
In today's web production environments, security is a necessity, not an option.
AIONCLOUD Website Protection offers two main solutions to meet these security needs: a WAAP solution that defends inline real-time traffic and a WMS that performs regular website security assessments and monitoring.
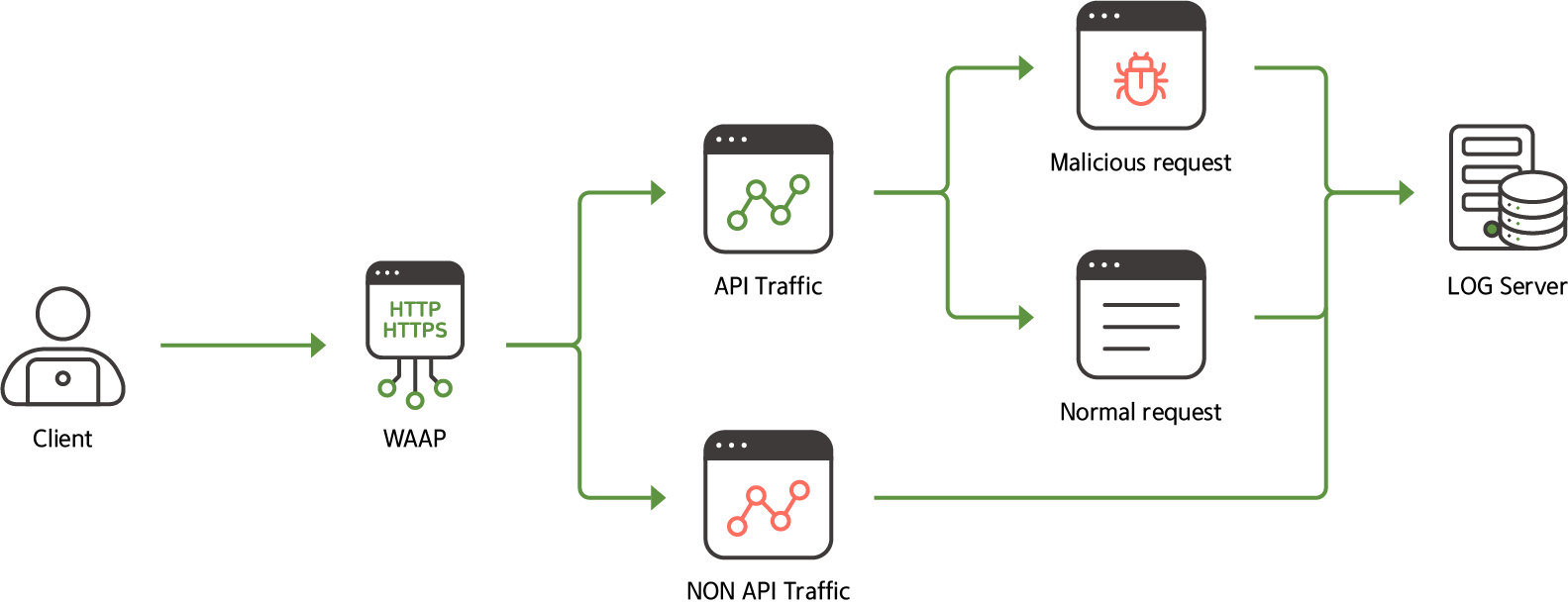
AIONCLOUD WAAP is a web application and API protection solution,
It integrates various features such as API security, bot management, DDoS protection, and user behavior analysis to ensure the safety of web applications and APIs, including common web attacks such as SQL injection and cross-site scripting (XSS).
AIONCLOUD WMS provides comprehensive security assessment and monitoring of your website.
With features such as scanning for malware infections, certificate forgery monitoring, DNS record forgery monitoring, and web vulnerability diagnostics, this service helps you continuously check the security status of your website and proactively detect and respond to potential threats.
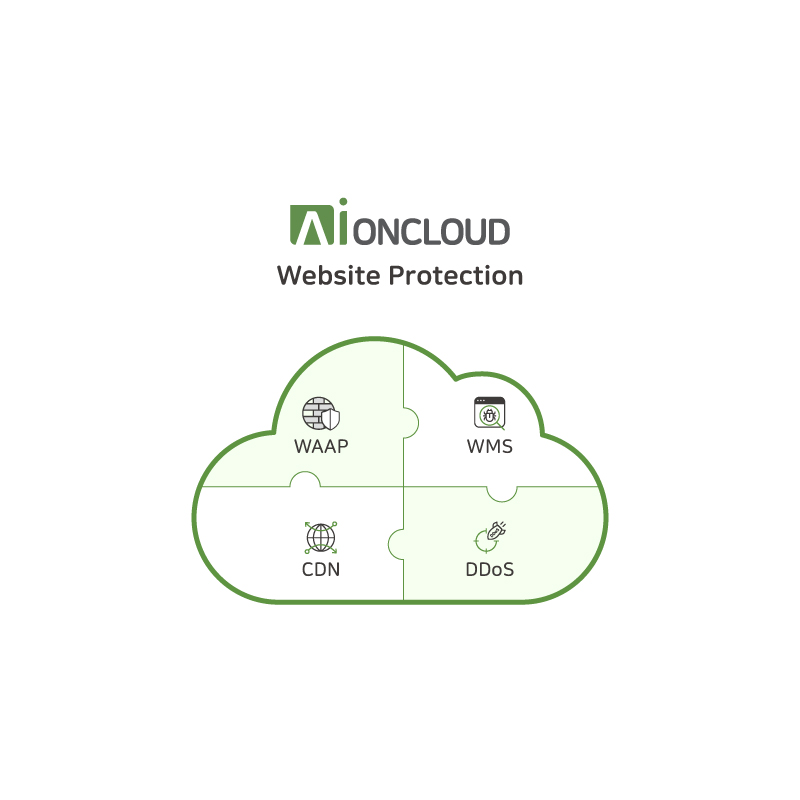
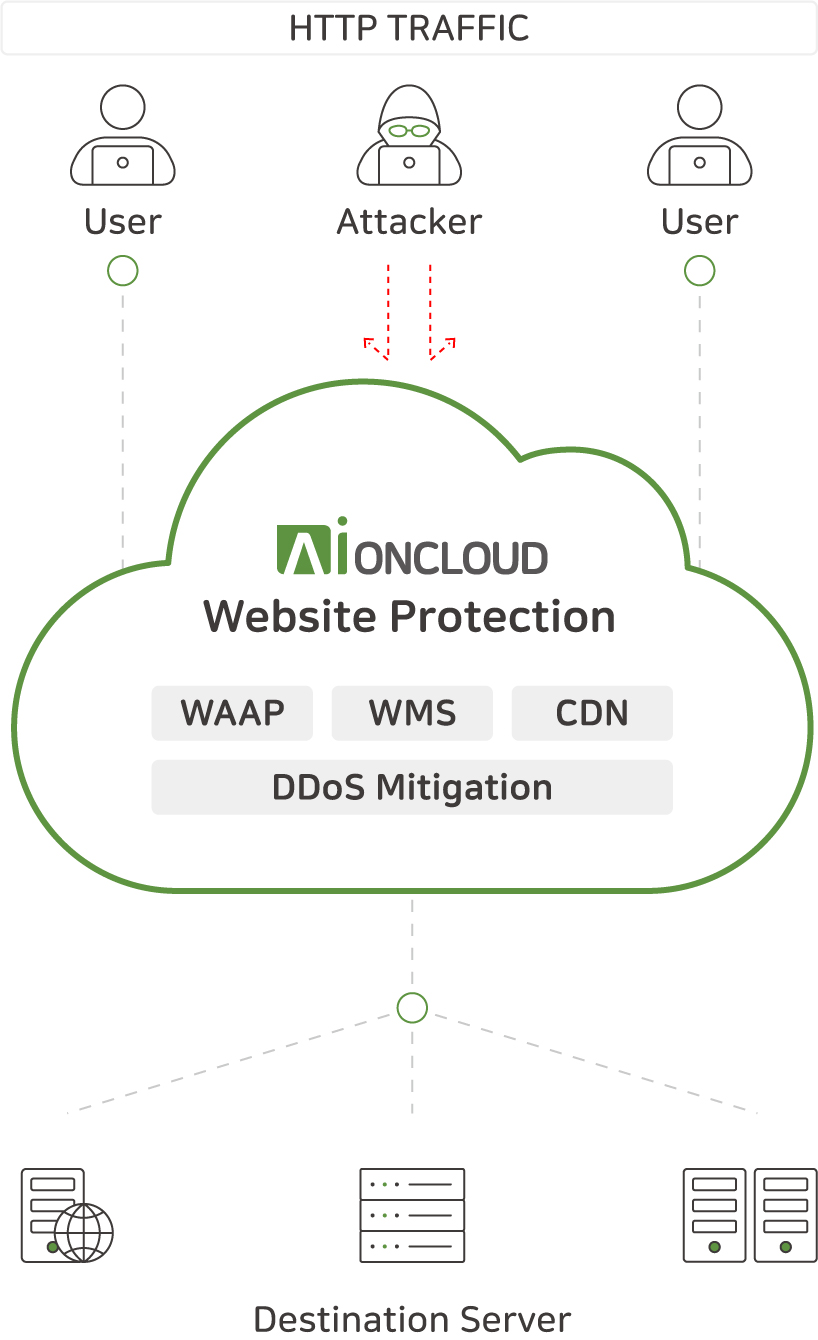
Website Protection, AIONCLOUD's integrated web security service, enables enterprises to assess and systematically manage the overall security posture of their websites in addition to real-time protection of web applications and APIs.
AIONCLOUD WAAP(Web Application and API Protection) : Real-time inline traffic defense
Web application firewall (WAF) solutions have been a staple of web application security since their inception.
WAFs have primarily focused on blocking common web attacks such as SQL injection, cross-site scripting (XSS), and more.
However, with the increasing complexity of web applications and the shift from monolithic to microservices architectures, the use of APIs has skyrocketed.
This has increased the importance of securing APIs, making it difficult for traditional WAF capabilities to meet these new security requirements.
As the security industry has evolved, so have cyber threats, resulting in new attack vectors.
Attacks targeting APIs, malicious bots performing crawling and scraping, and large-scale distributed denial of service (DDoS) attacks have emerged as major threats to the availability and security of web applications.
The rise of cloud computing has also increased the need for cloud-native security solutions.
Security solutions were required to provide cloud-based scalability and global coverage while reflecting the latest threat information in real time.
This is where web application and API protection (WAAP) solutions based on cloud infrastructure come into play.
WAAP solutions extend the capabilities of WAFs to incorporate features such as API security, bot management, DDoS protection, and user behavior analytics (UBA) to address the wide variety of security threats that arise in modern web application and API environments.
What is a WAAP solution?
A WAAP solution is a unified security platform that protects web applications and APIs from cyberattacks.
It extends the capabilities of a traditional web application firewall (WAF) to include API security, bot management, DDoS protection, and user behavior analytics (UBA).
WAAP solutions are cloud-based and provide real-time threat detection and response to protect your organization's digital assets.
1. Key features

