
Due to the nature of web services, an organization's web servers are always exposed to the outside world, which is why approximately 80% of hacking incidents target web servers.
However, traditional security solutions such as firewalls and Intrusion Prevention Systems (IPS) have clear limitations in today's complex network environments.
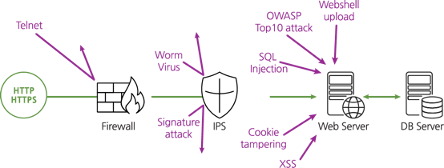
Web servers are required to keep port 80 for HTTP and port 443 for HTTPS open at all times.
This causes the firewall to treat all traffic coming into those ports as normal communication, which increases security risks.
IPS also doesn't provide granular policy settings and is less able to defend against SSL communications due to system load.
In this situation, enterprises have realized the need for a more effective security solution
that allows for more granular security policy settings and is compliant with privacy rules and regulations.
As a result, Web Application Firewall (WAF) has entered the market.
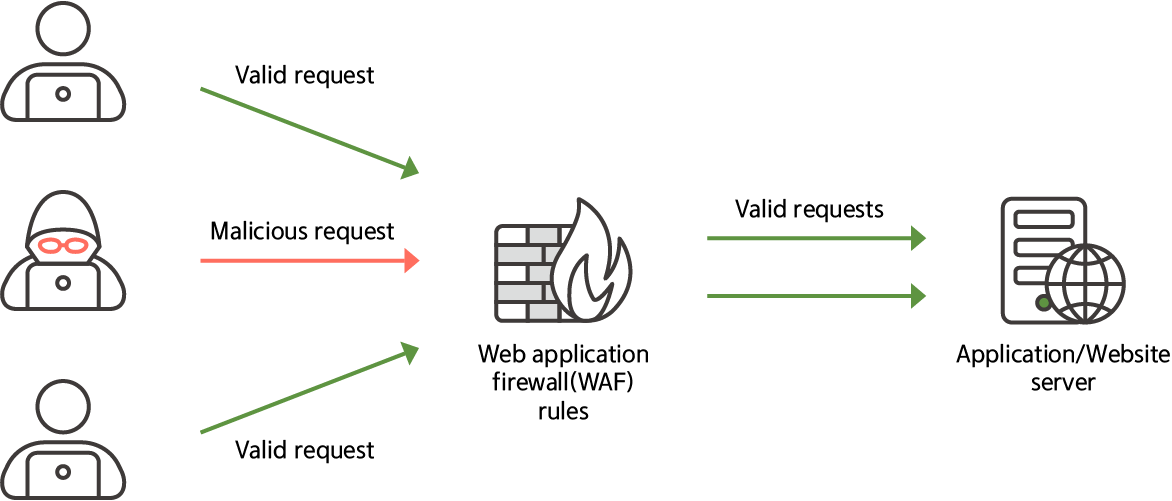
WAF detects and blocks various forms of attacks targeting web applications,
including SQL injection, cross-site scripting (XSS), and command injection.
The WAF has been constantly improving since its appearance.
In the early days, they mainly used blacklists and whitelists,
Since then, we have strengthened policy management according to the type of attack by
utilizing techniques such as web traffic content analysis..
However, with the advancement of technology, web applications have also evolved,
moving away from the single traditional architecture and using microservice architectures.
In other words, the Web Application actually consists of a set of several small services,
and these small services are connected to each other through an API and look like a single application.
Application Programming Interface (API) is a mechanism that enables data exchange between each application.
From simple numerical data to sensitive information is transmitted through API.
With the increasing use of APIs, the focus of web security has extended from simple web applications to API security.
Following these changes, Gartner defined Web Application and API Protection (WAAP).
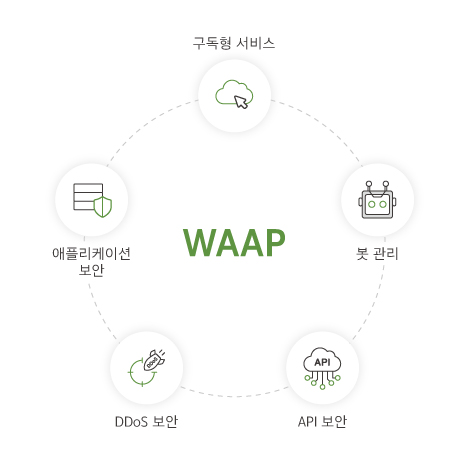
WAAP is a more comprehensive security solution that goes beyond traditional WAF capabilities and includes
API security, bot attack mitigation, DDoS defense, and more.
