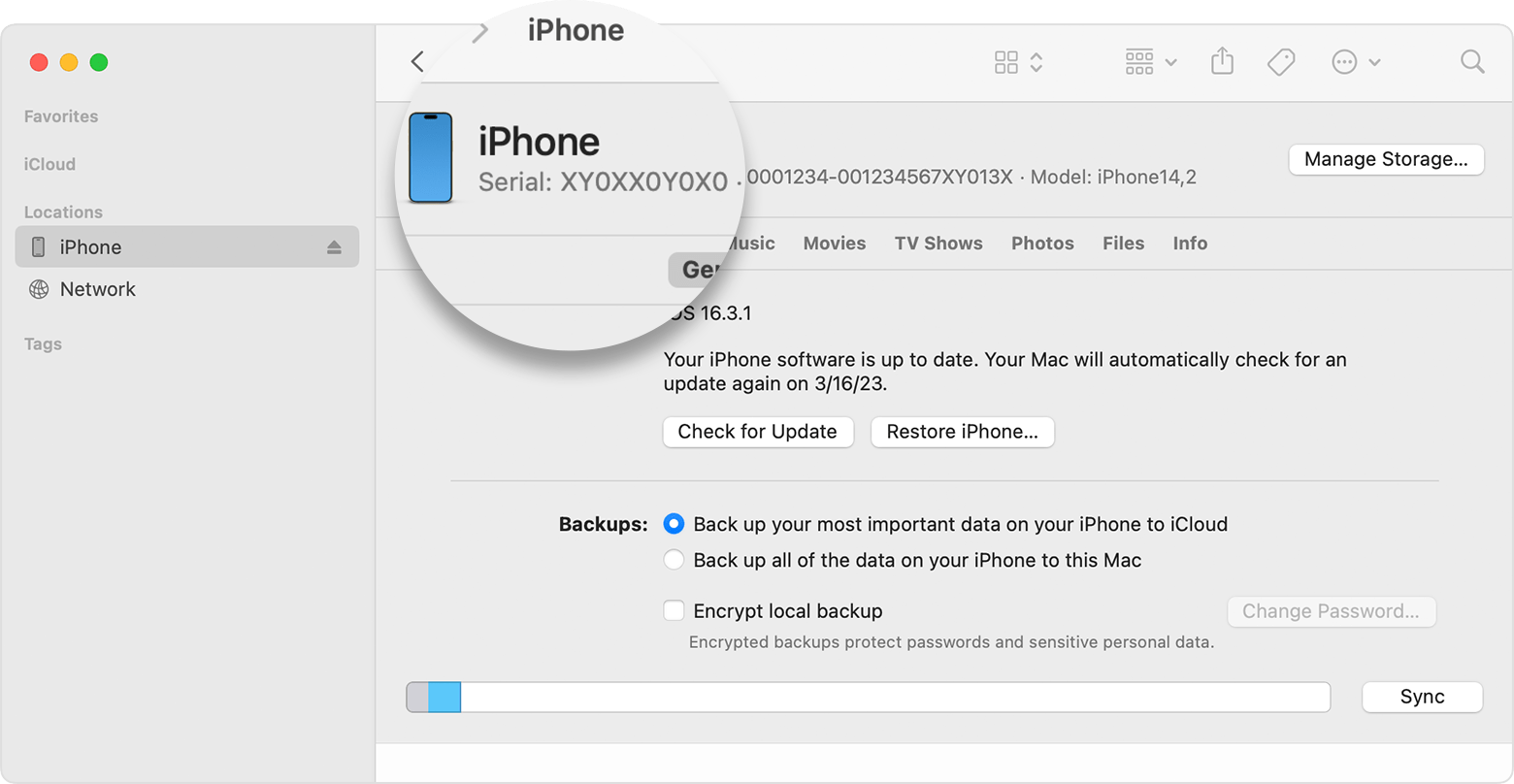
You can also see which devices a user has used, and you can use the device ID to view logs for a specific device.
AIONCLOUD SRA provides thorough security without sacrificing workplace flexibility.
It provides users with secure access to the resources they need, anytime, anywhere, and enables immediate response to security threats with real-time visibility into potential device vulnerabilities.
With AIONCLOUD SRA, your valuable enterprise resources are safe and secure in any situation, anytime.
https://www.aioncloud.com/zero-trust-network-access/