Web Application Firewall (WAF)
· Defend against common web attacks, including SQL injection, cross-site scripting (XSS), and more.
· Respond quickly to new threats with continuous rule updates.
API Protection
· Monitor API traffic, detect and block abnormal access attempts.
· Integrate with API gateways to enforce security policies such as authentication, authorization, rate limiting, and more.

DDoS Mitigation
· Detect and mitigate large-scale traffic attacks.
· Maintain service availability with cloud-based scaling capabilities.
Managing bots
· Block access from malicious bots and manage interactions with legitimate bots.
· Analyze bot activity to defend against automated attacks.
User Behavior Analytics(UBA)
· Detect unusual activity by distinguishing between legitimate users and attacker behavior patterns.
· Utilize machine learning algorithms to proactively block advanced attacks.
2. Value
Integrated protection
WAAP solutions provide many of the security features required for web production environments on a single platform for ease of management.

Cloud-based
Leverage cloud infrastructure to provide global coverage and reflect the latest threat intelligence in real time.
Scalability
It's flexible enough to scale as your business grows, and it's effective at handling large volumes of traffic.

Cost-effectiveness
It's more cost-effective than traditional on-premises security solutions and requires less upfront investment.
3. Adoption stories
Ecommerce companies
To protect customer data and defend against shopping cart hijacking attacks, they implemented a WAAP solution and are successfully running it.
Financial institutions
We are leveraging WAAP solutions to protect sensitive financial data and enhance transaction security through APIs.
Healthcare organizations
To protect patient data and enhance the security of healthcare applications, we implemented a WAAP solution.
4. AIONCLOUD Website Protection - WAAP
AIONCLOUD's WAAP solution provides robust web application and API protection as well as a content delivery network (CDN) to enhance security and performance at the same time.
The combination of WAAP's real-time attack defense and CDN's global content distribution ensures fast loading speeds and high availability of web applications.
This allows organizations to provide a vastly improved user experience for website visitors while staying safe from security threats.