Today, I'm going to talk about dual API security.
"API Security"
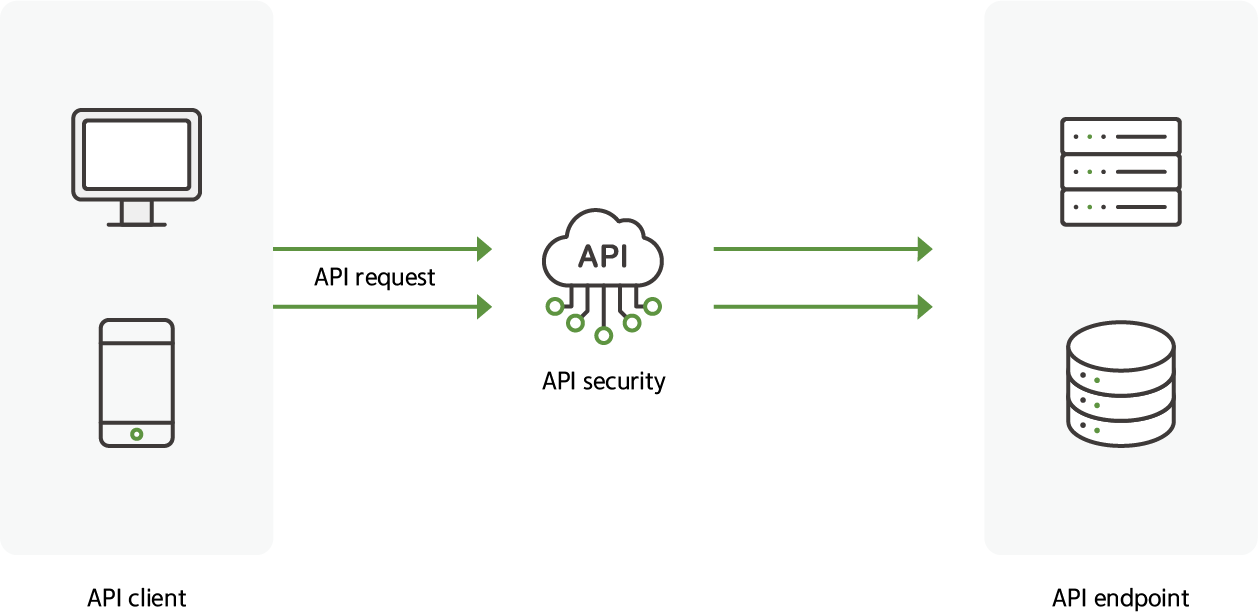
API security is a key component of WAAP, the process of protecting APIs from various forms of attacks.
This requires visibility into API traffic and the ability to establish specific policies for each endpoint.
For example, API Security requires a policy that protects APIs from DDoS attacks and prevents the delivery of incorrect parameter values.
Policies that block access to unauthorized users or applications are also important.
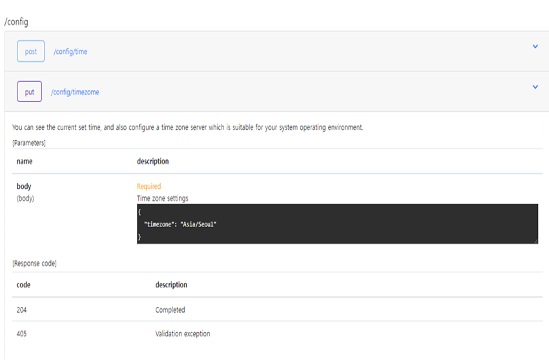
All input data sent to the API must be verified.
Because each API endpoint has a different format of required parameters, misformatted data,
SQL Injection, and XSS attack syntax can cause significant service loss.
