Weekly web attack trends
Weekly web attack trends allow you to see when web attacks are most prevalent. This can help you plan ahead to prevent and respond to web attacks during peak periods.
The graph below shows the web attacks detected by AIWAF as of December 2024.
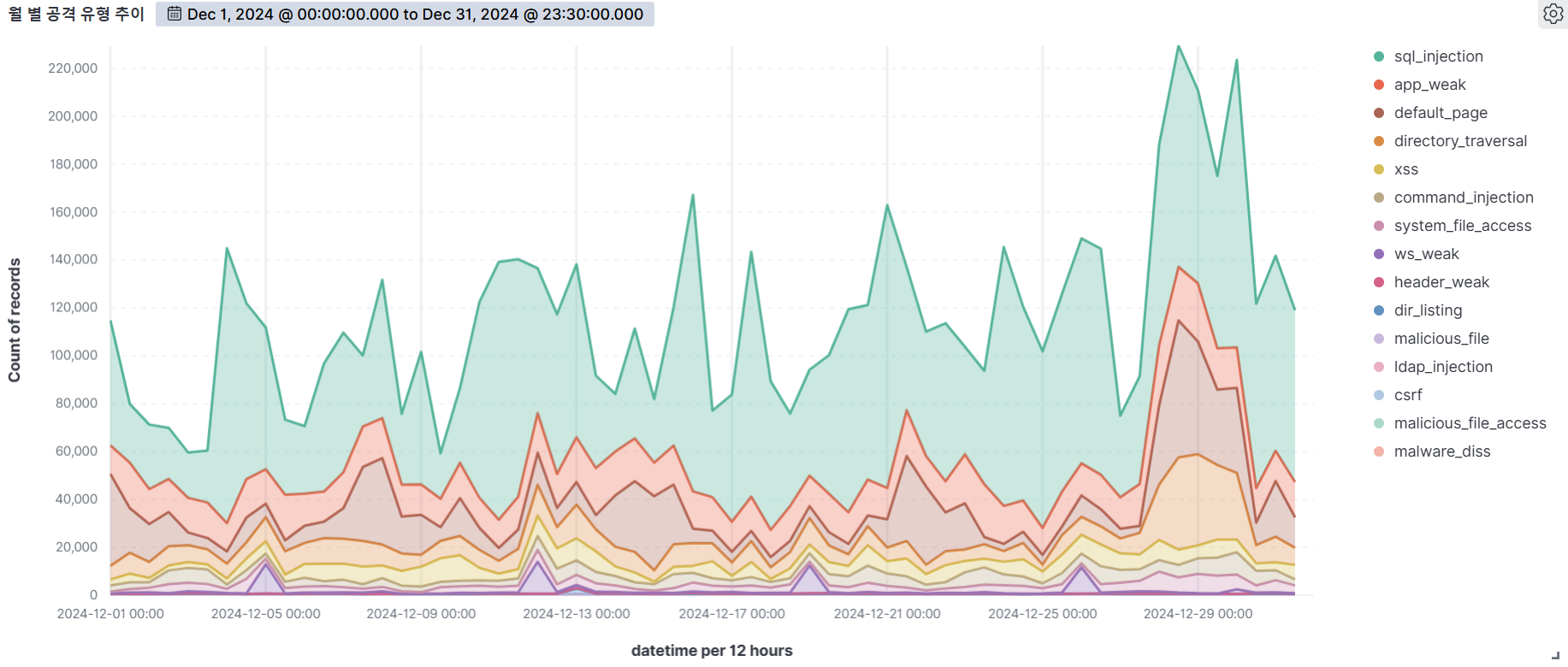
In December 2024, we detected over 240,000 attacks per day on average, with the highest number of attacks occurring on the 28th and 30th.
SQL Injection, the vulnerability with the most attempted attacks on the 28th, has the most detection conditions in our AIWAF. However, SQL Injection attacks are always being monitored because there are many new attack types and workarounds.
Web attack trends by attack type
Web attack trends by attack type, based on detection logs, allow you to see which attacks were most prevalent during the month. Based on this, you can establish basic web attack response guidelines to prevent and respond to these types of attacks.
The graph below shows the web attacks detected by AIWAF as of December 2024.