AIONCLOUD WMS(Website Malware Scanner): Integrated website security assessment and monitoring
In the digital age, website security is essential to the credibility and sustainability of your organization.
While many companies focus on inline real-time traffic defense, website security assessment and monitoring services are equally important.
AIONCLOUD fully recognizes this need and offers a wide range of security features through its website security assessment and monitoring solution, WMS.
WMS helps you manage security by systematically analyzing the underlying causes and problems of your website, and proactively detect and respond to potential threats.
1. Core technologies
The WMS solution is based on the Malicious URL Detection (MUD) engine, a core technology of the MonitorLab Cyber Threat Intelligence (CTI) platform, which identifies malicious content by visiting customer websites with a headless browser in the same environment as a real visitor.

Detect malicious files
Quickly and accurately identify downloaded files for maliciousness with a variety of analysis factors, including Anti-Virus, YARA Rule, Cuckoo Snadbox, Similarity Profiling, and more.
Analyzing response data
Signature-based detection of malware found in the body of website response data.
This allows you to proactively identify security threats posed by malware and quickly recognize exploits as transit and distribution points.

Detect visual changes
Save the results of website visits as images to compare possible visual changes.
This process enables you to quickly detect changes to your website and spot anomalies early.

Untrusted external links
Leverage the Content Security Policy and Content Security Policy report only headers to visualize a list of JavaScript, style sheets, and more that link to external websites you don't trust.
2. Key features

Scan for malware infections
Features : Regularly scan your website for hidden malware or malicious files to protect you and your data.
Benefits : Ensure the safety of your website by preventing data breaches, loss of trust, and more that can be caused by malicious files.

Monitoring certificate forgery
Features : Continuously monitor the validity of SSL/TLS certificates and quickly detect forgery attempts to ensure secure communications.
Benefits : Prevent phishing and man-in-the-middle attacks due to certificate forgery, and provide a secure browsing experience for users.

Monitor DNS record forgery
Features : Verify the integrity of DNS settings and records, and monitor them for tampering to prevent attacks such as domain hijacking.
Benefits : Maintain domain authenticity and prevent traffic interception, phishing sites, and more that can result from DNS forgery.

Monitoring block list enrollment
Features : Maintain search engine rankings and visitor confidence by ensuring your website is on the major block lists and providing immediate notification of any issues.
Benefits : Avoid the traffic loss and brand credibility damage that can result from being blocklisted.

Web vulnerability diagnostics
Features : Discover common web application vulnerabilities, including SQL injection, cross-site scripting (XSS), and more, and help you remediate them with detailed reports.
Benefits : Proactively discover vulnerabilities in web applications and quickly fix them to prevent attacks.
3. Value
Inline real-time traffic mitigation plays an important role in defending your website the moment it is attacked.
However, real-time defense alone cannot solve all security issues.
Our website security assessment and monitoring service continuously checks your website's security posture and guides you to proactively detect and respond to potential threats.
Proactive prevention
With periodic security scans and assessments, potential vulnerabilities can be discovered and fixed in advance.
This is an important way to prevent attacks before they actually happen.
Rapid response
With real-time monitoring, you can respond immediately if something goes wrong.
This minimizes the impact of security incidents and enables faster recovery.
Comprehensive security management
Website security assessment and monitoring gives you comprehensive control over the overall security posture of your website.
This ensures that your security policies are consistent and that you can continuously improve your security levels.
4. Adoption stories
News and media platforms
Validate ad content in real-time and quickly detect ads containing malware.
We've strengthened user data protection from malvertising and the trustworthiness of the ad experience.
Travel booking and hotel management platform
By making visible website resources such as Javascript, Stylesheets, and Images that link to the outside world, we completed trust validation and established guidelines for external links that had been managed indiscriminately.
5. AIONCLOUD Website Protection - WMS
AIONCLOUD WMS is a comprehensive solution that covers all aspects of website security assessment and monitoring.
With features such as scanning for malware infections, certificate forgery monitoring, DNS record forgery monitoring, block list registration monitoring, and web vulnerability diagnostics, you can thoroughly manage the security status of your website and proactively detect and respond to potential threats.
With website security assessment and monitoring services that are just as important as inline real-time traffic defense, businesses can build a safer and more reliable web experience.

Today, we've been talking about AIONCLOUD's Website Protection service, which is essential cybersecurity, not optional.
For more information, please refer to the URL below.
https://www.aioncloud.com/website-protection/


