
Recently, MONITORAPP has had the opportunity to introduce our newly launched zero trust solutions SIA (Secure Internet Access) and SRA (Secure Remote Access) at various exhibitions and conferences, and also, received inquiries from customers about the architecture of the SSE platform.


Therefore, we would like to share our answers regarding the SSE platform in the FAQ format.
Q: Doesn't speed get slower when going through the SSE platform?
A: This is one of the most asked questions we have received so far.
In general cases, it is totally normal to think that way.
But we can affirm one thing, the AIONCLOUD SSE platform can minimize the speed slowdown problem for the following reasons:

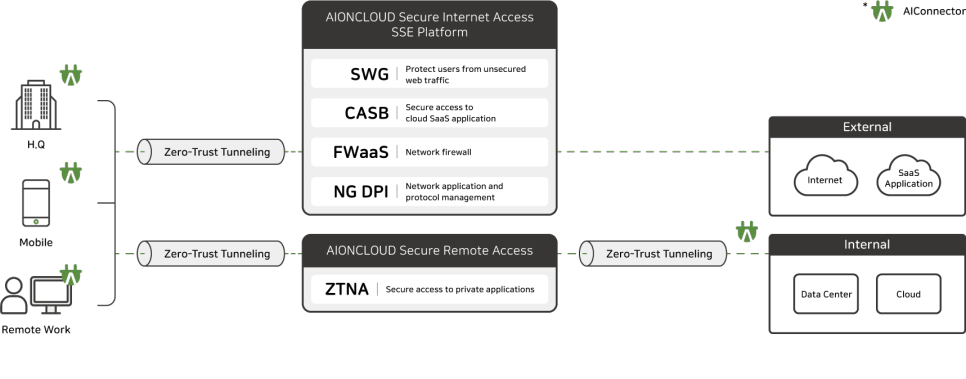
1. By providing services through the SSE edge closest to end users through cloud infrastructure distributed across major networks around the world, including South Korea, network-related speed slowdown issues are minimized.
2. SSE's core security functions, such as SWG, CASB, FWaaS, and NG-DPI, are provided as a single solution developed by MONITORAPP.
Additionally, the validation algorithm has been simplified and optimized so that multiple security features can be enabled without slowing down.
According to Gartner, if you use a combination of various security solutions from different vendors rather than a single vendor, then slowdown issues may frequently occur due to inefficient and redundant check logic.

Q : If we purchase the SSE platform, will it mean that the existing security equipment becomes unusable?
A: Basically, in order to apply AIONCLOUD SSE, you are required to install an agent called AIConnector on all devices.

After installing and authenticating, a separate tunnel will be formed between the device and the SSE edge.
Since this traffic is encrypted, it cannot be detected by network security devices such as IPS, FW, NGGW, and DLP and passed through.
However, security solutions such as PMS, NAC, and anti-virus that are installed and operated on the endpoint can still be used as they are unrelated to traffic tunneling or encryption.
Q : We already had many agents installed. Is there any other way other than installing the agent?
A: Technically speaking, in order to send all traffic to the SSE platform, in addition to installing a separate agent as mentioned above, you can also configure a VPN or GRE tunnel between the office network and the SSE platform.
However, we do not recommend this method as it might lead to several problems, including
(1) the inability to control access traffic from remote workers;
(2) the complicated network settings;
(3) the ability to support a separate protocol of customer’s network equipment, etc.
Also, various endpoint functions such as device posture cannot be used.
Q : What if I am in a situation where I cannot install the agent? (Either due to an old version of the OS or having issues with an outsourced company employee)
A: If installing the agent is not possible, you can consider the app launcher. This is a structure in which, when accessing a separately granted HTTPS website and passing authentication, a list of applications accessible to the user will be displayed, allowing you to access the application by clicking on it. This is why we have explained above that such functions as device posture – which can only verify after installing an agent – cannot be used simultaneously.
Q : If I apply SSE, can I use a fixed source IP such as the IP in the office?
A: Yes. If you would like to, you can allocate several fixed IPs, which can be issued upon separate request.
Q : I am having my legacy internal systems located within the company, and using private IPs. If I apply SSE, the source IP will become a public IP provided by AIONCLOUD. In this case, how can I access my in-house systems?
A: There are 2 methods.
1. You can use a feature called split tunnel. By simply setting the IP address in the manage console, this can be easily set up and applied immediately. Once set, the traffic going to that IP address will not go through tunneling but will be routed and connected directly from the device.
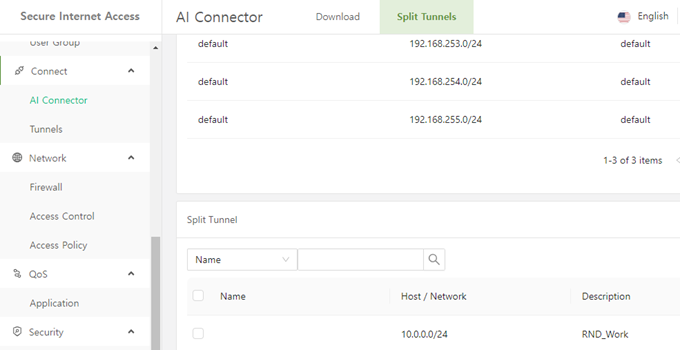
2. Another way (by using SRA) is to configure tunneling by installing a separate agent on each application device.
Q : I heard that ZTNA is “a service that is invisible to attackers”. How is this possible?
A: Imagine, you are accessing a specific server installed in a data center within the company.
The server must have already been assigned with an IP (either public IP or private IP).
In this case, ping can be proceeded if the IP is known through network scanning.
However, when ZTNA (SRA-Secure Remote Access) is used, it will become a different network structure.
In other words, when you install the agent on that server, a separate tunnel with the SSE platform will be automatically configured (a 1:1 independent tunnel is opened between the user and the server).
When you allow access to a specific user (or group) through the SSE console, only the specified user (or group) will be able to see the server information.
Therefore, even if you know the IP, it is meaningless as everything is blocked by default unless you allow it.
Of course, the existing IP previously set is only used for tunneling connection with the SSE platform, so it is necessary to set the appropriate ACL (Access Control List) later.
So far, we have looked at some of the most asked questions regarding the SSE platform.
As the interest in zero trust has increased recently, customer inquiries about the SSE platform are also increasing gradually on our side.
We will prepare and introduce another FAQ blog with more upgraded content soon! See you then!


