Hello, this is MONITORAPP.
On December 3, we released Zero Trust Guideline 2.0, which builds on the July 2023 release of Zero Trust Guideline 1.0 and introduces an adoption methodology and adoption level analysis to serve as a practical guide for Zero Trust adoption.
The Korea Zero Trust Committee (KOZETA) is supporting the proposal and utilization of the Zero Trust model through cooperation among information security companies in accordance with the trend of transformation from the existing perimeter security model to the Zero Trust security model.
MONITORAPP is participating in KOZETA as a supplier/developer company that wants to develop a zero-trust security model, and this conference was held to guide the implementation of zero-trust materialized based on the 'Zero Trust Guidelines 2.0' released the day before, and to introduce the zero-trust implementation strategies of KOZETA suppliers, and today I would like to review the scene.
The interest in Zero Trust, the 'hot' security paradigm in the AI era, was also high. Many people arrived early and filled the front seats, and the weather was very cold that day, but it didn't feel cold inside the conference venue because it was hot outside. The monitor lab was also waiting for the conference an hour in advance.
Opening remarks and toasts
The conference kicked off with opening remarks from Hwan Kook Bae, Chairman of the Korea Zero Trust Authority (KOZETA). He explained that Zero Trust is a new security paradigm that demand organizations are interested in as remote work and cloud services are activated, and that it is meaningful in that it introduces the introduction of Zero Trust solutions through cooperation between companies rather than a single company, and said that he will strive to provide opinions necessary for the activation of Zero Trust in Korea