Web Attack Trends by Rule
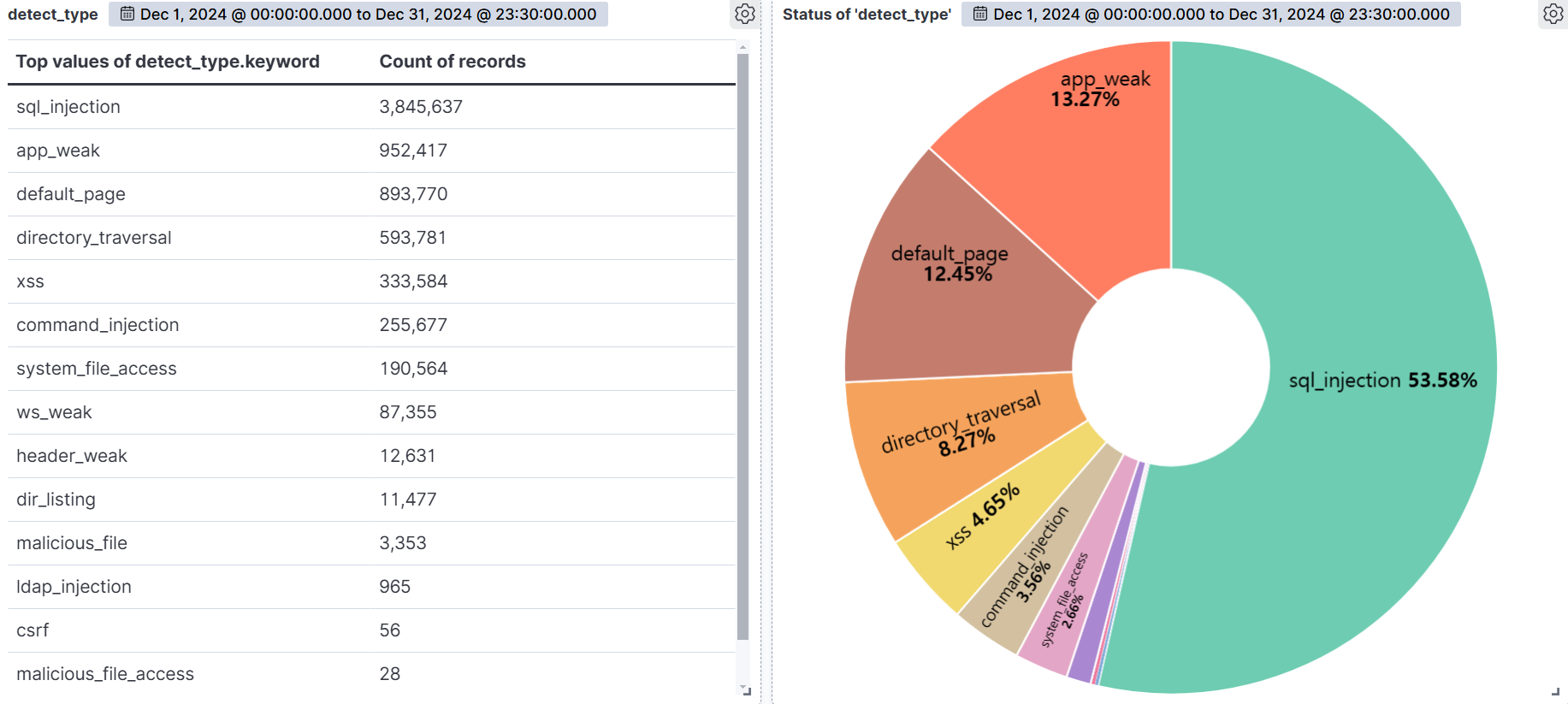
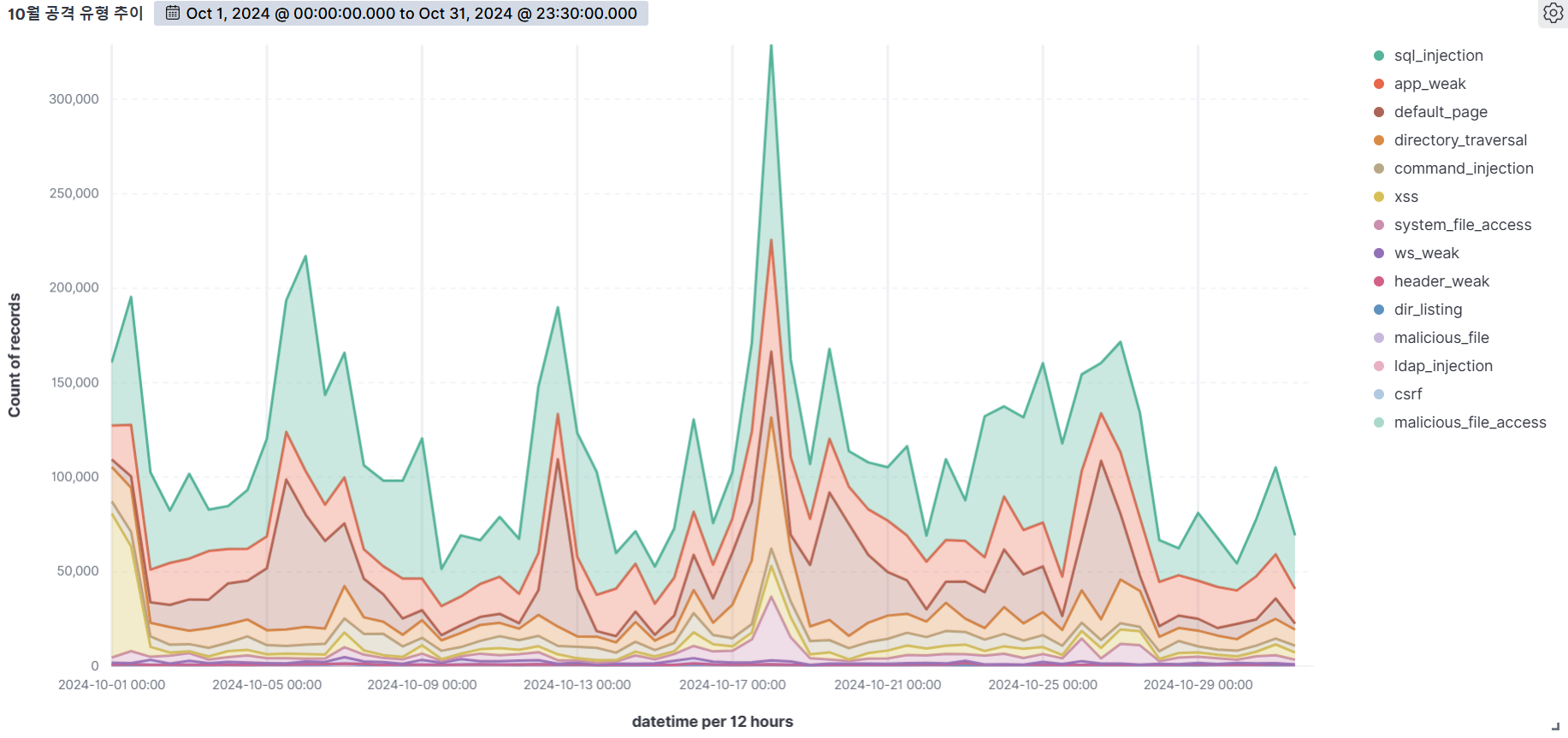
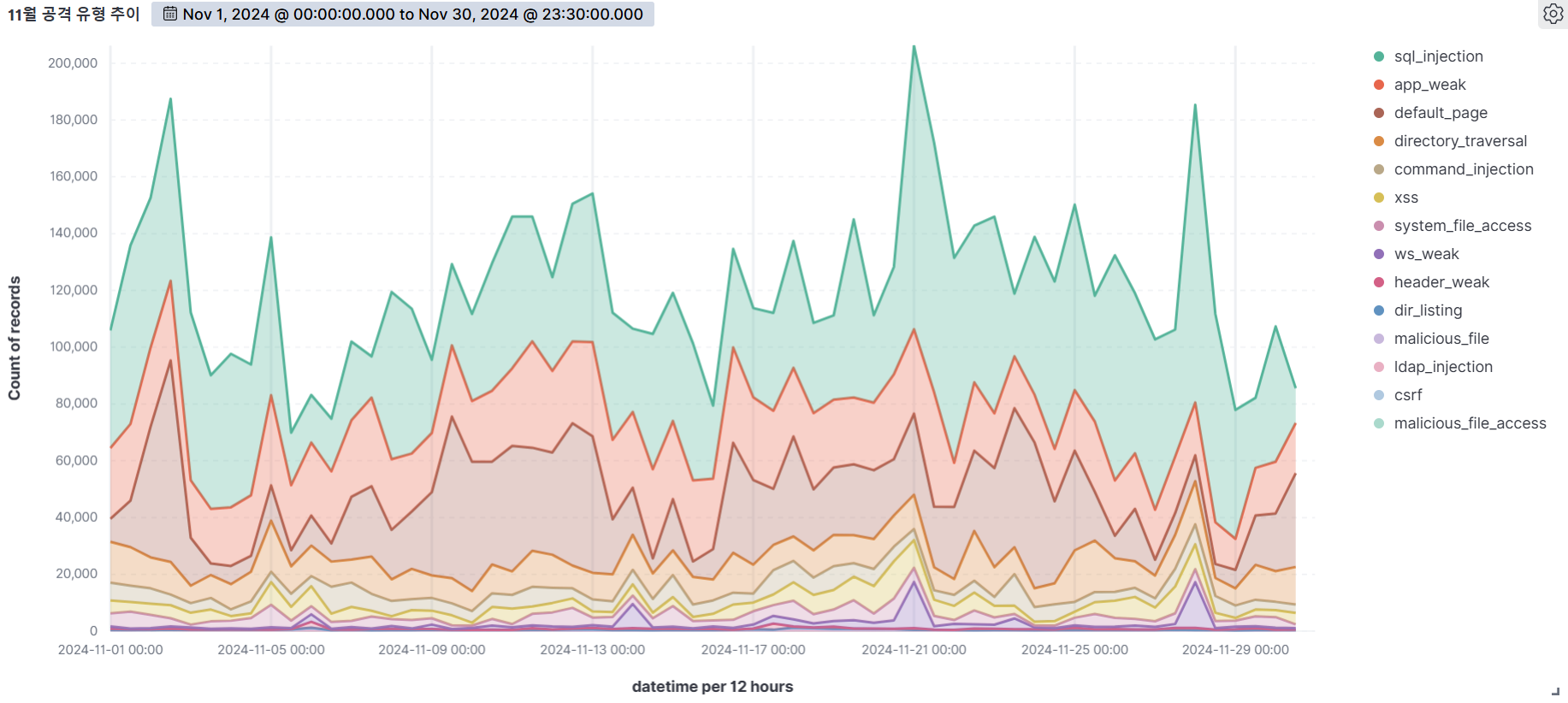
SQL Injection (53.58%) was the most common attack type, followed by App weak (13.27%), Default page (12.45%), and Directory Traversal (8.27%).
SQL Injection is the most diverse and dangerous attack, as it is ranked #1 by OWASP. It is an attack that forces malicious SQL statements into SQL statements that dynamically generate data based on user requests, which can cause vulnerable applications to authenticate or return abnormal SQL results. If you encounter the following syntax in your query values, you should suspect an attack.
APP WEAK indicates a vulnerability within an app that an attacker can exploit to gain unauthorized access or perform malicious actions. These vulnerabilities can be the result of poor coding practices, misconfiguration, or insufficient security measures. As a general rule of thumb, be suspicious of unauthorized files in addition to authorized files when using app programs.