Therefore, the value of the data that is always delivered must be verified,
WAAP should not forward the traffic to the web server when incorrectly formatted data is about to be delivered.
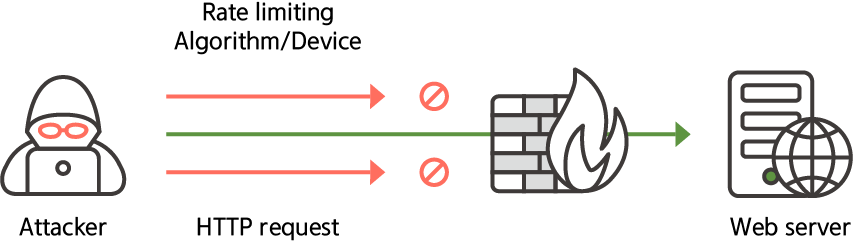
Excessive use of APIs eventually leads to waste of resources.
In particular, malicious traffic growth, such as DDoS attacks, can target APIs.
To manage this excess traffic, WAAP must use methods such as rate limits.
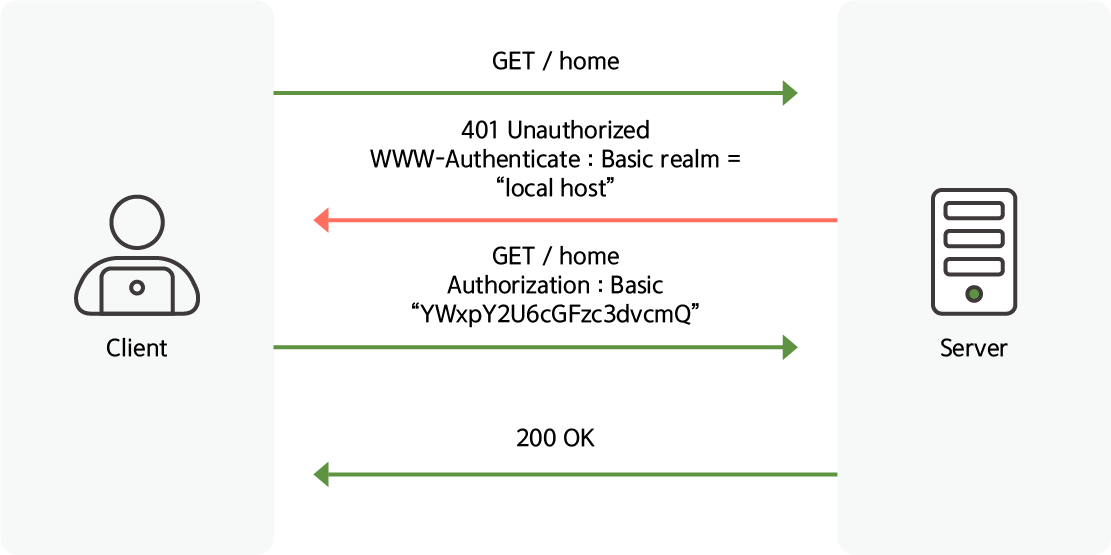
It is also important to block API requests from unauthorized users.
Because the API includes all requests to send and receive data, unauthorized users receiving and sending data can be fatal to the application.
Therefore, API communication should include a specific authentication header value or token,
WAAP must prevent requests that do not have a corresponding value.
Finally, WAAP must monitor usage patterns by separating only API traffic from traffic entering the web server and log to detect unusual activity or suspicious traffic.