After that, Cho Young-cheol, Chairman of the Korea Information Security Industry Association, gave a congratulatory speech and said that Korean companies are not creating a single solution to implement Zero Trust, but a solution is being created by collaborating with various companies in a consortium, and that they will do their best to help spread Zero Trust through a lot of publicity as well as recommendations to the government.
Keynotes
Next, Prof. Seokjun Lee of Gachon University's Smart Security Department started with the topic 'Introduction to Zero Trust Guideline 2.0': "Building Zero Trust does not prevent all security incidents. However, it should be viewed from the perspective that even if an attack occurs, the damage and propagation can be minimized. We don't want you to think of it as an absolute solution, but rather as a good reference model that you can use to strategize as you find your way to the right answer."
SECTION1.
Security solution alignment,
the key to modernizing Zero Trust
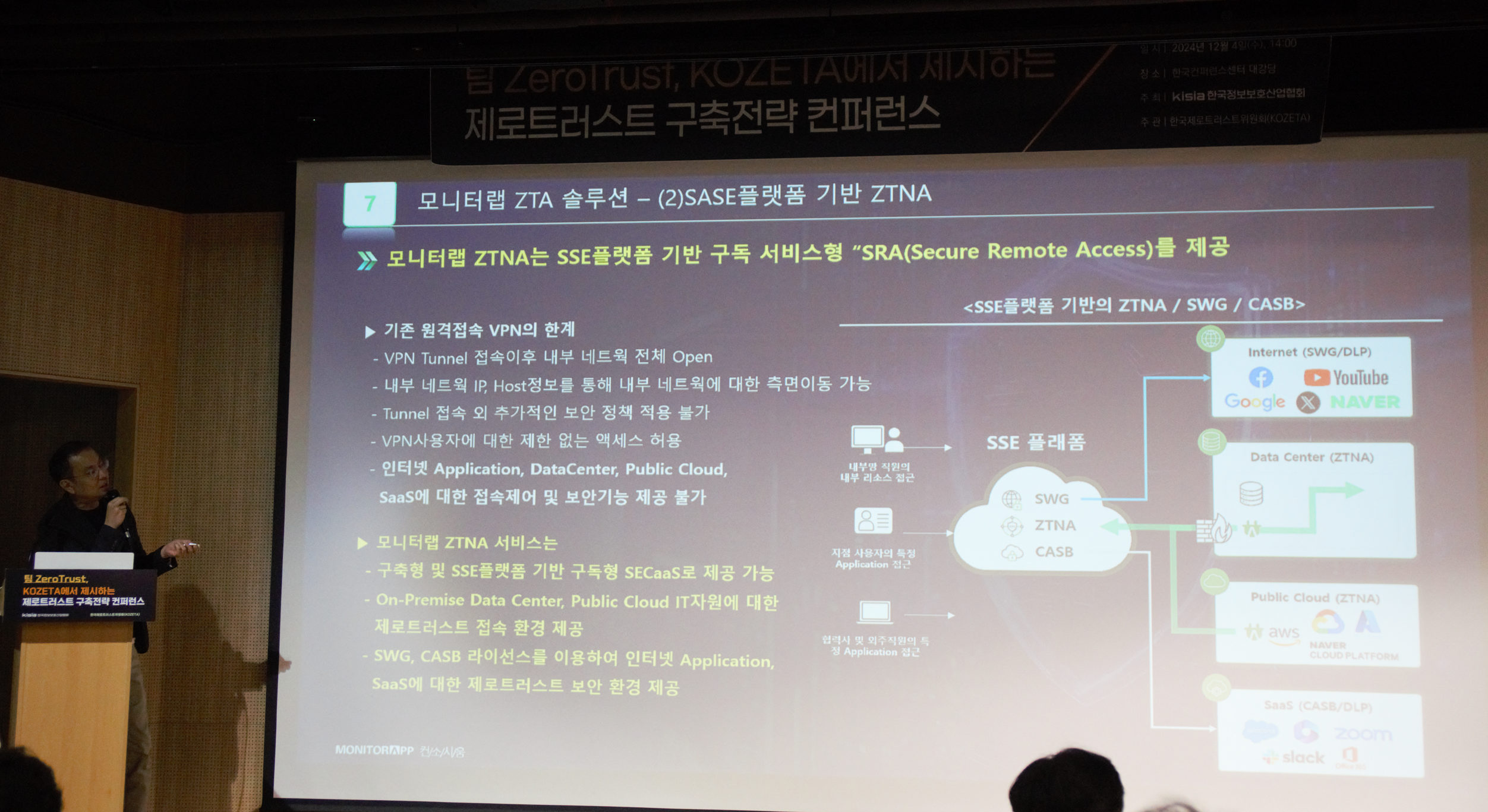
Citing the limitations of existing perimeter security as an example, the introduction of cloud environments, the spread of remote/home-based intelligent attacks, the need to introduce a zero-trust architecture due to changes in the IT environment, and the rising cost of operation/management and solution introduction due to the decentralized deployment of multiple point security solutions at all perimeters, MONITORAPP presented a security solution with zero-trust-based NW, EndPoint, and Cloud integration through AIONCLOUD SASE, and presented the need to change the existing on-premise-centered security as an example of the limitations of traditional VPN security.
The international market for Zero Trust is expected to grow at a CAGR of 17.3% over the next five years, and by 2025, 60% of enterprises/organizations will have internalized Zero Trust as a starting point for security. Many overseas vendors have already configured Zero Trust security architectures for on-premises and cloud-native environments based on edge computing by linking SASE/SSE/CCNAPP, and models related to integrated security service delivery (Cisco, Paloalto, ZSCaler, CLOUDFLARE) are proliferating.