Summary of web attack trend graphs for the last 3 months
September
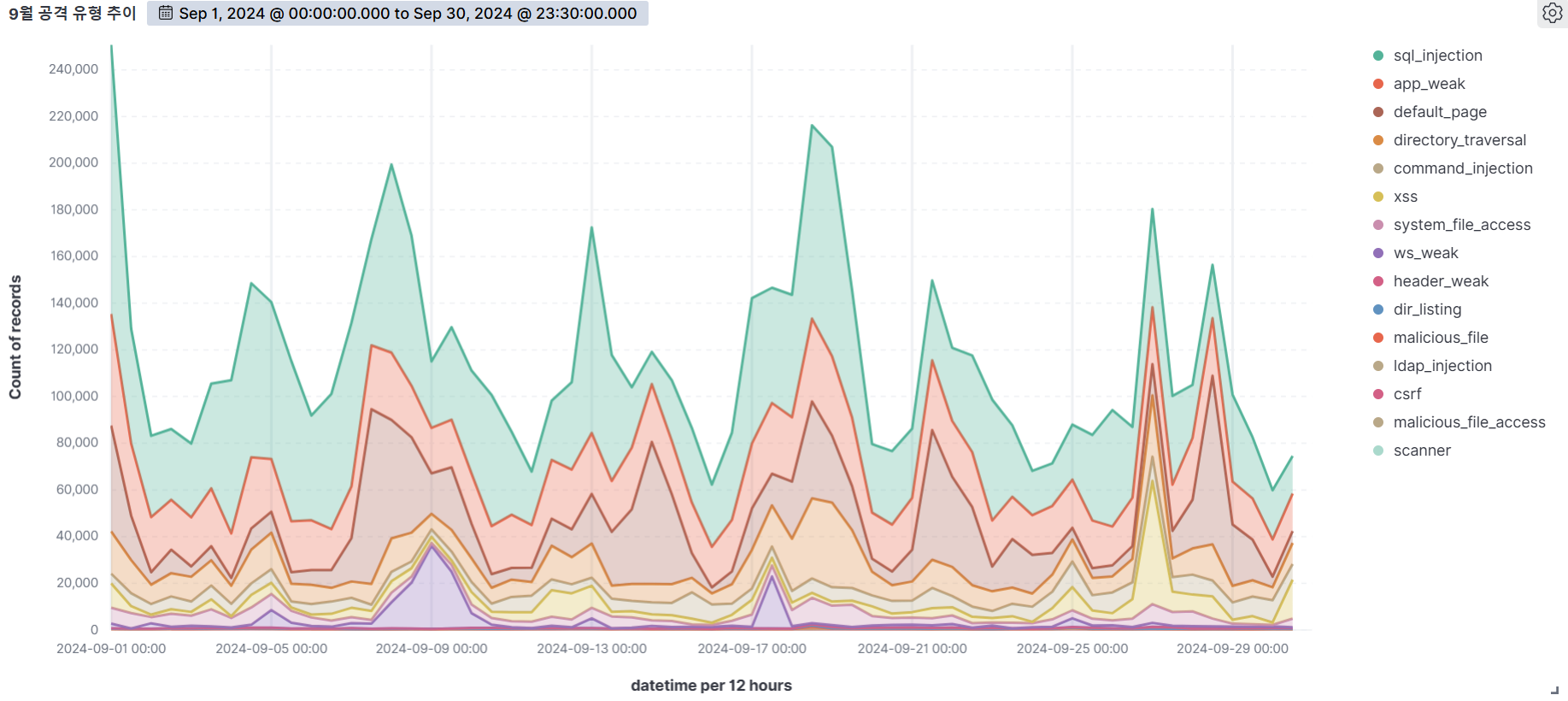
October
November
Top 30 Attacker IPs

Vulnerability analysis reports
Cleo Harmony, VLTrader and LexiCom File Read/Write Vulnerability
1. Overview
Cleo is a software organization that offers a piece of software called Managed File Transfer Solutions and includes features such as Harmony, VLTrader, and LexiCom. In this report, Cleo summarizes our analysis of CVE-2024-50623 and CVE-2024-55956, a file read and write vulnerability in their software.

Source : https://www.helpnetsecurity.com/2024/12/10/cve-2024-50623-cleo-file-transfer-software-vulnerabilities-exploited/
2. Attack types
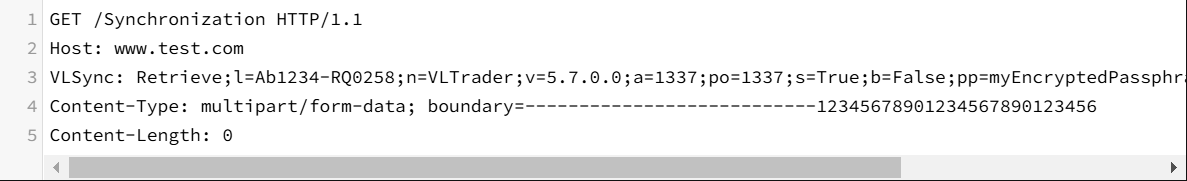
CVE-2024-50623 is a file read and write vulnerability in Cleo Harmony, VLTrader, and LexiCom software that leverages a weak number validation in the /Synchronization endpoint, which handles file synchronization, to either fetch arbitrary file data by sending a crafted VLSync header or write arbitrary files by sending malicious Webshell.
