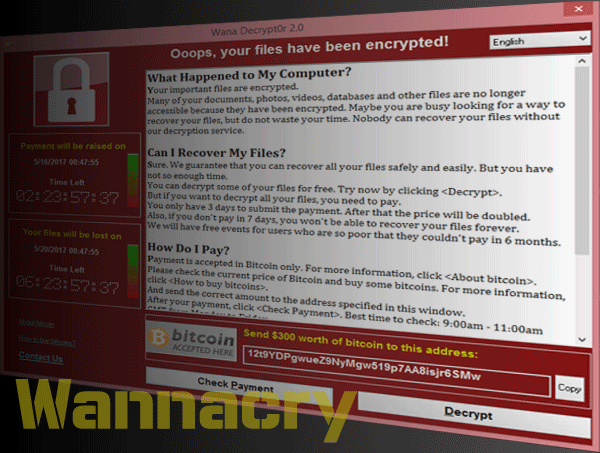
WannaCry ransomware is currently languishing, but the likelihood of a variant attack is still high. As other ransomware other than WannaCry are steadily attacking, fundamental security measures should be prepared. Ransomware primarily penetrates organizations and enterprise through phishing e-mails and it may be spread via media including exploits and other malware. Ransomware runs quickly, with 30,000 files damaged in just four minutes of infection. It spreads from machine to machine over the company network, infects endpoint devices and servers and storage media on the network. If a file is encrypted, no matter how professional, it is impossible to decrypt it without a decryption key. A good way for organizations to prepare for such attacks is to perform regular backups to restore data. However, since data is rarely backed up in real time, it is inevitable that some data will be lost. The first approach to minimizing the success of phishing is to educate users about the provenance of e-mail or website, which is important to know the source information. It is helpful to be aware of the nature of fraudulent emails or websites, and to encourage suspicious or unknown content to report to managers or other experienced staff. It does not completely block users from clicking on malicious URLs, but proper training is a good way to get started. The second stage of protection is to implement email and web gateway technologies to scan known or suspicious URLs. This solution is useful for distinguishing legitimate content from malware or suspicious sites that are not known. The third layer of protection is to install the technology on the endpoint. These technologies usually monitor process behavior and detect activities for ransomware. For example, if a process is continuously encrypting files, it is likely to be ransomware. However, this may also be a normal process used to protect data. In this case, the process can add on Whitelist into a secure process. Here is simply way to secure your website from ransomware. WMD visits your website periodically to diagnose and detects malware and then inform you malware alert to respond for future breach. WMD revisits websites and absolute confidence based on direct observation when suspicious event is founded. WMD provides enhanced inspection depth for multi-level URLs and identifies and inspects malware that have been encoded and obfuscated. WannaCry ransomware attacks are languishing, but variant ransomware and advanced threat is rapidly growing. The enterprises are required to security solution and service for preemptive threat detection and response capacity.