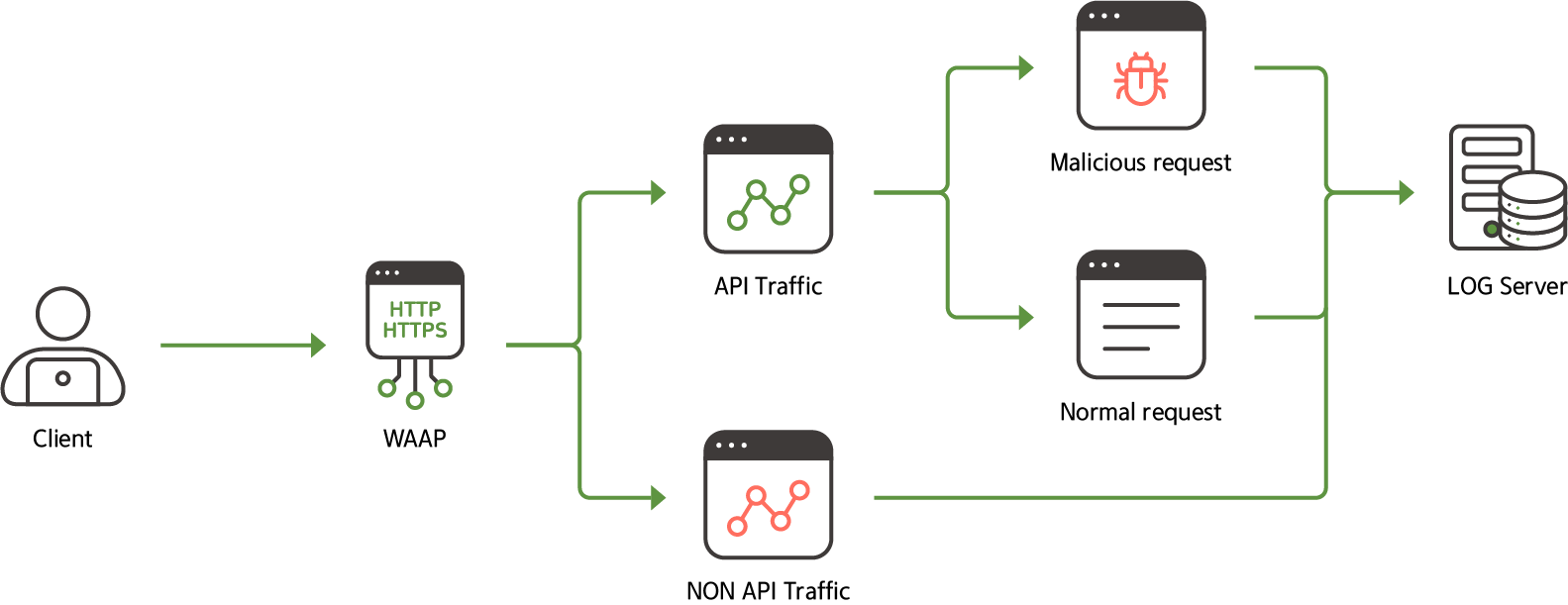
MONITORAPP's AIWAF is a WAAP solution that includes such API security as well as bot attack mitigation, DDoS defense, and more.

MONITORAPP's AIWAF can be implemented using traditional physical appliances installed inside Data Center and Virtual Appliance,
which deploys and configures virtual machines installed in public or private clouds.
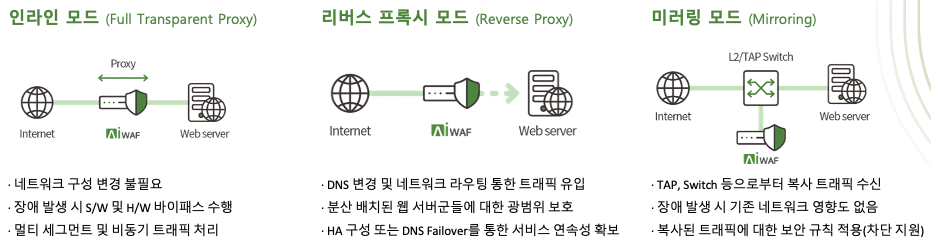
If configured as a physical appliance, it can be configured in 'Inline Mode', 'Reverse Proxy Mode', and 'Mirroring Mode',
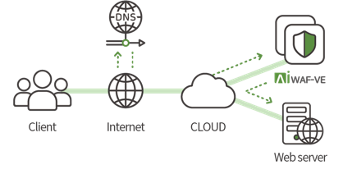
Virtual Appliance can be configured in 'Inline Mode' and 'Reverse Proxy Mode', respectively.
Protect your company's web applications and APIs with MONITORAPP's AIWAF/AIWAF-VE, which supports all deployment/configuration environments.