Read the win.ini file using a GET request :
Utilizing POST requests to generate a test.txt file :
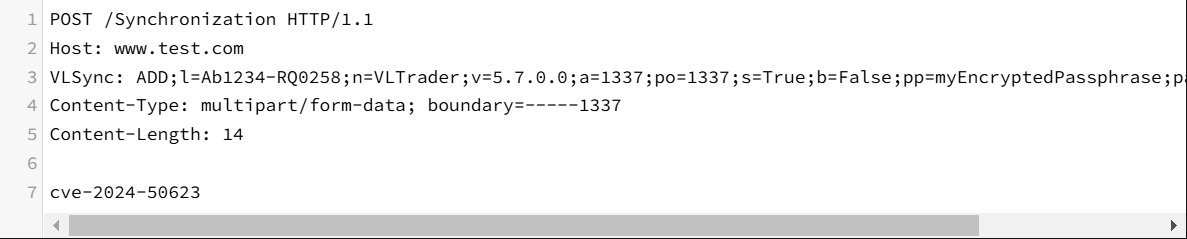
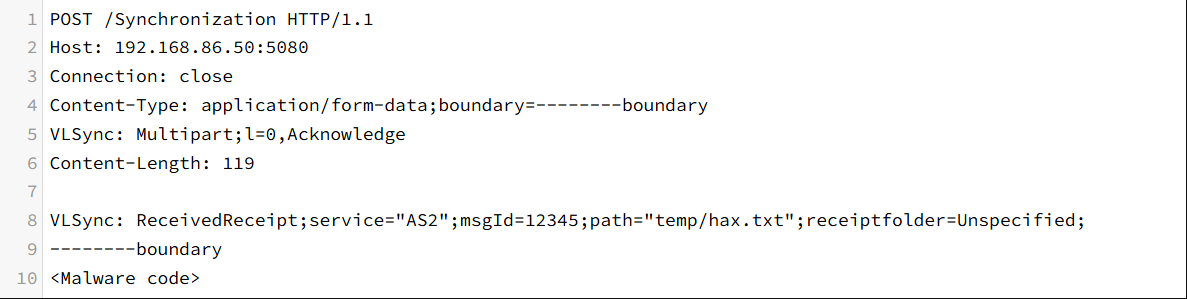
CVE-2024-55956 is a file write vulnerability found in the patched version of CVE-2024-50623, which allows malicious Webshell content to be written to arbitrary files by sending a request with the VLSync: Multipart;l=0,Acknowledge header.
However, this vulnerability is different from CVE-2024-50623 in that it only allows file writes.
Utilizing POST requests to create a temp/hax.txt file :
3. What to do
CVE-2024-50623 is addressed in the Harmony, VLTrader, and LexiCom 5.8.0.21 patches, and CVE-2024-55956 is addressed in the Harmony, VLTrader, and LexiCom 5.8.0.24 patches.
The vulnerabilities appear to be related to sending a request with a crafted VLSync header and will be further analyzed and responded to as a pattern in our AIWAF products.
4. Conclusion
Cleo Harmony, VLTrader, and LexiCom are software that power managed file transfer (MFT) solutions and are used by many large enterprises, and with CISA warning that the vulnerabilities are being actively leveraged in ransomware attacks, customers and enterprises using these software should update to the latest versions as soon as possible.
Our AIWAF products continue to monitor for vulnerabilities in software provided by Cleo, and we will continue to respond quickly to any related vulnerabilities that are discovered.
Responses include applying the latest security patches for affected versions, tightening access controls at the server level, and blocking data through a web application firewall (WAF).