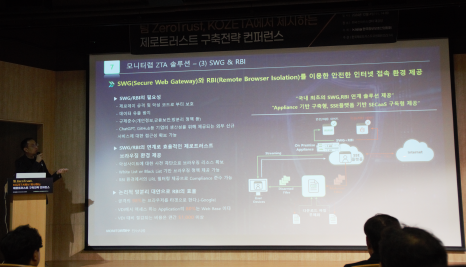
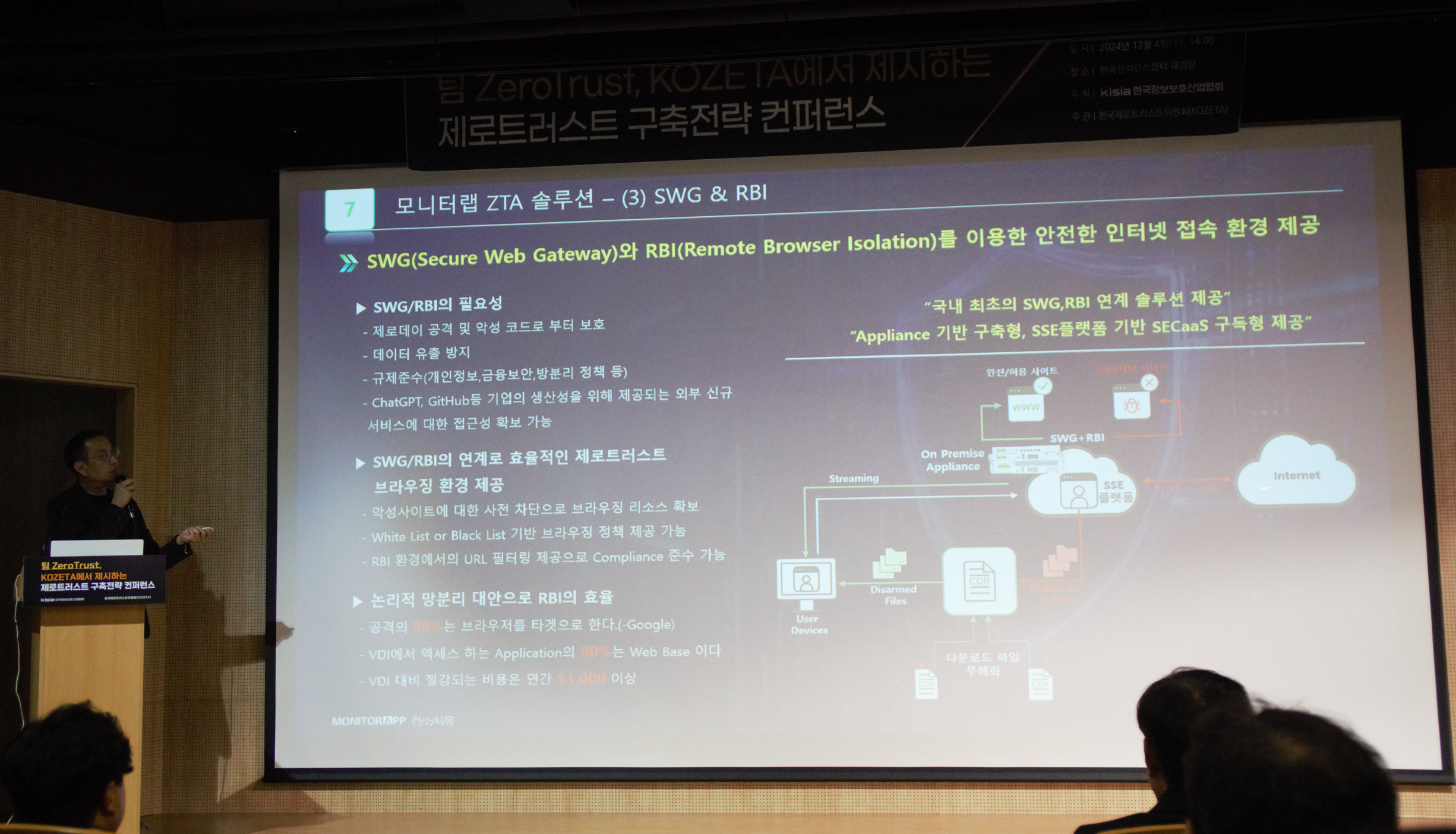
MONITORAPP ZTNA then emphasized the need for SWG and RBI as a logical network segregation alternative that can overcome the limitations of existing remote access VPNs by providing Secure Remote Access (SRA), a subscription service based on the SSE platform.
98% of attacks are browser-targeted,
80% of applications accessed in VDI are web-based,
and savings over VDI are more than $1,000 per year
In addition to the Monitor Lab, each consortium presented models and deployment strategies for implementing Zero Trust.
Looking forward to Zero Trust 2025!
With the recent deregulation of network disaggregation, zero trust security has become a hot topic, and MONITORAPP has been preparing various zero trust security solutions to help many financial, public, and enterprise organizations implement a clear zero trust security system.