5. References
https://labs.watchtowr.com/cleo-cve-2024-50623/
https://attackerkb.com/topics/geR0H8dgrE/cve-2024-55956/rapid7-analysis
https://socradar.io/cleo-file-transfer-vulnerabilities-cl0ps-attack-vector/
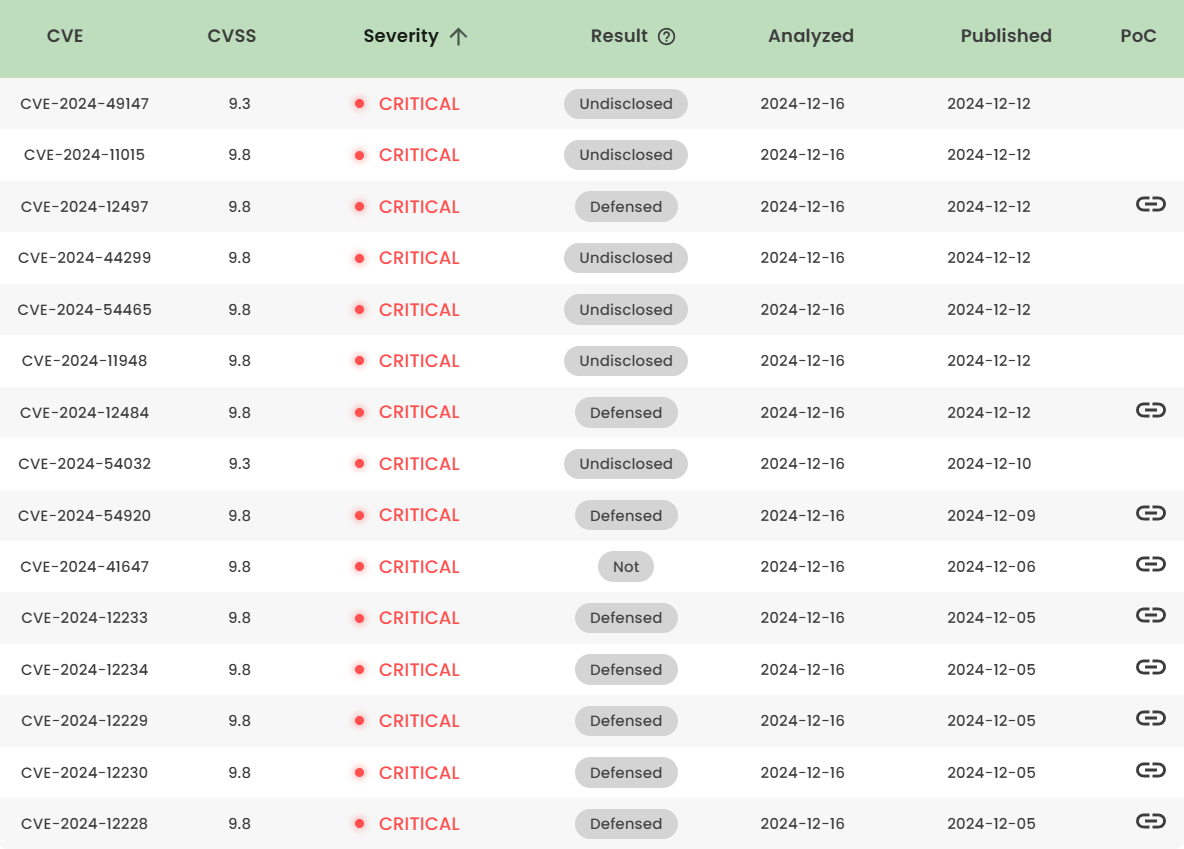
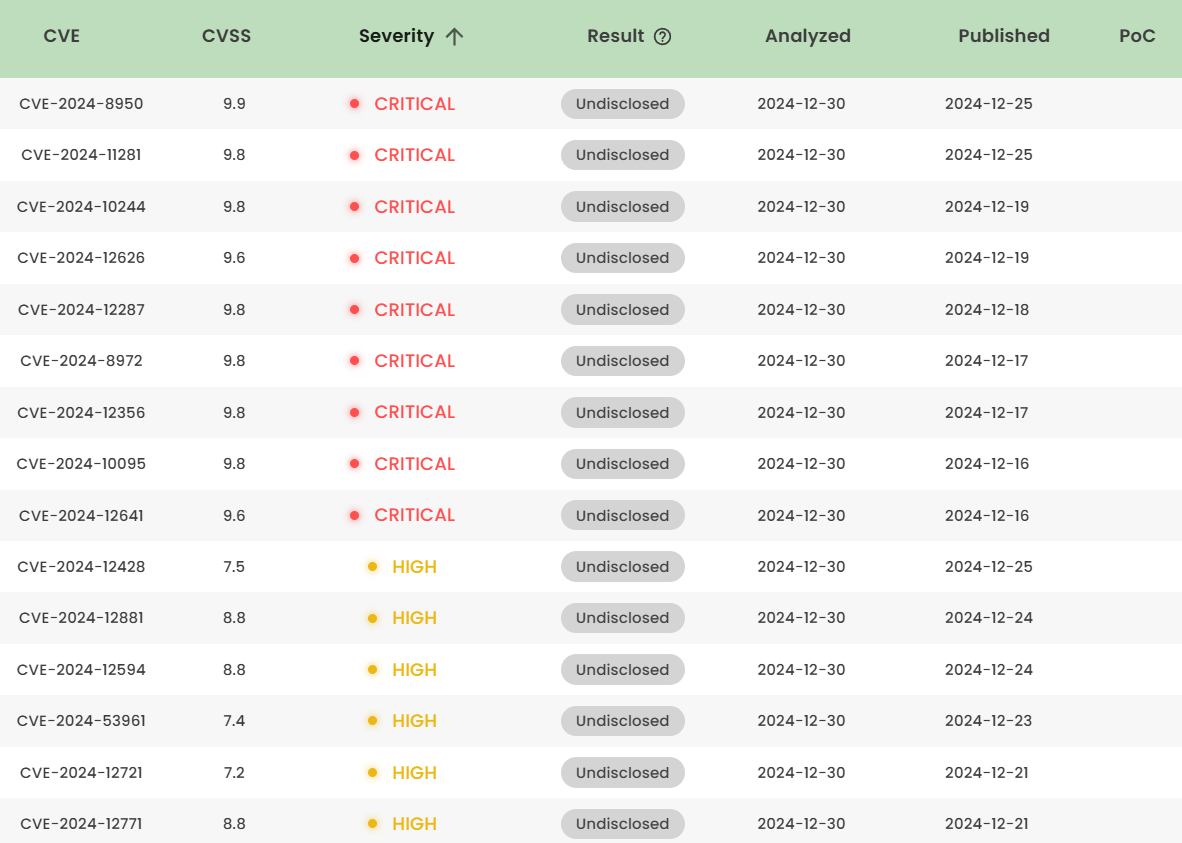
Latest vulnerability CVE status
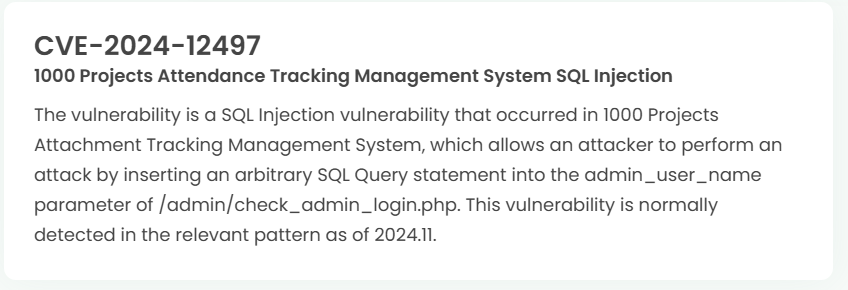
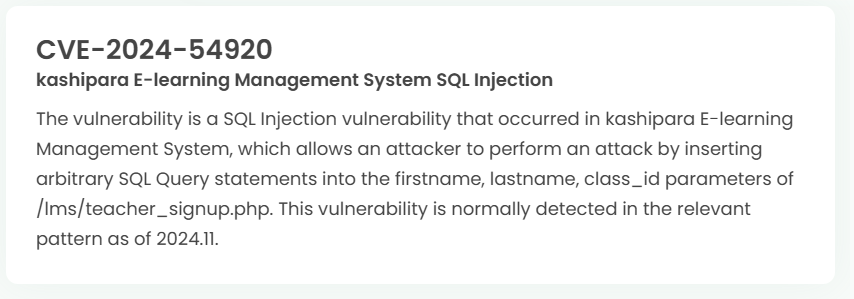
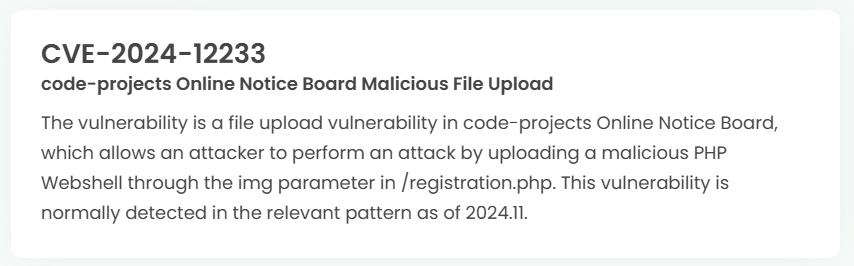
1. High-risk vulnerability status (2024.12)
2. High-risk vulnerability descriptions